OSINT Tool: cloud_enum
cloud_enum
cloud_enum by initstring, is a multi-cloud OSINT (Open Source Intelligence) enumeration utility designed to help security professionals, penetration testers, and researchers identify and enumerate publicly accessible resources across three major cloud platforms: Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
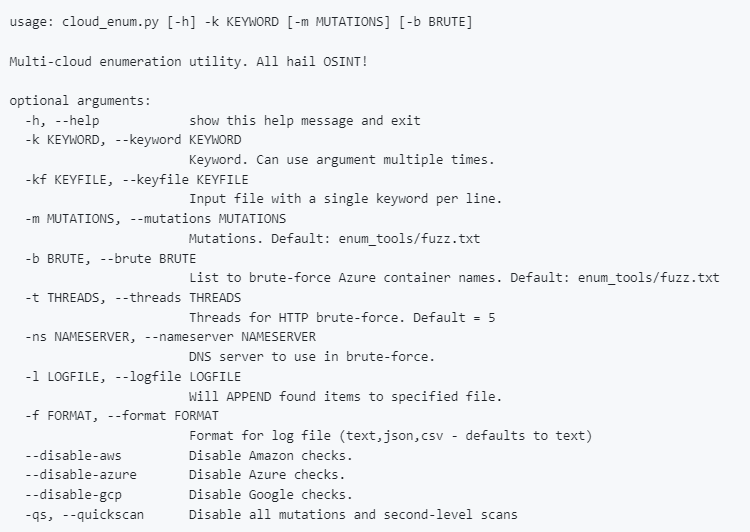
Currently enumerates the following:
Amazon Web Services:
- Open / Protected S3 Buckets
- awsapps (WorkMail, WorkDocs, Connect, etc.)
Microsoft Azure:
- Storage Accounts
- Open Blob Storage Containers
- Hosted Databases
- Virtual Machines
- Web Apps
Google Cloud Platform
- Open / Protected GCP Buckets
- Open / Protected Firebase Realtime Databases
- Google App Engine sites
- Cloud Functions (enumerates project/regions with existing functions, then brute forces actual function names)
- Open Firebase Apps
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Usage
Setup
Several non-standard libaries are required to support threaded HTTP requests and dns lookups. You’ll need to install the requirements as follows:
pip3 install -r ./requirements.txt
Running
The only required argument is at least one keyword. You can use the built-in fuzzing strings, but you will get better results if you supply your own with -m and/or -b.
You can provide multiple keywords by specifying the -k argument multiple times.
Keywords are mutated automatically using strings from enum_tools/fuzz.txt or a file you provide with the -m flag. Services that require a second-level of brute forcing (Azure Containers and GCP Functions) will also use fuzz.txt by default or a file you provide with the -b flag.
Let’s say you were researching “somecompany” whose website is “somecompany.io” that makes a product called “blockchaindoohickey”. You could run the tool like this:
./cloud_enum.py -k somecompany -k somecompany.io -k blockchaindoohickey
HTTP scraping and DNS lookups use 5 threads each by default. You can try increasing this, but eventually the cloud providers will rate limit you. Here is an example to increase to 10.
./cloud_enum.py -k keyword -t 10
See Also: Offensive Security Tool: Nginxpwner
See Also: Deep Dive to Fuzzing for Maximum Impact
Complete Usage Details
Clone the repo from here: GitHub Link









