WordPress Sites Hijacked for Widescale Brute Force Campaign

A wave of widescale attacks targeting WordPress sites has emerged, with hackers exploiting vulnerabilities to inject scripts that harness visitors’ browsers for large-scale brute force attacks on other websites.
Initiated by a threat actor previously associated with injecting crypto wallet drainer scripts, this campaign has caught the attention of cybersecurity firm Sucuri. The attacker’s modus operandi involves compromising WordPress sites to inject the AngelDrainer wallet drainer script initially. However, in a recent shift, they’ve redirected their efforts towards coercing visitors’ browsers into launching brute force attacks on other WordPress sites.
Brute force attacks entail repeated login attempts with varied passwords to gain unauthorized access. By compromising WordPress sites, threat actors implant malicious code into HTML templates. Upon visiting these compromised sites, visitors unwittingly load scripts from ‘https://dynamic-linx[.]com/chx.js‘ into their browsers.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
These scripts surreptitiously communicate with the attacker’s server at ‘https://dynamic-linx[.]com/getTask.php,’ receiving tasks in the form of JSON files outlining parameters for the brute force attack. Tasks include website URLs, account names, password batches, and instructions for the browser to upload files containing potential login credentials to the compromised WordPress sites.
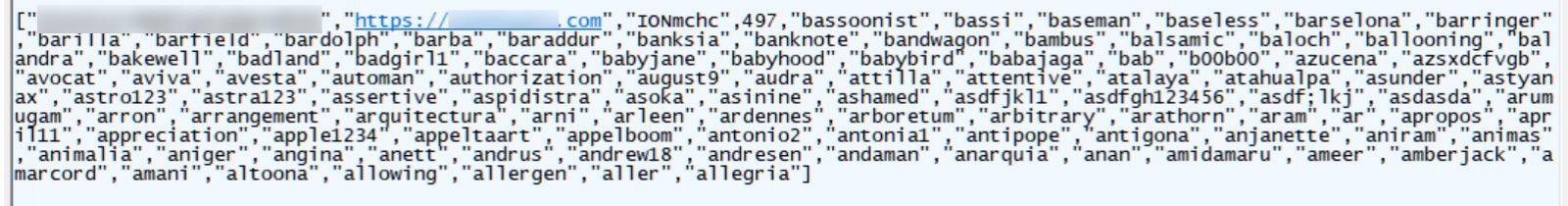 Example bruteforce JSON task
Example bruteforce JSON task
Source: BleepingComputer
After receiving the task, the script initiates a process where the visitor’s browser discreetly uploads a file via the WordPress site’s XMLRPC interface, utilizing the account credentials provided in the JSON data.
Upon successful authentication, the script alerts the malicious actor’s server about the discovered password for the site. Subsequently, the hacker gains access to the site to retrieve the uploaded file, which contains the base64 encoded username and password combination.
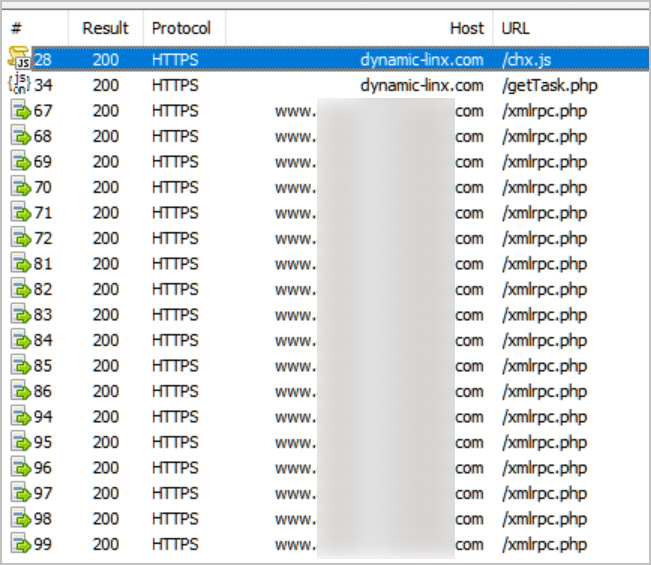 Script causing browser to bruteforce a website’s credentials
Script causing browser to bruteforce a website’s credentials
Source: BleepingComputer
Sucuri’s investigation reveals over 1,700 compromised sites harboring these malicious scripts, indicating a significant threat to WordPress security. Notably, Germán Fernández from CronUp discovered Ecuador’s Association of Private Banks’ website compromised, acting as a vector for unsuspecting visitors.
While the motive behind the shift from crypto wallet drainers to brute force attacks remains unclear, Sucuri suggests the change could be driven by the desire to expand the attacker’s portfolio for future monetization endeavors.
Trending: Offensive Security Tool: Upload_Bypass


