Offensive Security Tool: BruteSpray
Reading Time: 2 Minutes
Description
BruteSpray by x90skysn3k, its a tool that automates and accelerates the testing of weak credentials and passwords across multiple services, such as SSH, RDP, and FTP. BruteSpray operates by accepting a target list and a password list, and then efficiently launching brute force attacks against the specified services.
BruteSpray takes Nmap GNMAP/XML output, newline separated JSON, Nexpose XML Export output or Nessus .nessus exports and automatically brute-forces services with default credentials using Medusa. BruteSpray finds non-standard ports, make sure to use -sV with Nmap. It uses Python standard libraries.
See Also: So you want to be a hacker?
Offensive Security Course
Installation
pip install -r requirements.txt
On Kali:
apt-get install brutespray
Usage
If using Nmap, scan with -oG nmap.gnmap or -oX nmap.xml.
If using Nexpose, export the template XML Export.
If using Nessus, export your .nessus file.
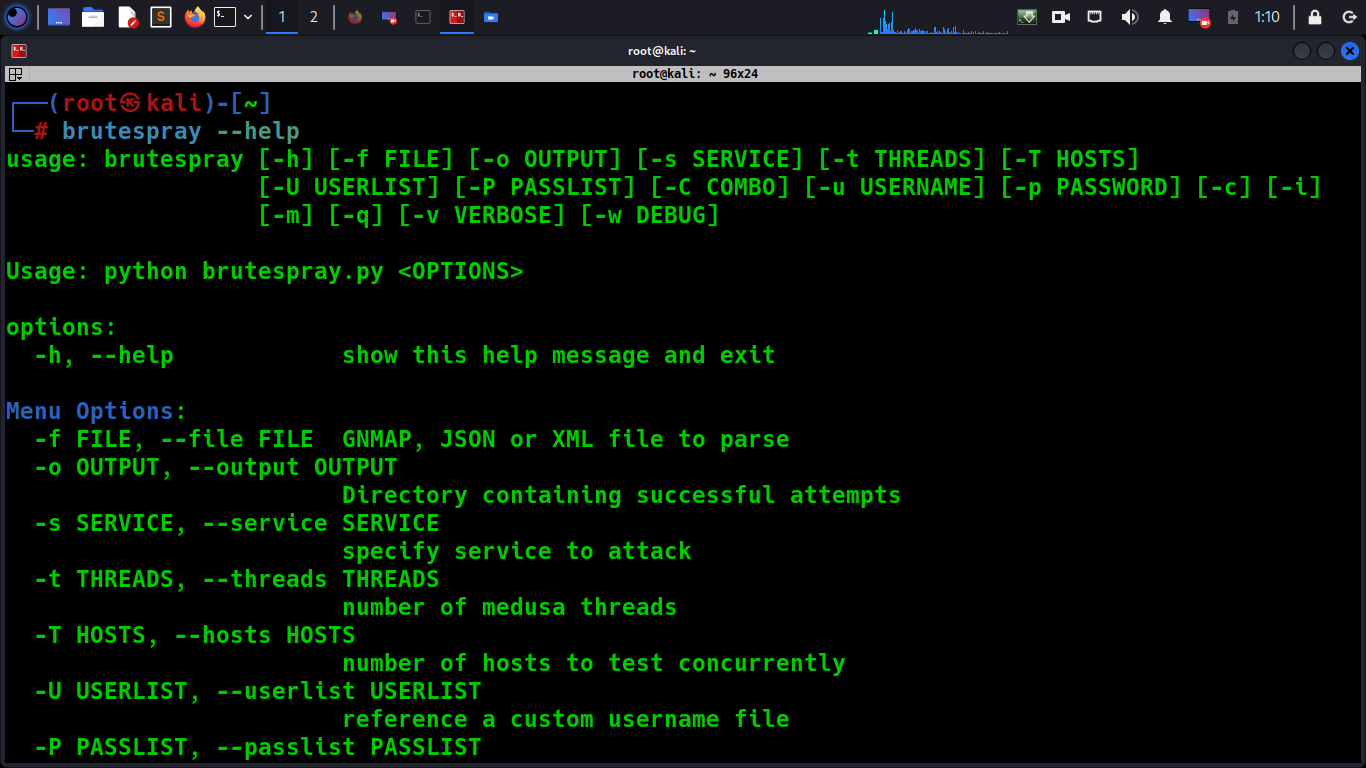
Command: python brutespray.py -h
Command: python brutespray.py --file nmap.gnmap
Command: python brutespray.py --file nmap.xml
Command: python brutespray.py --file nmap.xml -i
See Also: Recon Tool: RecoX
See Also: Offensive Security Tool: Go365
Examples
Using Custom Wordlists:
python brutespray.py --file nmap.gnmap -U /usr/share/wordlist/user.txt -P /usr/share/wordlist/pass.txt --threads 5 --hosts 5
Brute-Forcing Specific Services:
python brutespray.py --file nmap.gnmap --service ftp,ssh,telnet --threads 5 --hosts 5
Specific Credentials:
python brutespray.py --file nmap.gnmap -u admin -p password --threads 5 --hosts 5
Continue After Success:
python brutespray.py --file nmap.gnmap --threads 5 --hosts 5 -c
Use Nmap XML Output
python brutespray.py --file nmap.xml --threads 5 --hosts 5
Use JSON Output
python brutespray.py --file out.json --threads 5 --hosts 5
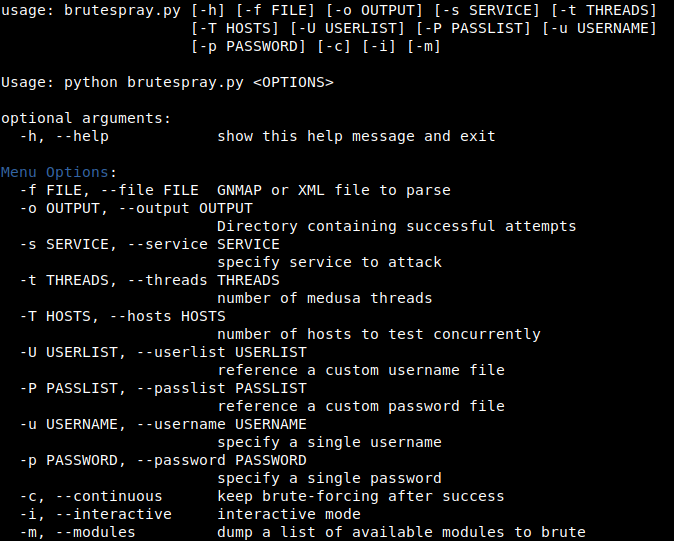
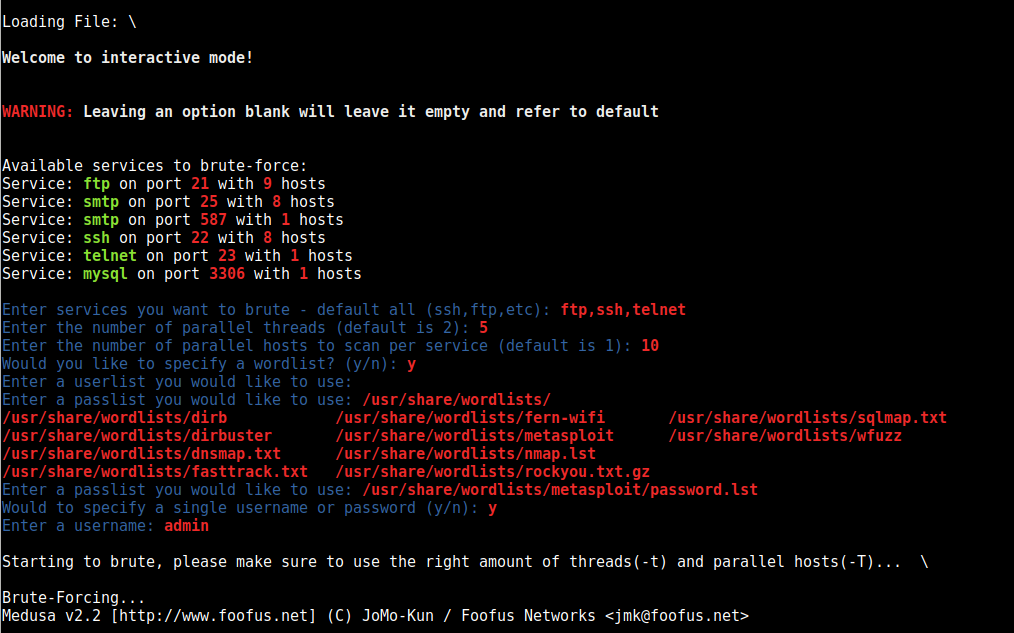
Interactive Mode
python brutespray.py --file nmap.xml -i
Supported Services
- ssh
- ftp
- telnet
- vnc
- mssql
- mysql
- postgresql
- rsh
- imap
- nntp
- pcanywhere
- pop3
- rexec
- rlogin
- smbnt
- smtp
- svn
- vmauthd
- snmp
See Also: Write up: Exploiting LFI Vulnerabilities
Data Specs
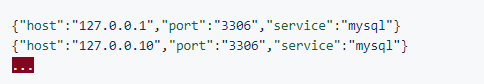
If using Nexpose, export the template XML Export.
If using Nessus, export your .nessus file.
Combo Option
When you specify a combo option -C, it will read the specified file and attempt the host:user:pass on each discovered service from Nmap. If you just want to specify only a username and password leave the host blank as shown below.
:user:pass
:user1:pass1
or
127.0.0.1:user:pass
127.0.0.10:user1:pass1
Demo
Clone the repo from here: GitHub Link









