Offensive Security Tool: Breacher
Reading Time: 2 Minutes
Offensive Security Tool: Breacher
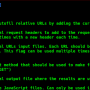
Breacher
Breacher by s0md3v, is a script in order to find admin login pages and EAR vulnerabilities. It works fast by probing with an included path wordlist of 500 known locations, that admin pages could exist. It sends a request to a webpage, supports multi-threading & parses the output on your terminal. It works real fast and also adds the prefixes automatically when testing a specific website URL you give it (http / https), it checks also for Robots.txt and EAR (Execution After Redirect) vulnerabilities which can be exploited for further take overs, known also as CVE-2013-1402. This quickly can find hidden admin login pages, which allows bug bounty hunters, penetration testers and the red team to perform traffic analysis on the login mechanisms, bruteforcing and more.
See Also: GitHub Prepares to Move Beyond Passwords
Features
⦿ Multi-threading on demand
⦿ Big path list (482 paths)
⦿ Supports php, asp and html extensions
⦿ Checks for potential EAR vulnerabilities
⦿ Checks for robots.txt
⦿ Support for custom patns
See Also: Hacking Stories: Xbox Underground
Usages
⦿ Check all paths with php extension
python breacher -u example.com --type php
⦿ Check all paths with php extension with threads
python breacher -u example.com --type php --fast
⦿ Check all paths without threads
python breacher -u example.com
⦿ Adding a custom path. For example if you want all paths to start with /data (example.com/data/…) you can do this:
python breacher -u example.com --path /data
Note: When you specify an extension using –type option, Breacher includes paths of that extension as well as paths with no extensions like /admin/login
See Also: Offensive Security Tool: EyeWitness