Winos4.0 Malware Framework Uses Gaming Apps to Infiltrate Windows Systems

Hackers Deploy Winos4.0 Malware via Game-Related Apps to Target Windows Users
Cybercriminals are increasingly distributing a powerful new malware framework, Winos4.0, by hiding it within seemingly legitimate game-related apps aimed at Windows users. This advanced post-exploitation framework, documented earlier this year by Trend Micro, mirrors popular frameworks like Sliver and Cobalt Strike in its capabilities. Originally used to target Chinese users through bundled software, hackers have now adapted their approach, using popular gaming-related downloads to spread Winos4.0 more widely.
 Malicious files infecting users with Winos4.0
Malicious files infecting users with Winos4.0
Source: Fortinet
How Winos4.0 Lures Victims Through Gaming Apps
The latest campaigns involve malicious actors using games or game-adjacent files as bait. Once the user installs what appears to be a legitimate game or application, Winos4.0 initiates its infection process by downloading a DLL file from a remote server, “ad59t82g[.]com,” and setting up a sophisticated, multi-step attack chain.
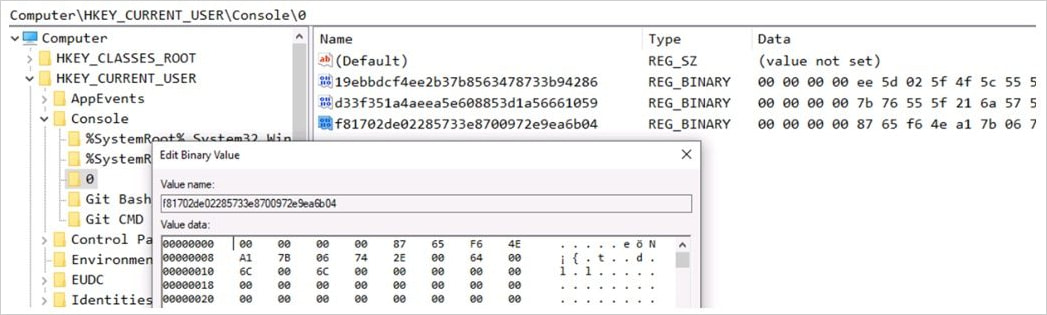 Malware modules added onto the Registry
Malware modules added onto the Registry
Source: Fortinet
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Multi-Stage Infection Process
Stage 1: Establishing Persistence
In the first phase, a downloaded DLL file namedyou.dllruns an initial payload that installs additional components and makes system modifications to ensure persistence. It adds registry entries to execute every time the system starts, ensuring that the malware remains active even after a reboot.Stage 2: Preparing for Command-and-Control
Next, the malware loads shellcode that enables communication with a remote command-and-control (C2) server. This step involves the framework establishing its operational parameters and retrieving configuration data that prepares the system for ongoing communication with attackers.Stage 3: Storing Data and Updating C2 Addresses
During this phase, another DLL (上线模块.dll) is downloaded and executed to retrieve additional, encoded data from the C2 server. This data is stored within the Windows Registry atHKEY_CURRENT_USER\\Console\\0, alongside updates to C2 addresses, ensuring that the malware remains adaptable if the primary C2 server changes.Stage 4: Information Gathering and Exfiltration
The final stage of Winos4.0’s infection chain involves loading a module (登录模块.dll) that performs the primary malicious functions. This module gathers detailed information on the victim’s environment, such as IP address, operating system, CPU details, and information on any installed security software. Additionally, the malware actively monitors clipboard content, takes screenshots, and extracts data from cryptocurrency wallet extensions, exfiltrating the information back to the attackers.
Complete Winos4.0 attack chain
Source: Fortinet
Stealth Tactics and Evasion Techniques
Winos4.0 incorporates several evasion methods, including scanning for the presence of security software like Kaspersky, Avast, Avira, Symantec, Bitdefender, Malwarebytes, McAfee, and ESET. By identifying these processes, the malware determines if it is being monitored and can adjust its behavior accordingly or even terminate its processes to avoid detection.
Trending: Blue Team Tool: Ghostport
Solidifying Winos4.0’s Role in Malicious Operations
For several months, Winos4.0 has been actively deployed in malicious campaigns, indicating its established role in hacking operations. Given its powerful functionality, Winos4.0 provides hackers with an effective tool for complete control over compromised Windows systems. Cybersecurity companies like Fortinet and Trend Micro offer detailed reports, including Indicators of Compromise (IoCs) to help organizations detect and defend against Winos4.0.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com



.jpeg)










