Offensive Security Tool: Cobalt Strike
Reading Time: 3 Minutes
Offensive Security Tool: Cobalt Strike
What is?
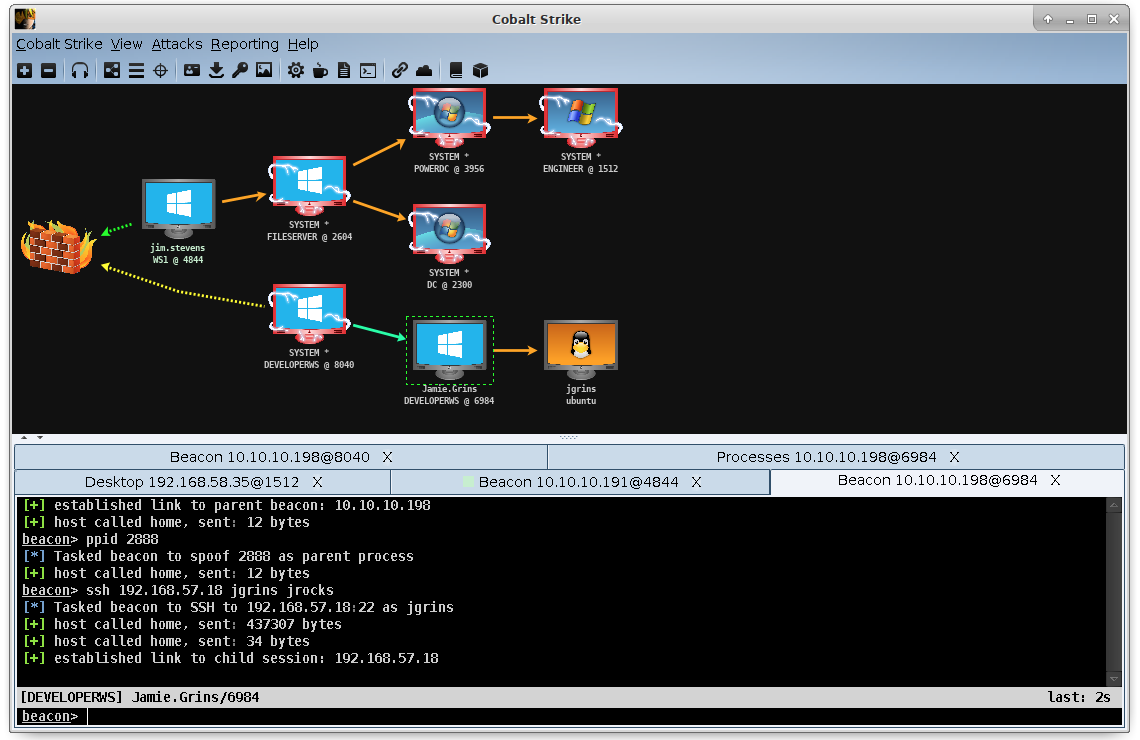
Cobalt Strike is threat emulation software. Execute targeted attacks against modern enterprises with one of the most powerful network attack kits available to penetration testers. This is not compliance testing. Its Software for Adversary Simulations and Red Team Operations.
Everyone has worked with Armitage, this is the more sophisticated version that offers you full GUI capabilities, and instead of Shell/Meterpreter offering Beacon for Connect Back Options giving more reliability.
Features
Reconnaissance
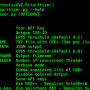
Cobalt Strike’s system profiler discovers which client-side applications your target uses, with version information.
Covert Communication
Beacon’s network indicators are malleable. Load a C2 profile to look like another actor. Use HTTP, HTTPS, and DNS to egress a network. Use named pipes to control Beacons, peer-to-peer, over the SMB protocol.
Spear phishing
Import a message and let Cobalt Strike replace links and text to build a convincing phish for you. Cobalt Strike sends email and tracks who clicks.
See Also: Hacking stories – Rafael Núñez (aka RaFa), hacking NASA with the hacking group: World of Hell
Collaboration
Connect to a Cobalt Strike team server to share data, communicate in real-time, and control systems compromised during the engagement.
Post Exploitation
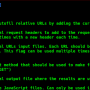
Beacon is Cobalt Strike’s payload to model an advanced actor. Beacon executes PowerShell scripts, logs keystrokes, takes screenshots, downloads files, and spawns other payloads.
Attack Packages
Use Cobalt Strike to host a web drive-by attack or transform an innocent file into a trojan horse.
Browser Pivoting
Use a Browser Pivot to go around two-factor authentication and access sites as your target.
Reporting and Logging
Cobalt Strike’s reports provide a timeline and a list of indicators from red team activity. These reports are made to benefit our peers in security operations. Cobalt Strike exports reports as both PDF and MS Word documents.
See Also: Complete Offensive Security and Ethical Hacking Course