Introduction
Checking administrative interfaces for weak and default credentials is a vital part of every VAPT exercise. But doing it manually can quickly become exhausting.
The problem with web interfaces is that they are all different. And so to develop an universal automation that could do the job across multiple interfaces is very hard.
Although there are some solutions for this, they are mostly commercial and the functionality is not even that great.
Luckily there is a free and open source solution that can help us.
NNdefaccts alternate dataset
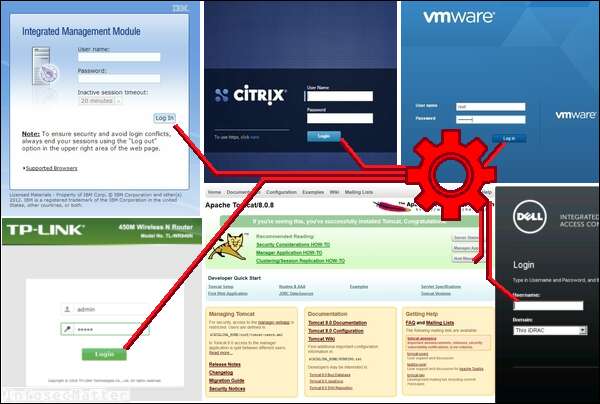
The NNdefaccts dataset made by nnposter is an alternate fingerprint dataset for the Nmap http-default-accounts.nse script.
The NNdefacts dataset can test more than 380 different web interfaces for default logins. For comparison, the latest Nmap 7.80 default dataset only supports 55.
Here are some examples of the supported web interfaces:
Network devices (3Com, Asus, Cisco, D-Link, F5, Nortel..)
Video cameras (AXIS, GeoVision, Hikvision, Sanyo..)
Application servers (Apache Tomcat, JBoss EAP..)
Monitoring software (Cacti, Nagios, OpenNMS..)
Server management (Dell iDRAC, HP iLO..)
Web servers (WebLogic, WebSphere..)
Printers (Kyocera, Sharp, Xerox..)
IP Phones (Cisco, Polycom..)
Citrix, NAS4Free, ManageEngine, VMware..
See the following link for a full list: https://github.com/InfosecMatter/http-default-logins/blob/master/list.txt
The usage is quite simple – we simply run the Nmap script with the alternate dataset as a parameter. Like this:
nmap --script http-default-accounts --script-args http-default-accounts.fingerprintfile=~/http-default-accounts-fingerprints-nndefaccts.lua -p 80 192.168.1.1
This is already pretty great as it is.
Nmap script limitations
Now the only caveat with this solution is that the http-default-accounts.nse script works only for web servers running on common web ports such as tcp/80, tcp/443 or similar.
This is because the script contains the following port rule which matches only common web ports:

So what if we find a web server running on a different port – say tcp/9999? Unfortunately the Nmap script will not run because of the port rule..
..unless we modify the port rule in the Nmap script to match our web server port! And that’s exactly where our new tool comes handy.
Introducing default-http-login-hunter
The default-http-login-hunter tool, written in Bash, is essentially a wrapper around the aforementioned technologies to unlock their full potential and to make things easy for us.
The tool simply takes a URL as an argument:
default-http-login-hunter.sh <URL>
First it will make a local temporary copy of the http-default-accounts.nse script and it will modify the port rule so that it will match the web server port that we provided in the URL.
Then it will run the Nmap command for us and display the output nicely. Here’s an example:

From the above screenshot we can see that we found a default credentials for Apache Tomcat running on port tcp/9999. Now we could deploy a webshell on it and obtain RCE. But that’s another story.
Additional features
List of URLs
The tool also accepts a list of URLs as an input. So for instance, we could feed it with URLs that we extracted from Nessus scan results using our Nessus CSV parser.
The tool will go through all the URLs one by one and check for default logins. Like this:
default-http-login-hunter.sh urls.txt

Here the tool found a default login to the Cisco IronPort running on port https/9443.
Resume-friendly
Another useful feature is that it saves all the results in the current working directory. So if it gets accidentally interrupted, it will just continue where it stopped. Like in this example:

Here we found some Polycom IP phones logins.
Staying up-to-date
To make sure that we have the latest NNdefacts dataset, run the update command:
default-http-login-hunter.sh update
And that’s pretty much it. If you want to see more detailed output, use -v parameter in the command line.
You can find the tool in our InfosecMatter Github repository here.
Fingerprint contribution
I encourage everyone to check out the NNdefacts project and consider contributing with fingerprints that you found during your engagements.
Contribution is not hard – you can simply record the login procedure in the Fiddler, Burp or ZAP and send the session file to the author. Please see more information on the fingerprint contribution here.
You may find these links useful while hunting for default logins manually:
https://cirt.net/passwords
https://www.routerpasswords.com/
Conclusion
This tool can be of a great help not only while performing internal infrastructure penetration tests, but everywhere where we need to test a web interface for default credentials. Its simple design and smart features make it also very easy to use. Hope you will find it useful too!