Offensive Security Tool: DirDar
Reading Time: 2 Minutes
Offensive Security Tool: DirDar
DirDar by M4DM0e, is a tool that searches for (403-Forbidden) directories to break it and get dir listing on it.
DirDar v1.0
bypass forbidden directories – find and identify dir listing – you can use it as directory brute-forcer as well.
Compatibility
This tool is compatible with all kind of operating systems as long as you have GO compiler installed
Install
You can use this command if you have Go installed and configured.
go get -u github.com/m4dm0e/dirdar
Or you can download a release. To make it easier to execute you can put the directory to the binary in your environment variable %PATH%.
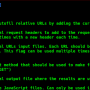
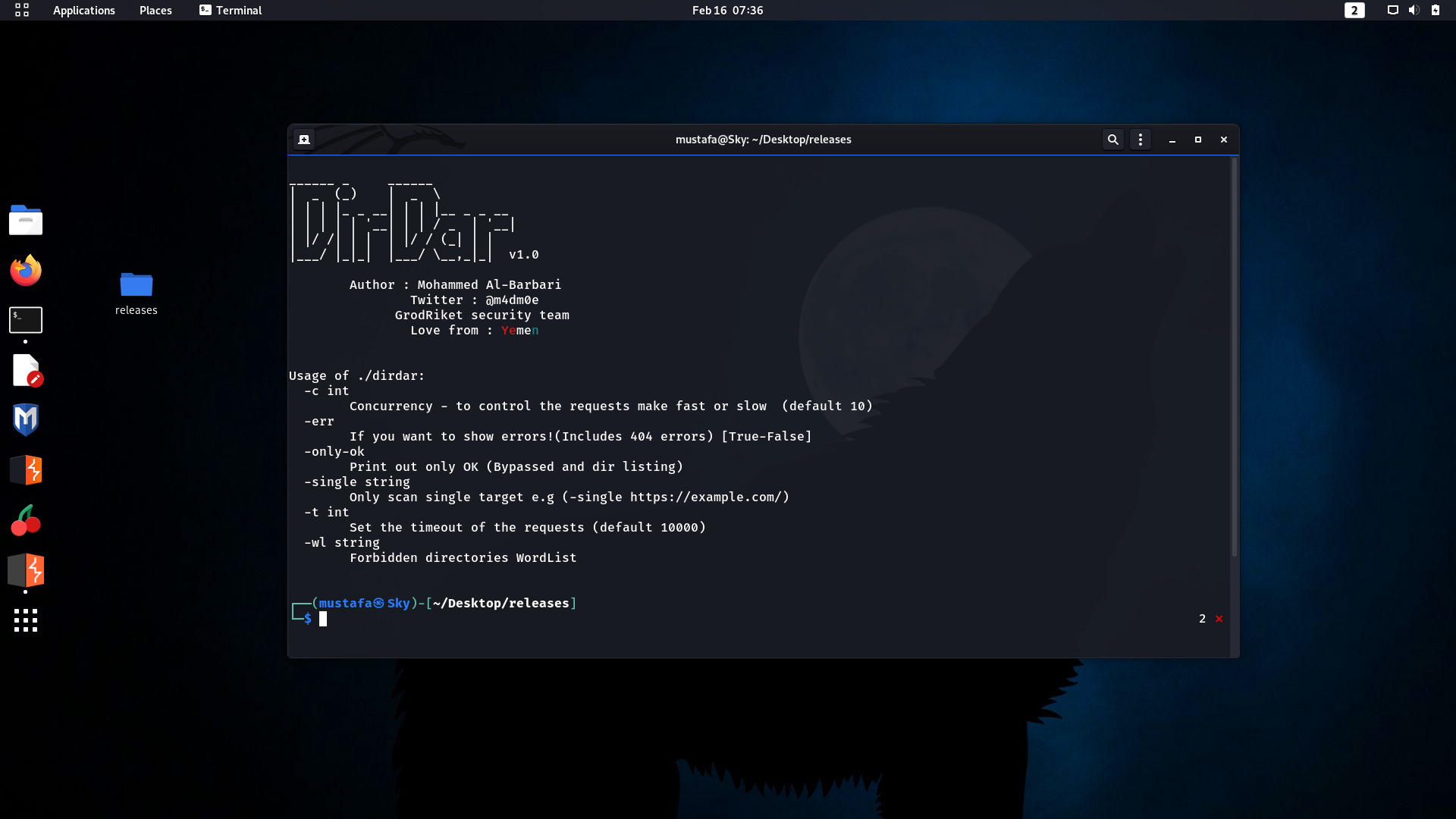
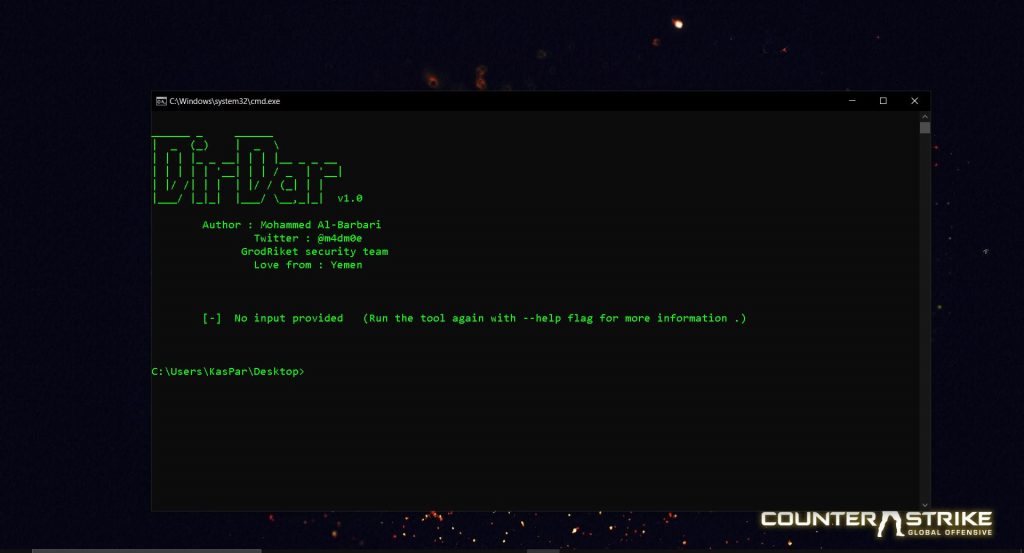
Tool screen:
⦿ Linux
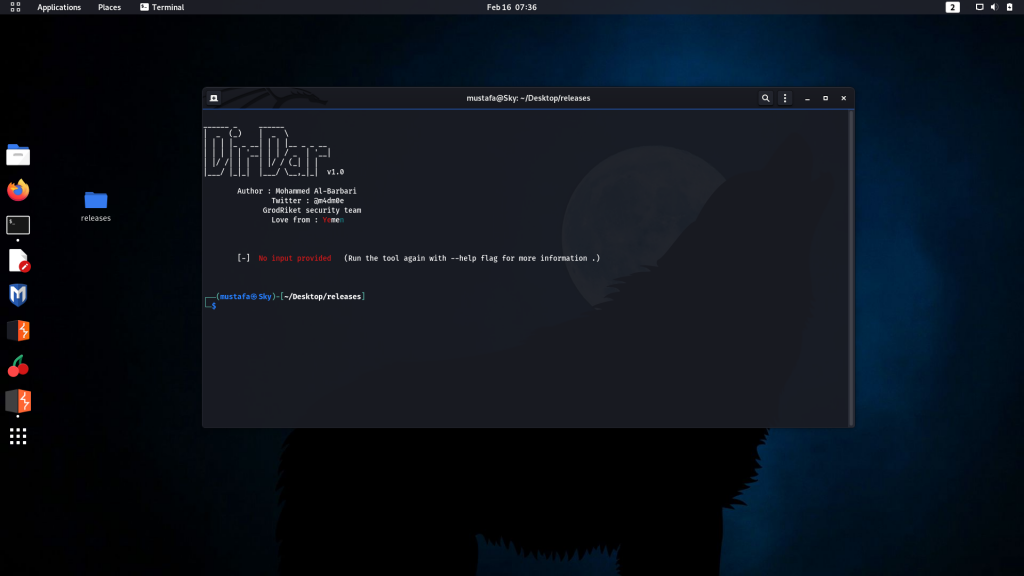
⦿ Windows
Help & Flags
-threads int
Number of threads (Defaulf 40)
-err
If you want to show errors!(Includes 404 errors) [True-False]
-only-ok
Print out only OK (Bypassed and dir listing)
-single string
Only scan single target e.g (-single https://example.com/)
-t int
Set the timeout of the requests (default 10000)
-wl string
Forbidden directories WordList
⦿ Screenshot
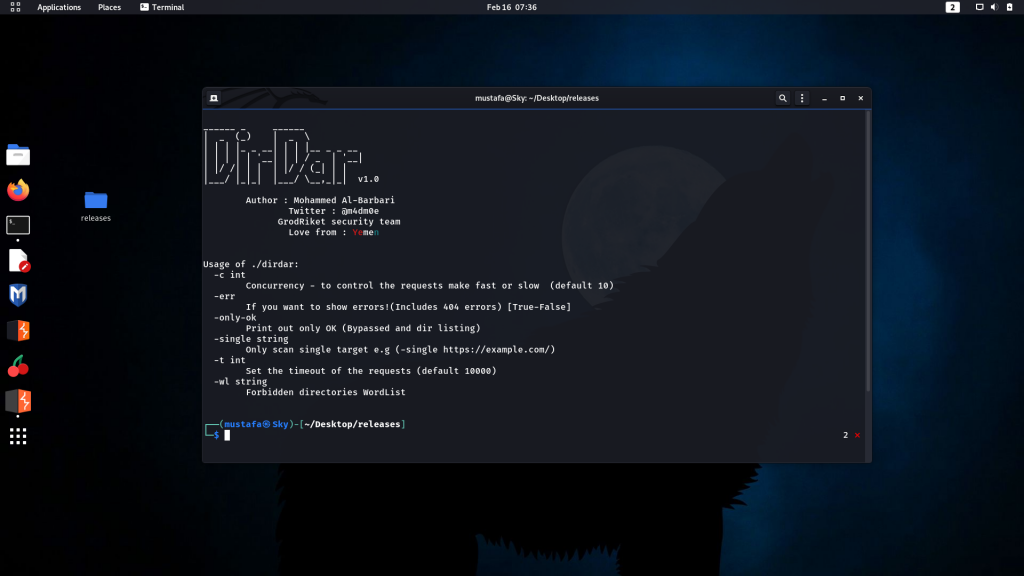
Bugs found by DirDar: (Will share the write up ASAP)
⦿ BackUp files at MTN Group (Triaged)
⦿ OLD php scripts to SQLi at MTN Group (Triaged)
⦿ OLD Files to information disclosure at BOSCH (Triaged)
Review