Zero-Click Takeover Alert – Thousands of Internet-Exposed GitLab Instances at High Risk

More than 5,300 GitLab instances exposed on the internet are grappling with a severe security vulnerability, CVE-2023-7028, which GitLab itself had issued a warning about earlier this month.
This critical flaw, carrying a CVSS score of 10.0, opens the door for attackers to execute a zero-click account takeover. The exploit allows threat actors to redirect password reset emails to an email address under their control, ultimately enabling them to change the account password and gain unauthorized access.
Despite not bypassing two-factor authentication (2FA), this vulnerability poses a significant risk to accounts lacking this additional layer of security. The affected versions include GitLab Community and Enterprise Editions ranging from 16.1 to 16.7, with fixes provided in the latest releases.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Despite GitLab’s response and the release of security updates on January 11, 2024, a recent report from ShadowServer indicates that 5,379 vulnerable GitLab instances remain exposed online. Given GitLab’s crucial role as a software development and project planning platform, the severity of the flaw puts these servers at risk of supply chain attacks, proprietary code exposure, API key leaks, and other malicious activities.
The majority of these vulnerable servers are identified in the United States, followed by Germany, Russia, China, France, the U.K., India, and Canada. GitLab emphasizes the urgency for administrators to follow the incident response guide, check for signs of compromise, and take immediate action.
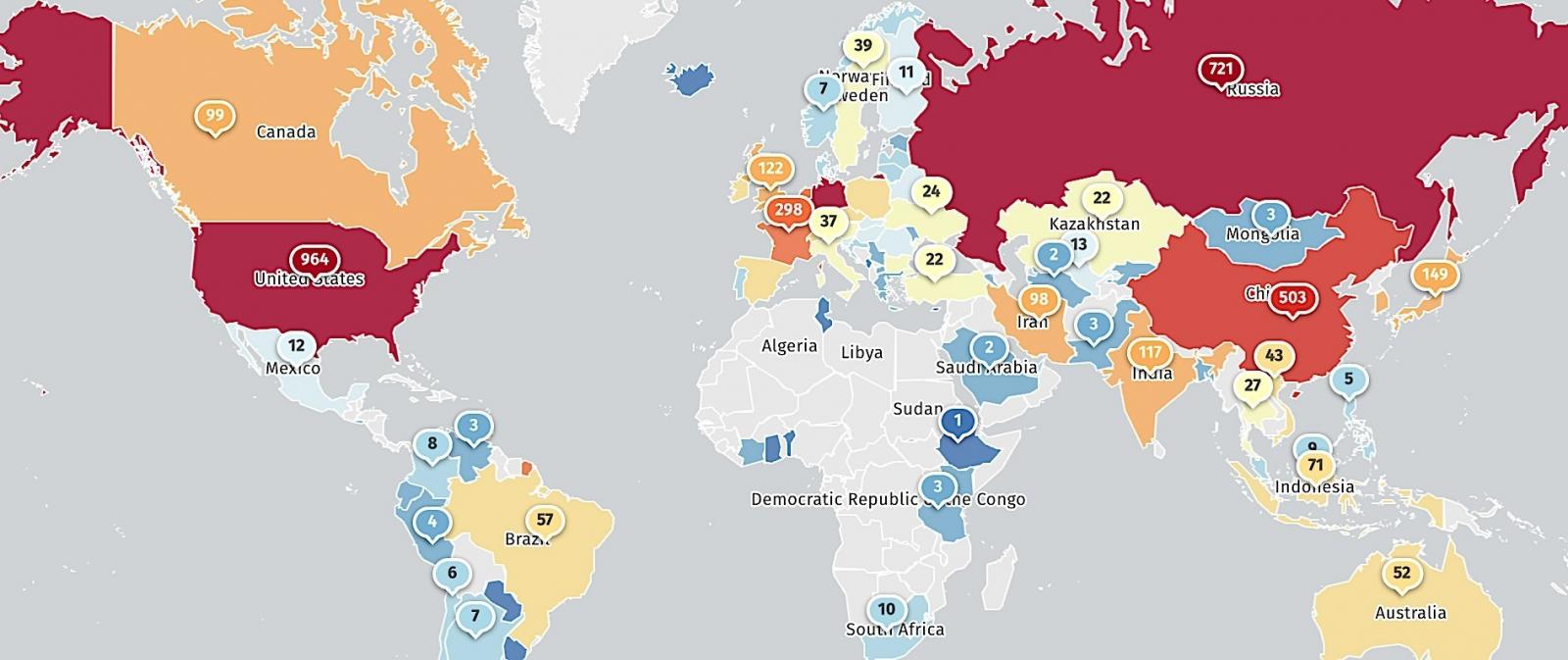 Location of vulnerable GitLab instances (Shadowserver)
Location of vulnerable GitLab instances (Shadowserver)
Trending: Jeff Foley – OWASP Amass Founder
Trending: OSINT Tool: apk2url
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













