Recon Tool: CHOMTE.SH
Reading Time: 2 Minutes
Description
CHOMTE.SH by mr-rizwan-syed is a versatile framework designed for automating reconnaissance tasks. It’s useful for bug bounty hunters and penetration testers in both internal and external network engagements. Its key features include subdomain gathering, DNS subdomain brute-forcing, quick port scanning, HTTP probing, service enumeration, and generating reports in various formats. Additionally, it performs content discovery, identifies common misconfigurations and vulnerabilities, conducts deep internet reconnaissance, provides command transparency, and specializes in JavaScript reconnaissance.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Major Features
CHOMTE.SH has the following features:
- Gather Subdomains using subfinder: This feature allows you to gather subdomains using the subfinder tool.
- DNS Subdomain Bruteforcing using dmut: This feature enables DNS subdomain bruteforcing using the dmut tool.
- Quick Port Scan using Naabu: This feature allows for quick port scanning using the Naabu tool.
- HTTP Probing using projectdiscovery HTTPX: This feature allows for HTTP probing using the projectdiscovery HTTPX tool to generate a CSV file.
- Service Enumeration using Nmap: This feature enables service enumeration using Nmap by scanning ports that are only open on the host.
- Nmap Report Format: This feature allows you to generate reports in XML, NMAP, CSV, and HTML (raw and styled) formats.
- Content Discovery Scan: Find sensitive files exposed in Web Applications
- Common Misconfigurations & Vulnerabilities of Infrastructure / Web Applications
- Internet Deep Recon: Shodan / Certificate Transparency
- Command Transparency: You will be able to see the commands that are running and where files are being saved
- JavaScript Reon: Hardcoded credentials / Sensitive Keys / Passwords
- Customizable Flags: Tool arguments can be changed by modifying flags.conf file
Check out the Mindmap
Installation
To install CHOMTE.SH, follow these steps:
- Clone the repository: git clone https://github.com/mr-rizwan-syed/chomtesh
- Change the directory: cd chomtesh
- Switch to root user sudo su
- Make the script executable: chmod +x *.sh
- Run the installation script: ./install.sh
- Run Chomte.sh: ./chomte.sh
See Also: Recon Tool: ReconFTW
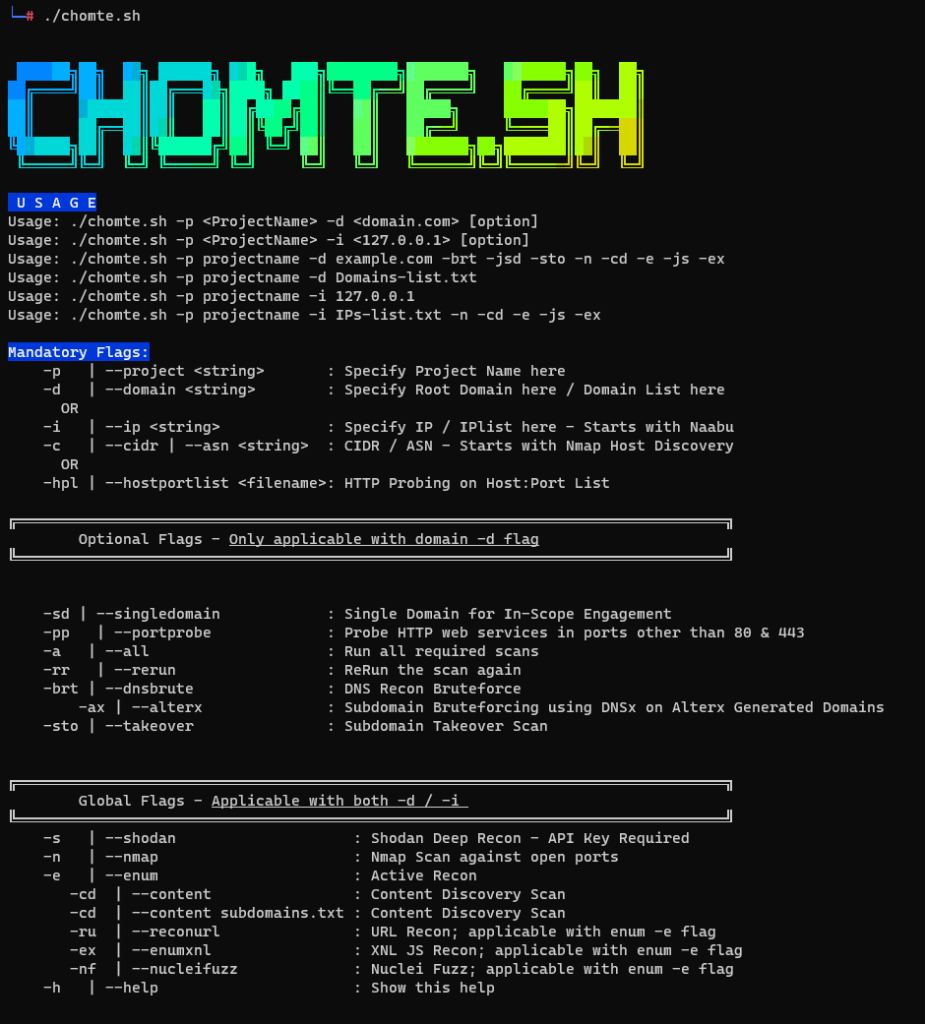
Usage
To use CHOMTE.SH, run the script with the following flags:
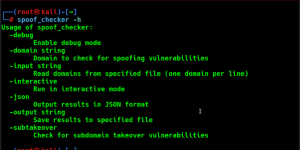
Mandatory Flags
- -p or –project: Specify the project name here.
- -d or –domain: Specify the root domain here or a domain list.
- -i or –ip: Specify the IP/CIDR/IP list here.
Optional Flags
-n or –nmap : Nmap scan against open ports.
-brt or –dnsbrute : DNS Recon Bruteforce.
-hpl or –hostportlist : HTTP Probing on Host:Port List
-cd or –content : Content Discovery – Path is optional
-e or –enum : Active Enum based on technologies
-h or –help : Show help.
Example
Here are some example commands:
| Mode | Commands |
|---|---|
| Gather Subdomains and perform HTTP Probing | ./chomte.sh -p projectname -d example.com |
| Bruteforcing Subdomains with dmut | ./chomte.sh -p projectname -d example.com -brt |
| Perform AlterX Bruteforcing using DNSx | ./chomte.sh -p projectname -d example.com -brt -ax |
| Subdomain Takeover Scan using Subjack and Nuclei | ./chomte.sh -p projectname -d example.com -brt -ax -sto |
| Port Scanning and then HTTP probing on open ports | ./chomte.sh -p projectname -d example.com -pp |
| Nmap Scan on open ports + CSV,HTML Reporting | ./chomte.sh -p projectname -d example.com -pp -n |
| EnumScan: Content Discovery scan on Potential URLs | ./chomte.sh -p projectname -d example.com -e -cd |
| EnumScan: URL Recon Function | ./chomte.sh -p projectname -d example.com -e -ru |
| EnumScan: Nuclei Fuzzer Template Scan on Potential Parameter URLs | ./chomte.sh -p projectname -d example.com -e -ru -nf |
| EnumScan: Run all Enum modules | ./chomte.sh -p projectname -d example.com -e -cd -ru -nf |
| EnumScan: XNL JS Recon and do Trufflehog Secret Scan | ./chomte.sh -p projectname -d example.com -e -ex |
| Perform all applicable Scans | ./chomte.sh -p projectname -d example.com -all |
| Input List of domains in scope | ./chomte.sh -p projectname -d Domains-list.txt |
| Single Domain for in scope engagements | ./chomte.sh -p projectname -d target.com -sd |
| Single IP Scan | ./chomte.sh -p projectname -i 127.0.0.1 |
| CIDR / Subnet Scan | ./chomte.sh -p projectname -i 192.168.10.0/24 |
| Perform Nmap scan on open ports | ./chomte.sh -p projectname -i IPs-list.txt -n |
| Perform host:port http probing & enum | ./chomte.sh -p projectname -hpl hostportlist.txt -e -cd |
Internet Deep Recon
Shodan Recon Setup
cd chomtesh
echo 'SHODAN-API-KEY' > .token
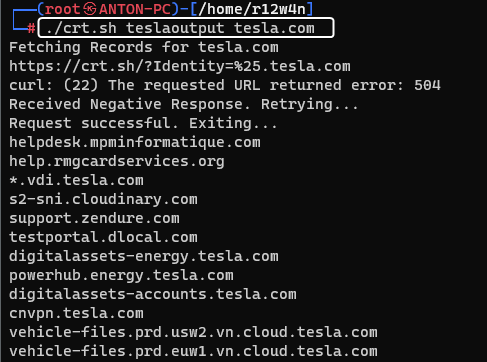
Horizontal Recon – To gather Root / TLD using crt.sh
Here are some example commands:
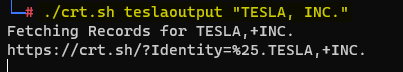
./crt.sh teslaoutput tesla.com
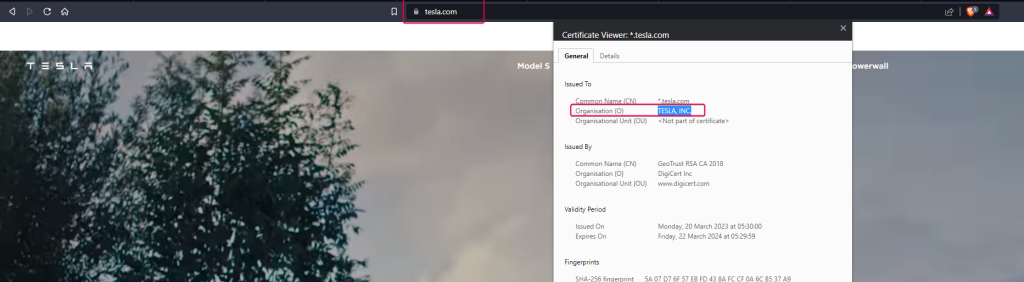
./crt.sh teslaoutput "TESLA, INC."
Customization
CHOMTE.SH allows you to customize the tool flags by editing the flags.conf file.
Add API keys to subfinder ~/.config/subfinder/provider-config.yaml Subfinder API Keys.
Clone the repo from here: GitHub Link