Recon Tool: FinalRecon

Reading Time: 3 Minutes
FinalRecon
FinalRecon developed by thewhiteh4t, is an all in one automatic web reconnaissance tool written in python. The goal of this tool is to provide an overview of the target in a short amount of time while maintaining the accuracy of results. Instead of executing several tools one after another it can provide similar results keeping dependencies small and simple.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Features
FinalRecon provides detailed information such as :
- Header Information
- Whois
- SSL Certificate Information
- Crawler
○ html
▪️ CSS
▪️ Javascripts
▪️ Internal Links
▪️ External Links
▪️ Images
○ robots
○ sitemaps
○ Links inside Javascripts
○ Links from Wayback Machine from Last 1 Year
- DNS Enumeration
○ Over 40 types of Records are queried
○ DMARC Records
- Subdomain Enumeration
○ Over 10 reliable data sources
- Directory Enumeration
○ Support for File Extensions
- Wayback Machine
○ URLs from Last 5 Years
- Port Scan
○ Fast
○ Top 1000 Ports
- Export
○ Formats
▪️ txt
▪️ json [Coming Soon]
Configuration
API Keys
Some Modules Use API Keys to fetch data from different resources, these are optional, if you are not using an API key, they will be simply skipped.
Environment Variables
Keys are read from environment variables if they are set otherwise they are loaded from the config directory.
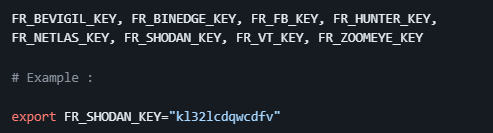
Saved Keys
You can use -k to add the keys which will be saved in config directory automatically
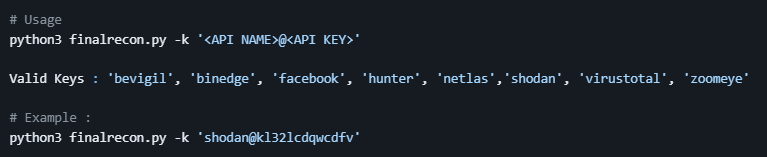
Path = $HOME/.config/finalrecon/keys.json
See Also: OSINT Tool: SiteDorks
See Also: Recon Tool: RecoX
| Source | Module | Link |
|---|---|---|
| Sub Domain Enum | https://developers.facebook.com/docs/facebook-login/access-tokens | |
| VirusTotal | Sub Domain Enum | https://www.virustotal.com/gui/my-apikey |
| Shodan | Sub Domain Enum | https://developer.shodan.io/api/requirements |
| BeVigil | Sub Domain Enum | https://bevigil.com/osint-api |
| BinaryEdge | Sub Domain Enum | https://app.binaryedge.io/ |
| Netlas | Sub Domain Enum | https://docs.netlas.io/getting_started/ |
| ZoomEye | Sub Domain Enum | https://www.zoomeye.hk/ |
| Hunter | Sub Domain Enum | https://hunter.how/search-api |
JSON Config File
Default config file is available at ~/.config/finalrecon/config.json
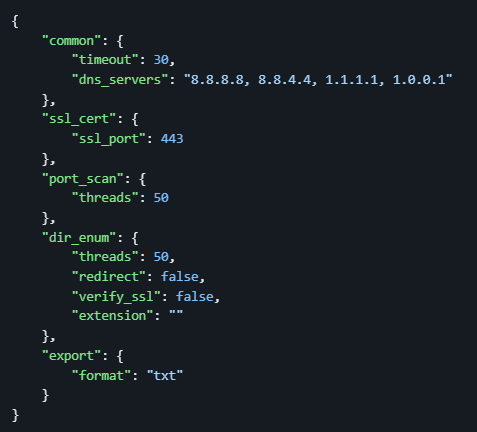
Tested on
- Kali Linux
- BlackArch Linux
FinalRecon is a tool for Pentesters and it’s designed for Linux based Operating Systems, other platforms like Windows and Termux are NOT supported.
Installation
Kali Linux
sudo apt install finalrecon
BlackArch Linux
sudo pacman -S finalrecon
SecBSD
doas pkg_add finalrecon
Other Linux
git clone https://github.com/thewhiteh4t/FinalRecon.git
cd FinalRecon
pip3 install -r requirements.txt
Docker
docker pull thewhiteh4t/finalrecon
docker run -it --entrypoint /bin/sh thewhiteh4t/finalrecon
Also docker user can use this alias to run the finalrecon as the normal CLI user.
alias finalrecon="docker run -it --rm --name finalrecon --entrypoint 'python3' thewhiteh4t/finalrecon finalrecon.py"
And then use finalrecon to start your scan.
remark
If you have any api keys you can easily commit that image in your local machine.
This docker usage needs root to run docker command.
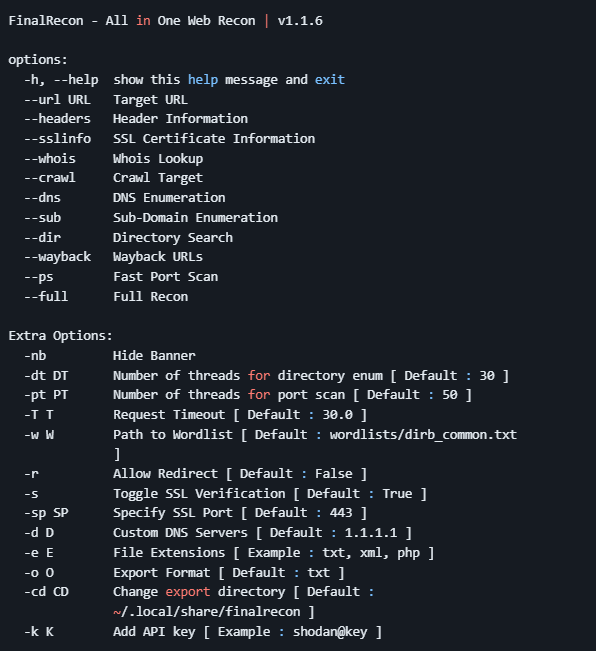
Usage
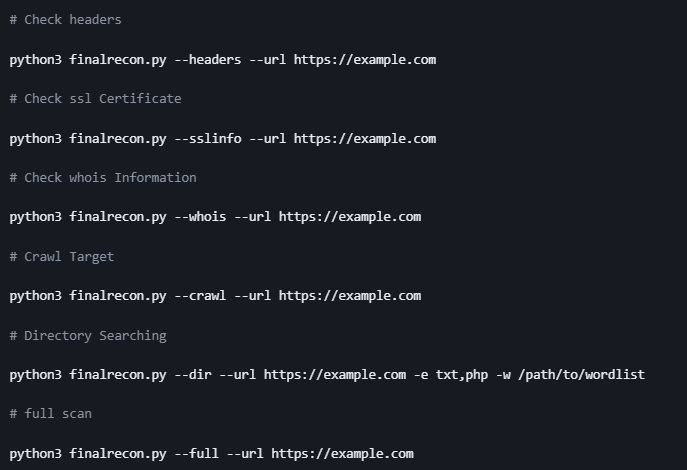
Clone the repo from here: GitHub Link









