Red Teaming Tool: avred

Reading Time: 3 Minutes
avred
avred developed by , is a tool designed for Red Teamers to identify and analyze how antivirus (AV) software detects malware. It scans files to determine which specific parts trigger AV detection, providing detailed information to help evade or obfuscate these detections. It can be useful when Red Teamers simulate attacks to test defenses, as it reveals weaknesses and patterns that AV software relies on.
This includes:
- Section names of matches
- Verification of matches
- Augmentation of matches as disassembled code or data references
It is mainly used to make it easier for Red Teamers to obfuscate their tools.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Background
Most antivirus engines rely on strings or other bytes sequences to recognize malware. This project helps to automatically recover these signatures (matches).
The difference to similar projects is:
- Knowledge of internal file structures.
- Can extract vbaProject.bin and modify it
- Knows about PE sections and scan each one individually
- Knows .NET streams
- Supports any Antivirus (thanks to AMSI server via HTTP)
- Shows detailed information about each match (disassembly etc.)
- Verifies the matches
Supported Files
- PE (EXE) files, r2 disassembly
- PE .NET files, dncil disassembly
- Word files, pcodedmp disassembly
Example
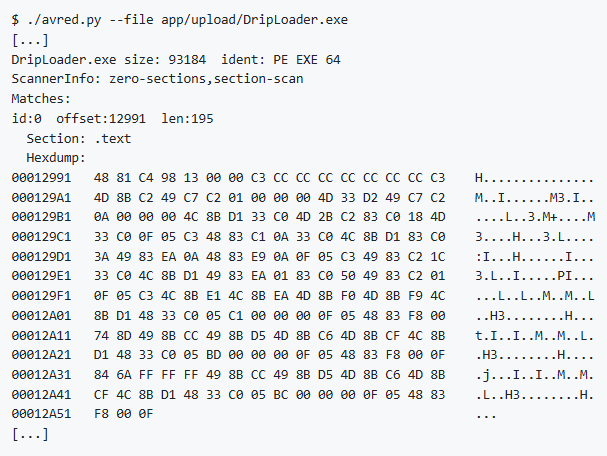
Upgrades
Note: Data is stored in pickled .outcome files. When the author change the model, weird things gonna happen.
Usually this will solve it:
$ rm app/upload/*.outcome; rm app/upload/*.log
$ for i in app/upload/*; do ./avred.py --file "$i"; done
With hashcache enabled, this should be quick.
Install
Requires: python 3.8
Install python deps:
pip3 install --upgrade -r requirements.txt
If you get the error ImportError: failed to find libmagic. Check your installation try:
pip3 install python-magic-bin==0.4.14
Install radare2:
- follow instructions on radare2 github
- Or download exe from github releases and add to your PATH (e.g. on windows)
Note: Make sure you have dnfile >= 0.14.1 installed
Setup
First, we need a windows instance with an antivirus. We use avred-server as interface to this antivirus on a Windows host.
Lets install and configure avred-server on windows VM 1.1.1.1:9001. Follow install instructions on avred-server README.
Once you have this and its working properly (use curl 1.1.1.1:9001/test), you can setup avred:
- Configure your server IP in config.yaml (eg “amsi”: “1.1.1.1:9001”)
- Test it by scanning a file with: ./avred.py –file test.ps1 –server amsi
It should look like this:

How to Use
As a web server:
$ python3 avredweb.py --listenip 127.0.0.1 --listenport 8080
If you dont want that every user is able to see every uploaded file, set password in config.yaml in key password, use username admin.
From command line:
$ python3 avred.py --server amsi --file app/upload/evil.exe
File and Directory structure
I am team NO-DB. Only files.
File nomenclature:
- file.exe: The file you want to scan
- file.exe.log: All log output of the scanning (with –logtofile)
- file.exe.outcome: Pickled Outcome data structure with all further information
- file.exe.pdb: If you have debug symbols
For the webapp, files are uploaded to app/uploads/.
Docker
Build:
$ podman build -t avred .
run:
$ podman run -p 9001:5000 -e "server=http://1.1.1.1:8001" --name avred -d avred
run with upload directory mounted:
$ podman run -p 9001:5000 -e "server=http://1.1.1.1:8001" -v $HOME/avred-uploads:/opt/avred/app/upload/ --name avred -d avred
Tests
Coverage:
python3 -m coverage run -m unittest -> .coverage
python3 -m coverage report -> stdout
python3 -m coverage html -> ./htmlcov/index.html
Clone the repo from here: GitHub Link









