OSINT Tool: Blackbird
Reading Time: 3 Minutes
Blackbird
Blackbird by p1ngul1n0, is an OSINT (Open-source intelligence) tool to search fast for accounts by username across 153 sites. When performing Pentesting, and Social Engineering attacks, this recon step is very crucial when you want to conduct targeted attacks, and find active profiles on various social media sites, so you can tweak the approach and maximize the outcome of that attack. The name of the tool is based on the Lockheed SR-71 “Blackbird” a long range, high-altitude, Mach 3+ strategic reconnaissance aircraft developed and manufactured by the American aerospace company Lockheed Corporation.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
Setup
Clone the repository
git clone https://github.com/p1ngul1n0/blackbird
cd blackbird
Install requirements
pip install -r requirements.txt
Trending: Offensive Security Tool: Offensive-Azure
Usage
Search by username
python blackbird.py -u username
Run WebServer
python blackbird.py --web
Access http://127.0.0.1:9797 on the browser
Read results file
python blackbird.py -f username.json
List supported sites
python blackbird.py --list-sites
Use proxy
python blackbird.py -u crash --proxy http://127.0.0.1:8080
Show all results
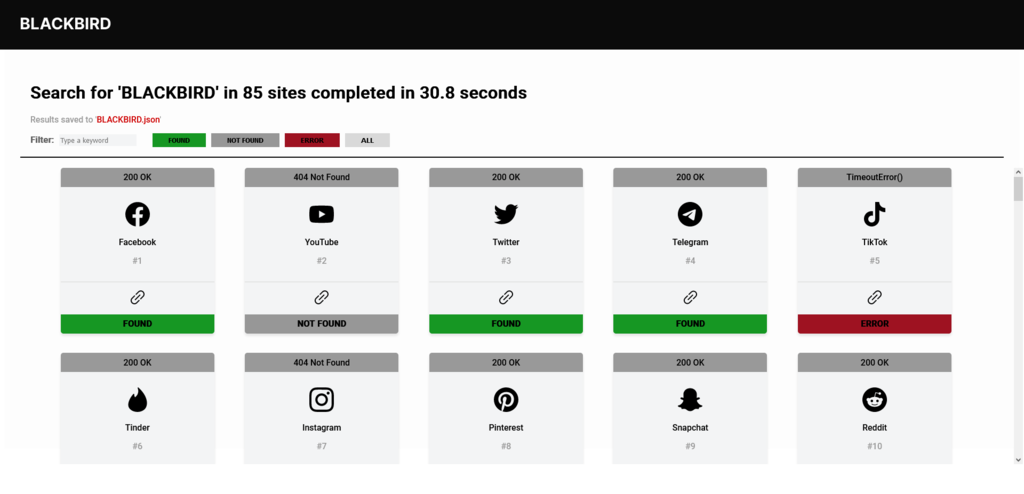
By default only found accounts will be shown, however you can use the argument below to see them.
python blackbird.py -u crash --show-all
Supported Social Networks
It is up to you for how you wish to use this toolkit. Each module can be ran independently, or you can install it as a package and use it in that way. Each module is exported to a script named the same as the module file. For example:
- YouTube
- Telegram
- TikTok
- Tinder
- Snapchat
- Soundcloud
- Github
- Steam
- Linktree
- Xbox Gamertag
- Twitter Archived
- Xvideos
- PornHub
- Xhamster
- Periscope
- Ask FM
- Vimeo
- Twitch
- Pastebin
- WordPress Profile
- WordPress Site
- AllMyLinks
- Buzzfeed
- JsFiddle
- Sourceforge
- Kickstarter
- Smule
- Blogspot
- Tradingview
- Internet Archive
- Alura
- Behance
- MySpace
- Disqus
- Slideshare
- Rumble
- Ebay
- RedBubble
- Kik
- Roblox
- Armor Games
- Fortnite Tracker
- Duolingo
- Chess
- Shopify
- Untappd
- Last FM
- Cash APP
- Imgur
- Trello
- Minecraft
- Patreon
- DockerHub
- Kongregate
- Vine
- Gamespot
- Shutterstock
- Chaturbate
- ProtonMail
- TripAdvisor
- RapidAPI
- HackTheBox
- Wikipedia
- Buymeacoffe
- Arduino
- League of Legends Tracker
- Lego Ideas
- Fiverr
- Redtube
- Dribble
- Packet Storm Security
- Ello
- Medium
- Hackaday
- Keybase
- HackerOne
- BugCrowd
- OneCompiler
- TryHackMe
- Lyrics Training
- Expo
- RAWG
- Coroflot
- Cloudflare
- Wattpad
- Mixlr
- ImageShack
- Freelancer
- Dev To
- BitBucket
- Ko Fi
- Flickr
- HackerEarth
- Spotify
- Snapchat Stories
- Audio Jungle
- Avid Community
- Bandlab
- Carrd
- CastingCallClub
- Coderwall
- Codewars
- F3
- Gab
- Issuu
- Steemit
- Venmo
- MODDB
- COLOURlovers
- Scheme Color
- Roblox Trade
- Aetherhub
- BugBounty
- Huntr
- Universocraft
- Wireclub
- AminoApps
- Trakt
- Giphy
- Minecraft List
- SEOClerks
- Mix
- Codecademy
- Bandcamp
- Poshmark
- hackster
- BodyBuilding
- Mastodon
- IFTTT
- Anime Planet
- Destructoid
- Gitee
- Teknik
- BitChute
- The Tatto Forum
- NPM
- PyPI
- HackenProof
- VKontakte
- about me
- Dissenter
- Designspiration
- Fark
- mmorpg
- Pikabu
- Playstation Network
- Warrior Forum
- Pixilart
Export Report
The results can be exported as a PDF Report.


Export Report
When possible Blackbird will extract the user’s metadata, bringing data such as name, bio, location and profile picture.

Random UserAgent
Blackbird uses a random UserAgent from a list of 1000 UserAgents in each request to prevent blocking.
Supersonic speed
Blackbird sends async HTTP requests, allowing a lot more speed when discovering user accounts.
JSON Template
Blackbird uses JSON as a template to store and read data.
The data.json file store all sites that blackbird verify.
Params
- app – Site name
- url
- valid – Python expression that returns True when user exists
- id – Unique numeric ID
- method – HTTP method
- json – JSON body POST (needs to be escaped, use this: https://codebeautify.org/json-escape-unescape)
- {username} – Username place (URL or Body)
- response.status – HTTP response status
- responseContent – Raw response body
- soup – Beautifulsoup parsed response body
- jsonData – JSON response body
- metadada – a list of objects to be scraped
Examples
GET

POST JSON

GET with Metadata extraction

Disclaimer
This or previous program is for Educational purpose ONLY. Do not use it without permission. The usual disclaimer applies, especially the fact that the author is not liable for any damages caused by direct or indirect use of the information or functionality provided by these programs. The author or any Internet provider bears NO responsibility for content or misuse of these programs or any derivatives thereof. By using these programs you accept the fact that any damage (dataloss, system crash, system compromise, etc.) caused by the use of these programs its your responsibility.
Clone the repo from here: GitHub Link