Offensive Security Tool: CloudFail
Reading Time: 2 Minutes
Offensive Security Tool: CloudFail – Find CloudFlare hidden IP’s
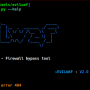
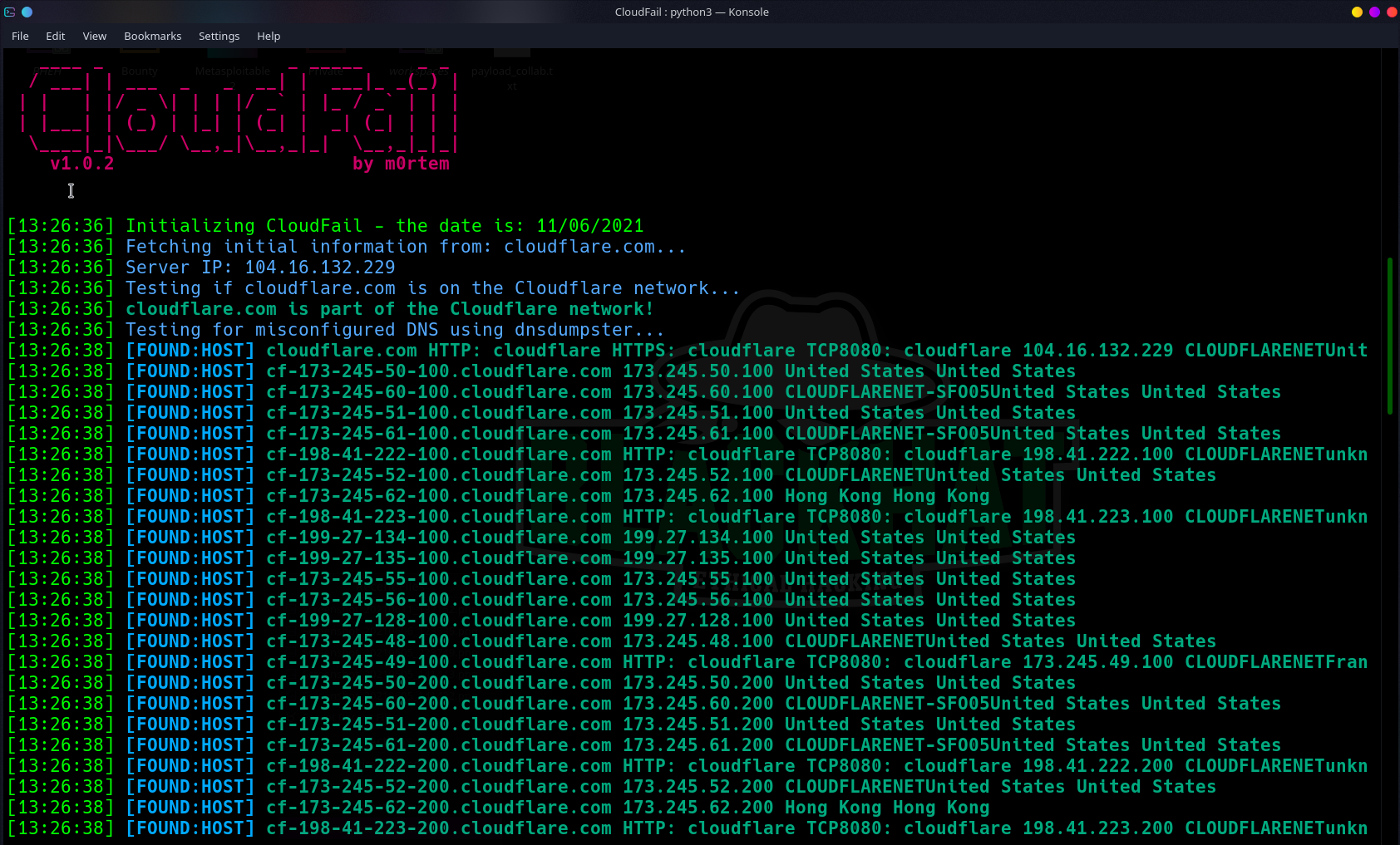
CloudFail by m0rtem, is a tactical reconnaissance tool which aims to gather enough information about a target protected by Cloudflare in the hopes of discovering the location of the server. Using Tor to mask all requests, the tool as of right now has 3 different attack phases.
- Misconfigured DNS scan using DNSDumpster.com.
- Scan the Crimeflare.com database.
- Bruteforce scan over 2500 subdomains.
The way it works is that it utilizes misconfigured DNS and old database records to find hidden IP’s behind the CloudFlare network.
See Also: Offensive Security Tool: Pacu – The Amazon Web Services Exploitation Framework
Disclaimer
This tool is a PoC (Proof of Concept) and does not guarantee results. It is possible to setup Cloudflare properly so that the IP is never released or logged anywhere; this is not often the case and hence why this tool exists. This tool is only for academic purposes and testing under controlled environments. Do not use without obtaining proper authorization from the network owner of the network under testing. The author bears no responsibility for any misuse of the tool.
Install on Kali/Debian
First we need to install pip3 for python3 dependencies:
$ sudo apt-get install python3-pip
Then we can run through dependency checks:
$ pip3 install -r requirements.txt
See Also: Jeff Moss, aka Dark Tangent, the person who founded DEF CON and Black Hat
Usage
To run a scan against a target:
python3 cloudfail.py –target seo.com
To run a scan against a target using Tor:
service tor start
(or if you are using Windows or Mac install vidalia or just run the Tor browser)
python3 cloudfail.py –target seo.com –tor
Note: Please make sure you are running with Python3 and not Python2.*.
Dependencies
Python3
⦿ argparse
⦿ colorama
⦿ socket
⦿ binascii
⦿ datetime
⦿ requests
⦿ win_inet_pton
See Also: Chrome Browser Bug Under Active Attack – Update your chrome now