Offensive Security Tool: GoMapEnum
Reading Time: 3 Minutes
Offensive Security Tool: GoMapEnum
GoMapEnum
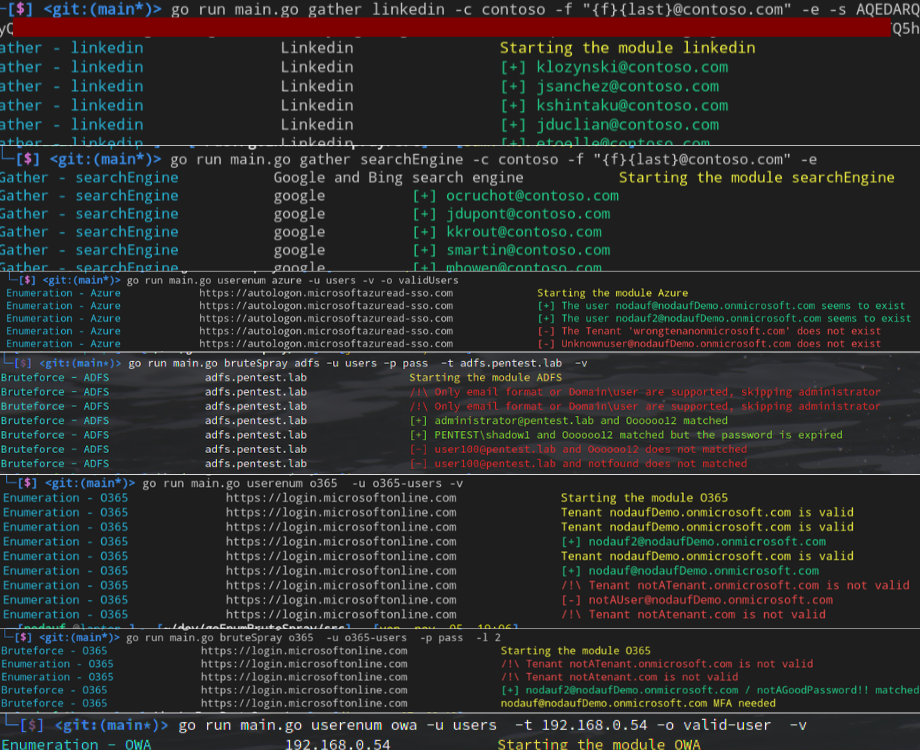
As bug bounty hunters, pentesters you should work with fuzzing and bruteforcing constantly depending on the scope. As there are many tools to do that, this tool has it all in one. Written by nodauf, it allows user enumeration and password bruteforce on Azure, ADFS, OWA, O365 and gather emails on LinkedIn in a more evasive and sophisticated way to bypass a lot of mechanisms.
Description
Summary
The recommended module is o365 for user enumeration and passwords bruteforce / spray. Additional information can be retrieved to avoid account lockout, to know that the password is good but expired, MFA enabled and more.Make sure to check this tool as it offers different capabilities based on what you are attacking, from all those modules expect to see for: LinkedIn, Search Engines, Azure, ADFS, Office 365 and OWA. After all, how can you be sure of your infrastructure’s security if you do not put it into real world tests.
See Also: New malware hides as legit nginx process on e-commerce servers
This module should be used to retrieve a list of email addresses before validating them through a user enumeration module. The company will be searched on LinkedIn and all people working at these companies will be returned in the specified format.
The Linkedin’s session cookie li_at is required.

SearchEngine
This module should be used to retrieve a list of email addresses before validating them through a user enumeration module. The company name will be searched on Google and Bing with a dork to find people working in the company (site:linkedin.com/in+”%s”). The results title will be parsed to output email addresses in the specified format.

See Also: Hacking Stories: Rafael Núñez (aka RaFa), hacking NASA with the hacking group: World of Hell
Azure
User enumeration
The Azure module is only available to enumerate the users of a tenant. The authentication request will be made on https://autologon.microsoftazuread-sso.com, a detailed response shows if the account does not exist, a MFA is required, if the account is locked, …

ADFS
Passwords bruteforce / spray
The ADFS module is only available to bruteforce or spray a password. The authentication request is sent to https://<target>/adfs/ls/idpinitiatedsignon.aspx?client-request-id=<randomGUID>&pullStatus=0. An error message can informs the user if the password is expired.

See Also: Complete Offensive Security and Ethical Hacking Course
O365
This module allows to enumerate users and bruteforce / spray passwords.
User enumeration
Several modes are available: office, oauth2 and OneDrive (not implemented yet). The office mode is recommended as no authentication is made. Oauth2 can retrieve additional information through AADSTS error code (MFA enable, locked account, disabled account)

Passwords bruteforce / spray
As for the user enumeration, two modes are available: oauth2 and autodiscover (not implemented yet). The Oauth2 is the recommended mode, it allows to get much information thanks to the AADSTS error code.

OWA
This module allows to enumerate users and bruteforce / spray passwords.
User enumeration
Enumeration is made with authentication requests. Authentication for a non-existent user will take longer than for a valid user. At first, the average response time for an invalid user will be calculated and then the response time for each authentication request will be compared.

Passwords bruteforce / spray
Please note that no account locking mechanism can be implemented because no information about it is returned.

See Also: Offensive Security Tool: Hashcat