Offensive Security Tool: dontgo403
Description
DontGo403 by devploit is a tool designed to help Pentesters and Red Teams identify vulnerabilities in web servers that could be exploited to gain unauthorized access to resources. The tool does this by bypassing HTTP error code 403 responses, which are typically used to indicate that a user is not authorized to access a particular resource or webpage.
DontGo403, can send multiple requests to a web server, each with a different User-Agent string, to identify a User-Agent string that is not being blocked by the server. By doing so, they can bypass the 403 error code and potentially gain access to restricted resources.
Offensive Security Courses
Installation
Grab the latest release for your OS from RELEASES
Or compile by your own:
git clone https://github.com/devploit/dontgo403; cd dontgo403; go get; go build
Trending: Offensive Security Tool: dontgo403
Customization
If you want to edit or add new bypasses, you can add it directly to the specific file in payloads folder and the tool will use it.
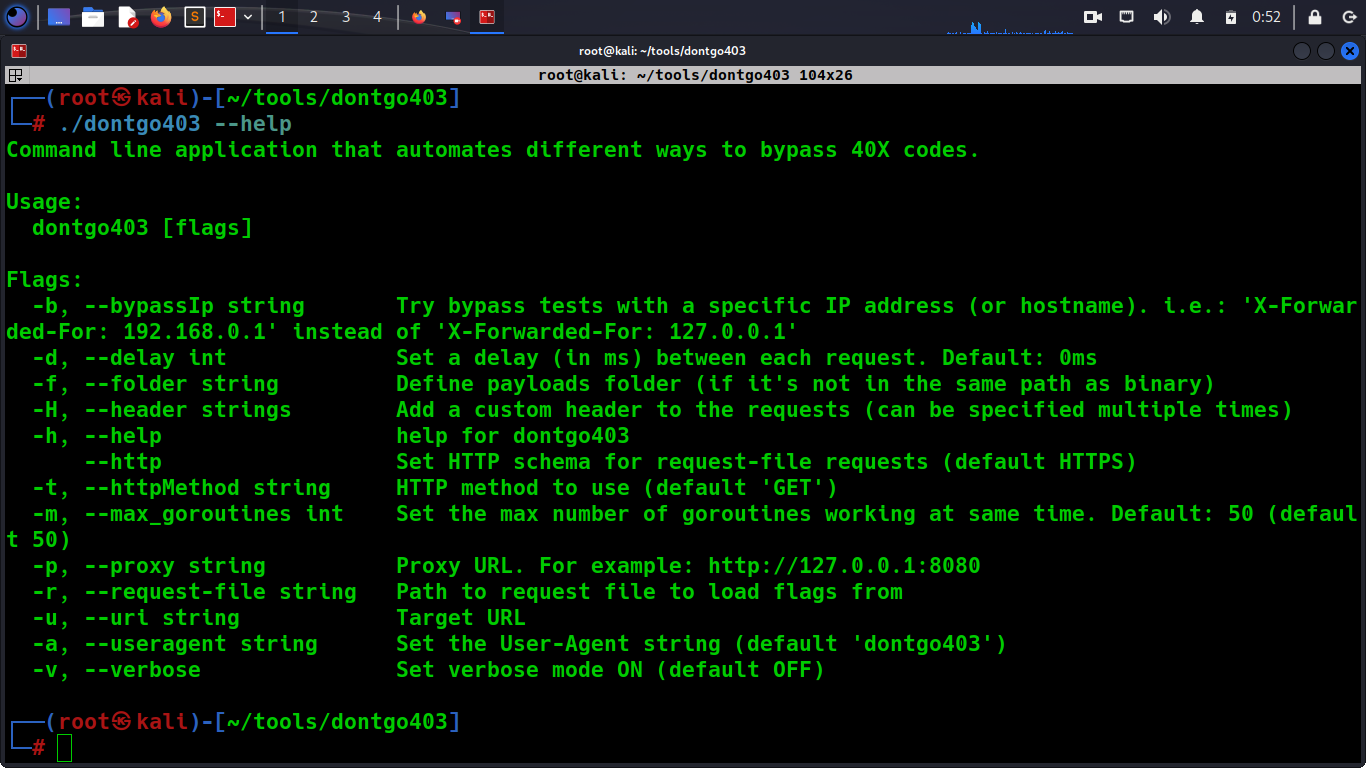
Options
./dontgo403 -h Command line application that automates different ways to bypass 40X codes. Usage: dontgo403 [flags] Flags: -b, --bypassIp string Try bypass tests with a specific IP address (or hostname). i.e.: 'X-Forwarded-For: 192.168.0.1' instead of 'X-Forwarded-For: 127.0.0.1' -d, --delay int Set a delay (in ms) between each request. Default: 0ms -f, --folder string Define payloads folder (if it's not in the same path as binary) -H, --header strings Add a custom header to the requests (can be specified multiple times) -h, --help help for dontgo403 --http Set HTTP schema for request-file requests (default HTTPS) -t, --httpMethod string HTTP method to use (default 'GET') -m, --max_goroutines int Set the max number of goroutines working at same time. Default: 50 (default 50) -p, --proxy string Proxy URL. For example: http://127.0.0.1:8080 -r, --request-file string Path to request file to load flags from -u, --uri string Target URL -a, --useragent string Set the User-Agent string (default 'dontgo403') -v, --verbose Set verbose mode ON (default OFF)