WordPress Websites at Risk – Hackers Exploit Critical Flaw in Essential Addons for Elementor

Hackers have launched a widespread campaign, targeting vulnerable versions of the Essential Addons for Elementor plugin on thousands of WordPress websites through extensive internet scans. Their objective is to exploit a critical account password reset flaw that was recently disclosed.
Tracked as CVE-2023-32243, this critical-severity vulnerability affects Essential Addons for Elementor versions 5.4.0 to 5.7.1. Exploiting this flaw allows unauthenticated attackers to reset administrator account passwords and gain control of targeted websites.
PatchStack, a security company, discovered the flaw on May 8th, 2023, and promptly alerted the plugin vendor. The vendor swiftly addressed the issue and released version 5.7.2 on May 11th to fix the vulnerability.
PoC
The scale of the exploitation remained uncertain until recently. On May 14th, researchers made a proof-of-concept (PoC) exploit available on GitHub, exposing attackers to a widely accessible tool for carrying out the attacks.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Reports surfaced of a BleepingComputer reader and website owner who fell victim to hackers exploiting the flaw by resetting their admin password. However, it was still unclear how extensively this flaw was being exploited.
A recent report by Wordfence sheds light on the matter, revealing that millions of probing attempts have occurred to identify websites vulnerable to this plugin. Wordfence successfully blocked over 6,900 exploitation attempts.
Just a day after the flaw’s disclosure, Wordfence recorded a staggering five million probing scans specifically targeting the plugin’s ‘readme.txt’ file, which contains version information crucial for identifying vulnerable sites.
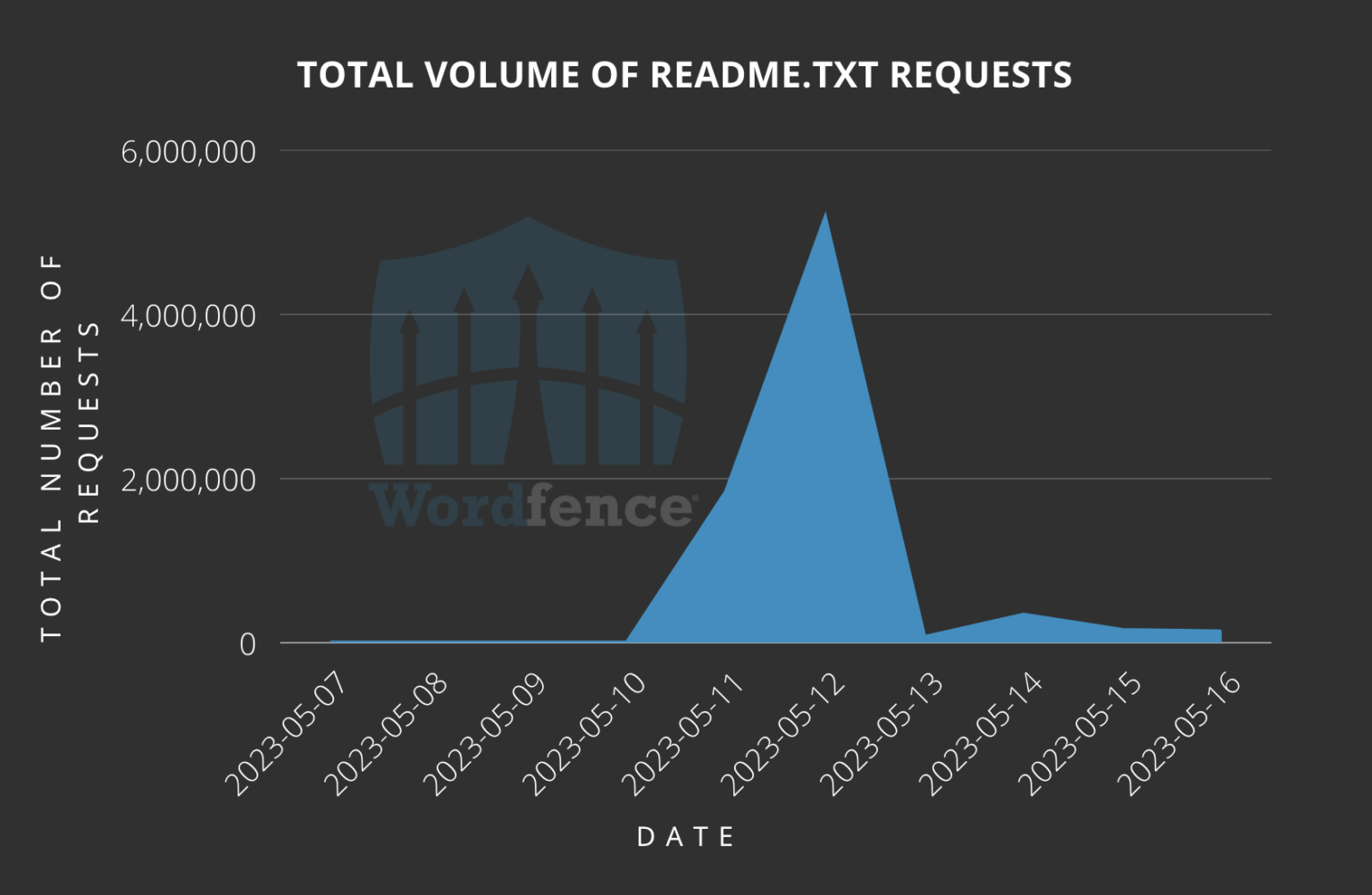 Number of recorded daily scans (Wordfence)
Number of recorded daily scans (Wordfence)
“While some services perform legitimate installation data probes, our data suggests that attackers began targeting vulnerable sites immediately after the flaw was disclosed,” commented Wordfence in their report.
Trending: OSINT Tool: GooFuzz
The majority of these probing attempts originated from two IP addresses: ‘185.496.220.26’ and ‘185.244.175.65.’ When it comes to exploitation attempts, one IP address, ‘78.128.60.112,’ accounted for a substantial volume of attacks by leveraging the PoC exploit released on GitHub. Several other high-ranking attacking IPs made between 100 and 500 attempts each.
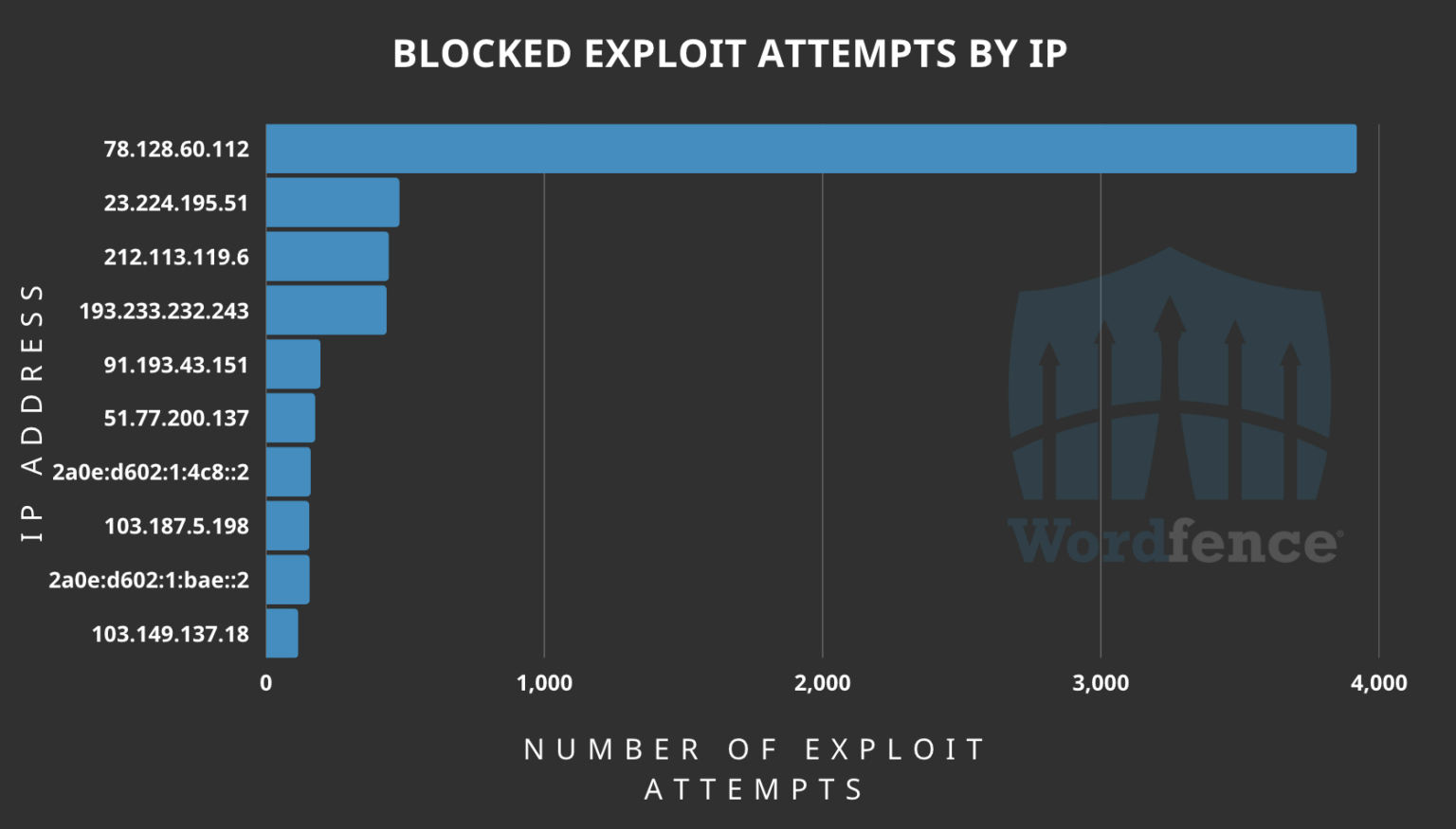 Origin of most exploitation attempts (Wordfence)
Origin of most exploitation attempts (Wordfence)
To safeguard their websites, owners who utilize the ‘Essential Addons for Elementor’ plugin are strongly advised to update to version 5.7.2 or newer immediately. Given the vulnerability’s high exploitability, Wordfence emphasizes the urgency of this update to prevent site compromise.
Additionally, website administrators should review the indicators of compromise outlined in Wordfence’s report and add the identified malicious IP addresses to their blocklist to mitigate current and future attacks.
While users of Wordfence’s free security package are currently exposed to CVE-2023-32243, they can expect protection against this vulnerability on June 20, 2023.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













