Offensive Security Tool: Freeway

Reading Time: 2 Minutes
Freeway
Freeway is written by FLOCK4H and its a Python scapy-based tool for Wi-Fi penetration testing, designed to assist ethical hackers and pentesters in auditing and securing home or enterprise networks.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
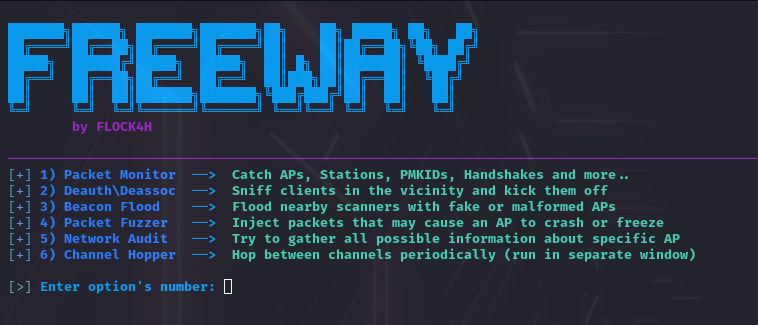
Features
- IEEE 802.11 Packet Monitoring
- Deauthentication Attack
- Beacon Flood
- Packet Fuzzer
- Network Audit
- Channel Hopper
- Evil Twin
Preparation
It is necessary to have:
- A network adapter supporting monitor mode and frame injection.
- An operating system running a Linux distribution.
- Python 3+ installed.
Setup
Option A: Install via PyPi (RECOMMENDED)
$ sudo pip install 3way
Option B: Install or run manually
First, clone the repository:
git clone https://github.com/FLOCK4H/Freeway
Navigate to the cloned repository:
cd Freeway
Option 1: Install dependencies, folders, and Freeway. (RECOMMENDED)
This will allow to launch the tool from anywhere
sudo pip install .
Option 2: Run without installation using Python.
Must be called from the /Freeway directory
sudo pip install scapy rich
sudo python Freeway
See Also: Recon Tool: RecoX
Usage
This tool comes with its own command line interface (CLI) and can be run without specifying any additional arguments.
sudo Freeway
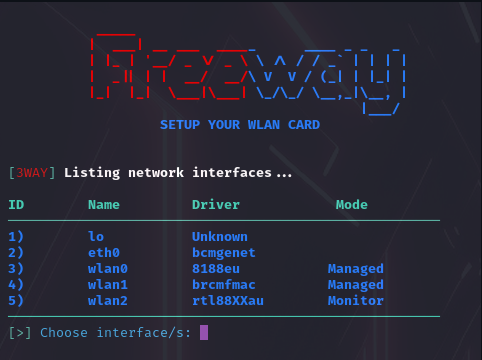
Follow the prompt to select the network adapter (see Section 3):
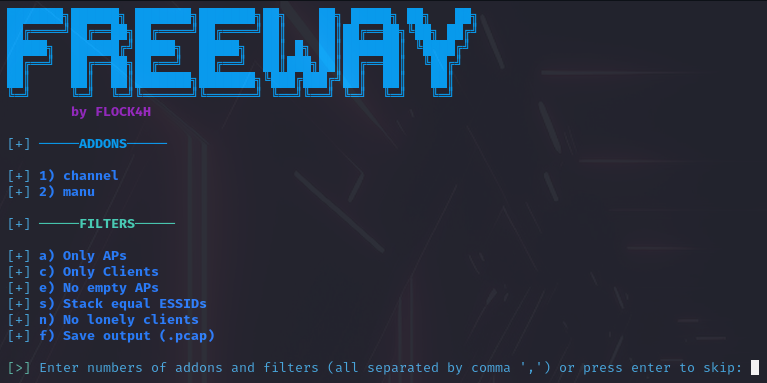
Select the feature and parameter(s):
And with the additional arguments, to skip the CLI partially or completely.
sudo Freeway -i wlan2 -a monitor -p 1,2,a
‘-p’ is not required with ‘-a’, e.g., this will prompt for parameters to specify in the CLI:
sudo Freeway -i wlan2 -a deauth
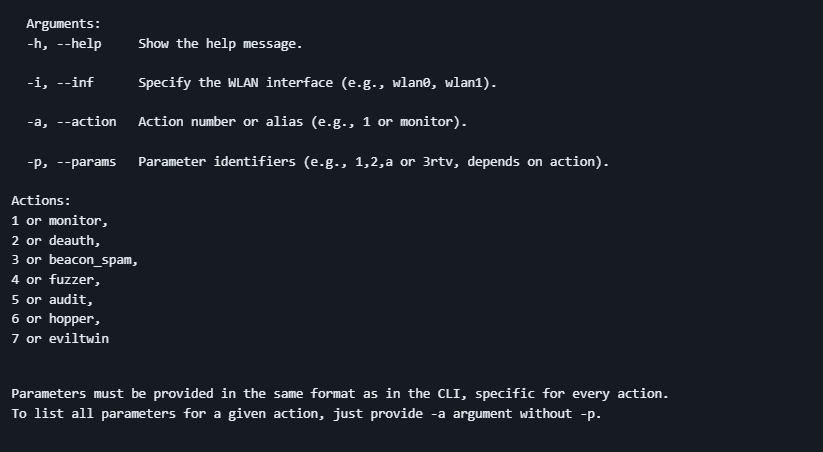
All arguments, actions, and parameters:
Details
- Packet Monitor – Sniffs the Wi-Fi packets in the air, analyze them and return the result onto the python’s curses display. Catches SSIDs, MACs, Clients, Uptime, Channel, Signal (dBm), Encryption and resolves manufacturer. Catches PMKIDs in hashcat crackable format, and 4-way Handshakes, as well as other EAPOL packets. Logs the captured session to the /caps folder or every captured packet if Save output was selected.
- Deauthentication Attack (Deauthing) – Disconnects a device from the network by sending a packet containing AP1 address, device address (or broadcast for Mass Deauthing) and the deauthentication frame with a reason of kicking the client(s). In case where a device address is a broadcast address, the AP will in most cases disconnect all clients at once. Freeway creates separate thread for every AP or client found in order to make deauthing maximally efficient.
- Beacon Flood Attack – Floods the nearby Wi-Fi scanners with fake or malformed APs. It can cause the devices looking for WiFi to behave abnormally (e.g. crash, freeze, drain the battery or run slower) and disrupt the nearby network traffic. User is able to specify his own ssid list, use the default one and generate correct (but random) or malformed beacon packets.
- Packet Fuzzer – Fuzzing is a technique of network vulnerability assessment by sending a wide array of malformed or semi-random data to network interfaces and observing the responses. Freeway covers: Replay captured packets (RX&TX2), Spam CTS/RTS or Probe requests and Flood an AP with Authentication or Association Frames. Devices that will capture fuzzed packets will behave differently depending on vulnerability level of receiver (!USE WITH CAUTION!).
- Network Audit – Gathers all possible information about specific network and returns them onto the curses view. Tracks all clients signal and last activity, as well as resolve the manufacturer.
- Channel Hopper – Changes the current channel of the network adapter. Helpful in making specific attacks more successful.
- Evil Twin – Hosts a legitimate Access Point with Captive Portal, this ‘legitimate’ AP asks user for login/ bank credentials, or to download malware. First, there’s a normal AP created, most times with an ESSID and MAC of existing network. Then, we host our captive portal (e.g., login website), so a normal web server, that reroutes users to our index.html trying to associate with the network we spoof.
1Access Points
2Transceive and receive at the same time
You can read the article about this tool.
Clone the repo from here: GitHub Link