XLoader macOS Malware Resurfaces as ‘OfficeNote’ App, Evading Detection with New Tactics
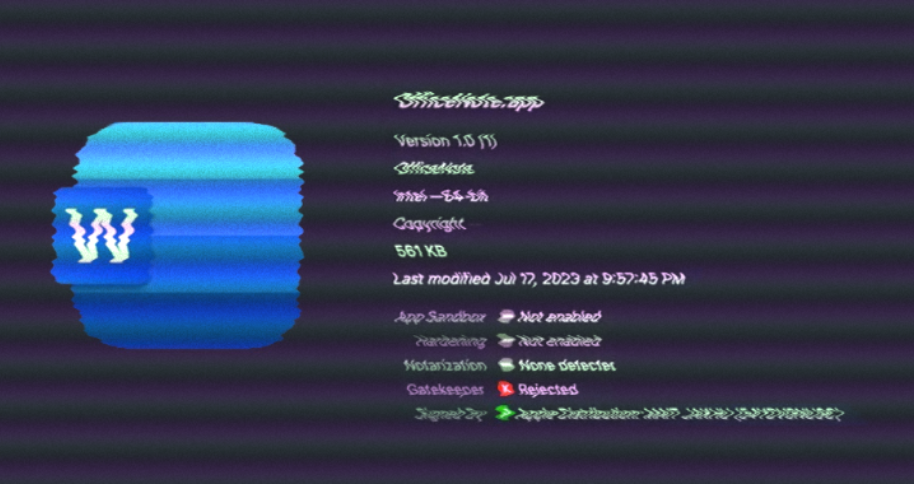
A fresh variant of the notorious Apple macOS malware, XLoader, has emerged, adopting the guise of an innocuous office productivity application named “OfficeNote.” This evolving malware strain has hidden its malicious capabilities behind the facade of a seemingly legitimate app.
Security researchers at SentinelOne revealed in a recent analysis that the new version of XLoader is concealed within an Apple disk image named “OfficeNote.dmg.” The contained application is signed with the developer’s signature “MAIT JAKHU (54YDV8NU9C).”
Originating in 2020, XLoader, considered a successor to Formbook, operates as an information stealer and keylogger. It is offered as part of the malware-as-a-service (MaaS) model. In July 2021, a macOS variation of the malware emerged, distributed in the form of a Java program within a compiled .JAR file.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The preceding macOS version encountered a roadblock, as it required the Java Runtime Environment to function. Given that Apple ceased shipping JRE with Macs over a decade ago, the malicious .jar file could not execute on standard macOS installations.
The latest iteration of XLoader has circumvented this limitation by transitioning to programming languages like C and Objective C. The disk image file, signed on July 17, 2023, obtained a now-revoked signature from Apple.
SentinelOne researchers noted multiple VirusTotal submissions of this artifact throughout July 2023, indicating a broad-reaching campaign.
Advertisements on underground forums dedicated to cybercriminal activities are offering the Mac version of XLoader for rent at a relatively high price point: $199 per month or $299 for three months. This cost disparity is intriguing, as Windows variants of XLoader are priced at $59 per month or $129 for three months.
Trending: Recon Tool: RecoX
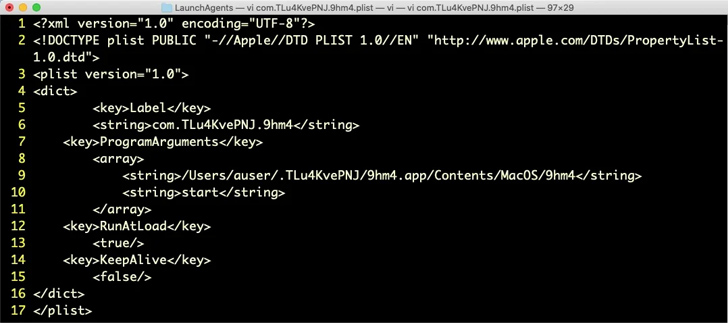
Upon execution, the OfficeNote application ostensibly displays an error message stating that it “can’t be opened because the original item can’t be found.” In reality, it discreetly installs a Launch Agent in the background, ensuring its persistence on the system.
It’s worth highlighting that vigilance in avoiding suspicious apps and regularly updating security software is crucial to protecting macOS devices from evolving threats like XLoader’s deceptive variants.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












