Blue Team Tool: Ghostport
Reading Time: 3 Minutes
Ghostport
Ghostport developed by vxfemboy, is a high-performance port spoofing tool to deceive and mislead port scanners. By dynamically emulating services across all ports, Ghostport effectively creates the illusion of various open services, making it challenging for port scanners to identify real services accurately. This tool incorporates customizable signatures for emulation, efficient asynchronous handling through Rust’s Tokio library, and straightforward traffic redirection.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Features
- Dynamic Port Emulation: Responds to port scans with a variety of convincing service signatures.
- Customizable Signatures: Easily add or modify service signatures through a simple text file.
- High Performance: Built with Rust and Tokio for efficient, asynchronous handling of connections.
- Flexible Logging: Offers debug, verbose, and quiet logging modes for different use cases.
- Easy to Use: Simple command-line interface with sensible defaults.
Installation
git clone https://github.com/vxfemboy/ghostport.git
cd ghostport
cargo build --release
Usage
Basic usage:
./target/release/ghostport -s signatures.txt
or you can run with cargo
git clone https://github.com/vxfemboy/ghostport.git
cd ghostport
cargo run -- -s signatures.txt
This will start Ghostport on the default address (127.0.0.1:8888) using the signatures from signatures.txt.
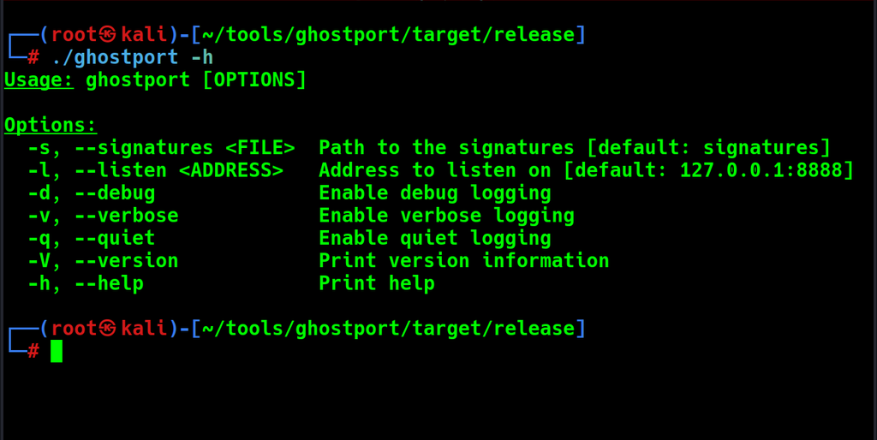
Command-line Options
- -s, –signatures <FILE>: Path to the signatures file (default: “signatures”)
- -l, –listen <ADDRESS>: Address to listen on (default: “127.0.0.1:8888”)
- -d, –debug: Enable debug logging
- -v, –verbose: Enable verbose logging
- -q, –quiet: Enable quiet logging
- -V, –version: Print version information
Examples
Run with custom address and verbose logging:
./target/release/ghostport -s signatures.txt -l 0.0.0.0:8888 -v
Run with debug logging:
./target/release/ghostport -s signatures.txt -l 0.0.0.0:8888 -d
Signature File Format
The signature file should contain one signature per line. Signatures can be raw text or regex patterns. For example:
HTTP/1.1 200 OK\r\nServer: Apache/2.4.41 (Unix)\r\n
SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.1
220 (vsFTPd 3.0.3)
for more examples, see the signatures file.
Routing Traffic to Ghostport
To redirect all incoming TCP traffic to Ghostport, you can use iptables. This will allow Ghostport to respond to connections on any port, effectively spoofing all services:
INTERFACE="eth0" # change to your network interface
iptables -t nat -A PREROUTING -i $INTERFACE -p tcp -m tcp -m multiport --dports 1:65535 -j REDIRECT --to-ports 8888
Note: This requires root privileges and will affect all incoming TCP connections on the specified interface. Use with caution, especially on production systems.
iptables -t nat -D PREROUTING -i $INTERFACE -p tcp -m tcp -m multiport --dports 1:65535 -j REDIRECT --to-ports 8888
Clone the repo from here: GitHub Link