Recon Tool: go-dork
Reading Time: 2 Minutes
go-dork
go-dork by dwisiswant0 is a is a powerful and efficient command-line tool written in the Go programming language, designed to be the fastest dork scanner available. It streamlines the process of conducting advanced Google dork queries, making it an invaluable resource for security researchers, bug bounty hunters and penetration testers.
There are also various search engines supported by go-dork, including Google, Shodan, Bing, Duck, Yahoo and Ask.
See Also: A Practical Guide to Hacking Techniques for finding Top Bugs.
The Bug Bounty Hunting Course
Install
- Download a prebuilt binary from releases page, unpack and run! or
- If you have Go 1.15+ compiler installed and configured:
> GO111MODULE=on go install dw1.io/go-dork@latest
Usage
Basic Usage
It’s fairly simple, go-dork can be run with:
> go-dork -q "inurl:'...'"
Flags
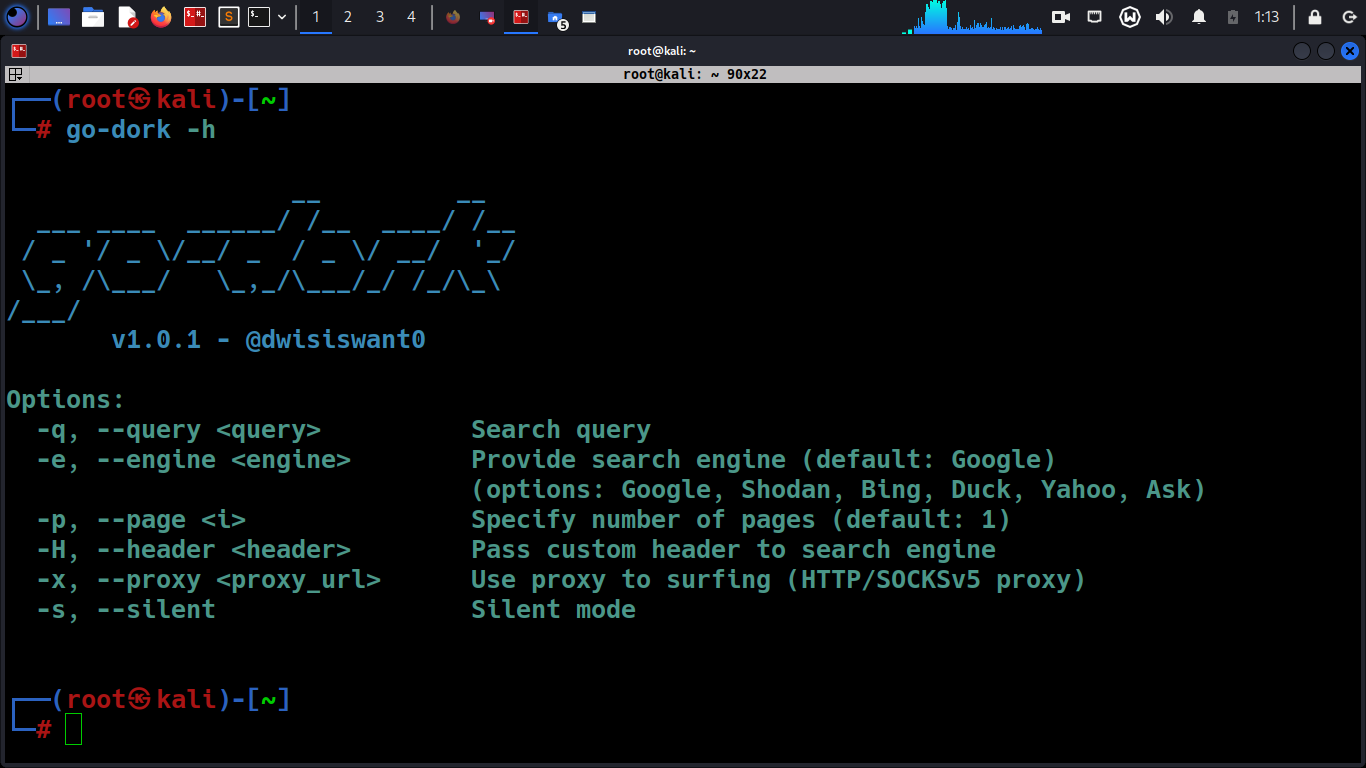
go-dork -h
This will display help for the tool. Here are all the switches it supports.
| Flag | Description |
|---|---|
| -q/–query | Search query (required) |
| -e/–engine | Provide search engine (default: Google) |
| (options: Google, Shodan, Bing, Duck, Yahoo, Ask) | |
| -p/–page | Specify number of pages (default: 1) |
| -H/–header | Pass custom header to search engine |
| -x/–proxy | Use proxy to surfing |
| -s/–silent | Silent mode, prints only results in output |
See Also: Offensive Security Tool: SQLMutant
See Also: OSINT Tool: MOSINT
Querying
> go-dork -q "inurl:..."
Queries can also be input with stdin
cat dorks.txt | go-dork -p 5
Defining engine
Search engine can be changed from the available engines: Google, Shodan, Bing, Duck, Yahoo, Ask. However, if the -e flag is not defined, it will use the Google search engine by default.
> go-dork -e bing -q ".php?id="
This will do a search by the Bing engine.
Pagination
By default, go-dork scrapes the first page, you can customize using the -p flag.
go-dork -q "intext:'jira'" -p 5
It will search sequentially from pages 1 to 5.
Adding custom headers
Maybe you want to use a search filter on the Shodan engine, you can use custom headers to add cookies or other header parts.
> go-dork -q "org:'Target' http.favicon.hash:116323821" \--engine shodan -H "Cookie: ..." -H "User-Agent: ..."
Using proxy
Using a proxy, this can also be useful if Google or other engines meet Captcha.
go-dork -q "intitle:'BigIP'" -p 2 -x http://127.0.0.1:8989
Chained with other tools
If you want to chain the go-dork results with another tool, use the -s flag.
> cat dorks.txt | go-dork | pwntools
> go-dork -q "inurl:'/secure' intext:'jira' site:org" -s | nuclei -t workflows/jira-exploitaiton-workflow.yamlClone the repo from here: GitHub Link
See Also: Deep Dive to Fuzzing for Maximum Impact









