Recon Tool: BF ActiveSub

Reading Time: 3 Minutes
Subdomain Brute-Force The Pure and Fast Programming Way
A Subdomain enumeration tool that supports active attack mode (not passive recon) written by Black Hat Ethical Hacking
What is Subdomain Enumeration/Brute-Force?
Brute force means guessing possible combinations of the target until the expected output is discovered. So, in the subdomain context, the brute-forcing is to try the possible combination of words, alphabets, and numbers before the main domain in order to get a subdomain that is resolved to IP address. Sometimes subdomains are not indexed on search engines and are not available on online DNS aggregators sites in that case brute forcing is the best way to find out the subdomains which may have been forgotten by the organization. It is like a treasure for an adversary.
Our tool has 0 false positives as it verifies it before bringing the result, and is focused on active scanning rather than passive.
It will resolve if the Host is Alive and Output the Results after bruteforcing using Pipe for Speed – Bounty Quick Technique
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
About this Tool
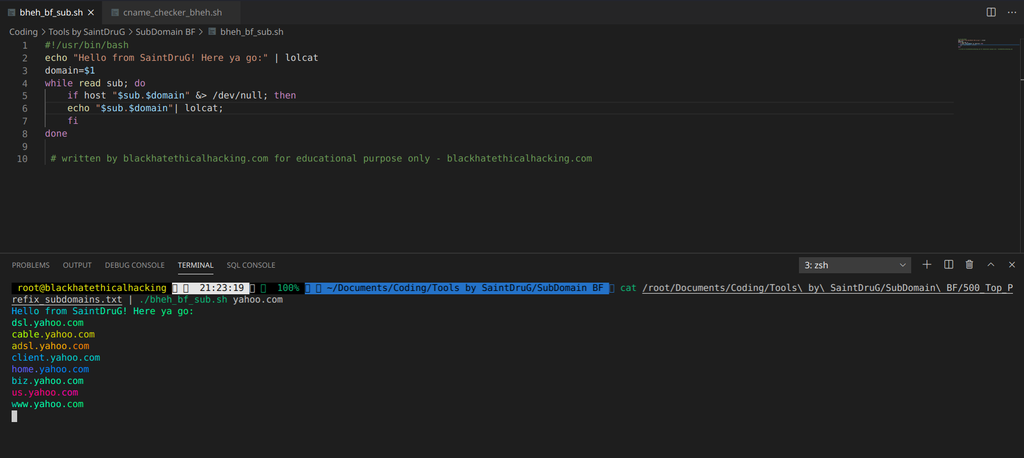
BF ActiveSub is a tool written by us in Bash. It was written for internal use to find more subdomains when performing Recon. ‘host’ is a Linux command that resolves a host if it’s alive by providing it with an IP. After brute-forcing it from a wordlist provided, that checks prefixes of 500/5000 top combinations. The way it’s written as we know stdin and stderr can be controlled, so we redirect it to &> /dev/null; which in the terminal world, it’s like black hole, and then after resolving if it exists, outputs the result in your terminal, or save it to a new list.
This is an Active Recon scan, and not Passive.
Pure BF, and allows you to get even more targets when you are performing Bug Bounty or Pentesting and you know you want to be different from just getting the same results everyone gets, using the same default tools and configs that will maximize your potential bounty, since you will have more subdomains to work with than others, and speed is very important in such action.
Installation
- Requirements:
apt-get install lolcat
apt-get install figlet
- Installation
git clone https://github.com/blackhatethicalhacking/bf_active_sub.git
cd bf_active_sub
chmod +x bheh_bf_sub.sh
Trending: OSINT Tool: Social Hunter
Instructions and Usage Example
Take a list that we provide, add a domain, and it will bruteforce it
Basically, using the below examples, you can perform in various one-liners since it supports piping as follows:
- Usage Example With Output in your Terminal:
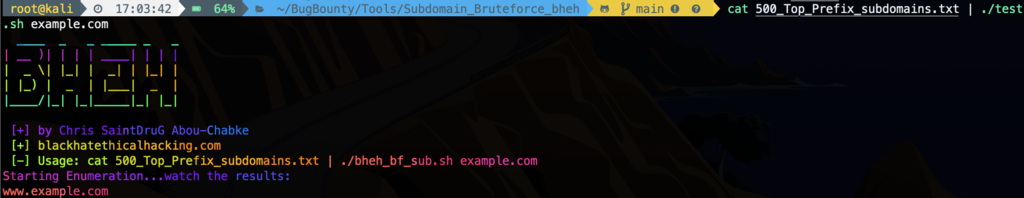
cat 500_Top_Prefix_subdomains.txt | ./bheh_bf_sub.sh example.com
cat 5000_Top_Prefix_subdomains.txt | ./bheh_bf_sub.sh example.com
- Usage Example With Output Saved in a new File:
cat 500_Top_Prefix_subdomains.txt | ./bheh_bf_sub.sh example.com > resolved_domains.txt
cat 5000_Top_Prefix_subdomains.txt | ./bheh_bf_sub.sh example.com > resolved_domains.txt
If you want to save the results, then simply add: > results.txt after your one-liner.
i.e: cat 500_Top_Prefix_subdomains.txt | ./bheh_bf_sub.sh example.com > resolved_domains.txt > results.txt
Disclaimer
This tool is provided for educational and research purpose only. The author of this project are no way responsible for any misuse of this tool. We use it to test under NDA agreements with clients and their consents for Pentesting purposes and we never encourage to misuse or take responsibility for any damage caused!
Clone the repo from here: GitHub Link