Offensive Security Tool: Hashcat

Reading Time: 3 Minutes
Offensive Security Tool: Hashcat
Hashcat
Hashcat is the world’s fastest and most advanced password recovery utility, supporting five unique modes of attack for over 300 highly-optimized hashing algorithms. Hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and macOS, and has facilities to help enable distributed password cracking.
Brute-forcing has evolved into not just cracking passwords from websites, but also specifically from databases, archived folders/files, backups, hashes and more. This tool is different because of the way it can utilize all your machine’s resources especially if you have a GPU. Depending on the machine used, it will give you an ETA of how fast you can crack, with speeds of testing more than 1000 combinations per second.
It can be used as part of your pentesting, bug bounty especially when you come across a lot of secrets keys that can be analyzed of which encryption is used and crack them accordingly to reveal the hidden content of the encryption. Since it supports almost all known algorithms you can check it out by testing it in a training environment to uncover its true power and speed.
See Also: New Linux malware hides in cron jobs with invalid dates
Features
- World’s fastest password cracker
- World’s first and only in-kernel rule engine
- Free
- Open-Source (MIT License)
- Multi-OS (Linux, Windows and macOS)
- Multi-Platform (CPU, GPU, APU, etc., everything that comes with an OpenCL runtime)
- Multi-Hash (Cracking multiple hashes at the same time)
- Multi-Devices (Utilizing multiple devices in same system)
- Multi-Device-Types (Utilizing mixed device types in same system)
- Supports password candidate brain functionality
- Supports distributed cracking networks (using overlay)
- Supports interactive pause / resume
- Supports sessions
- Supports restore
- Supports reading password candidates from file and stdin
- Supports hex-salt and hex-charset
- Supports automatic performance tuning
- Supports automatic keyspace ordering markov-chains
- Built-in benchmarking system
- Integrated thermal watchdog
- 350+ Hash-types implemented with performance in mind
- … and much more
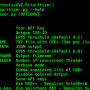
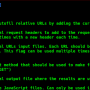
Screenshot
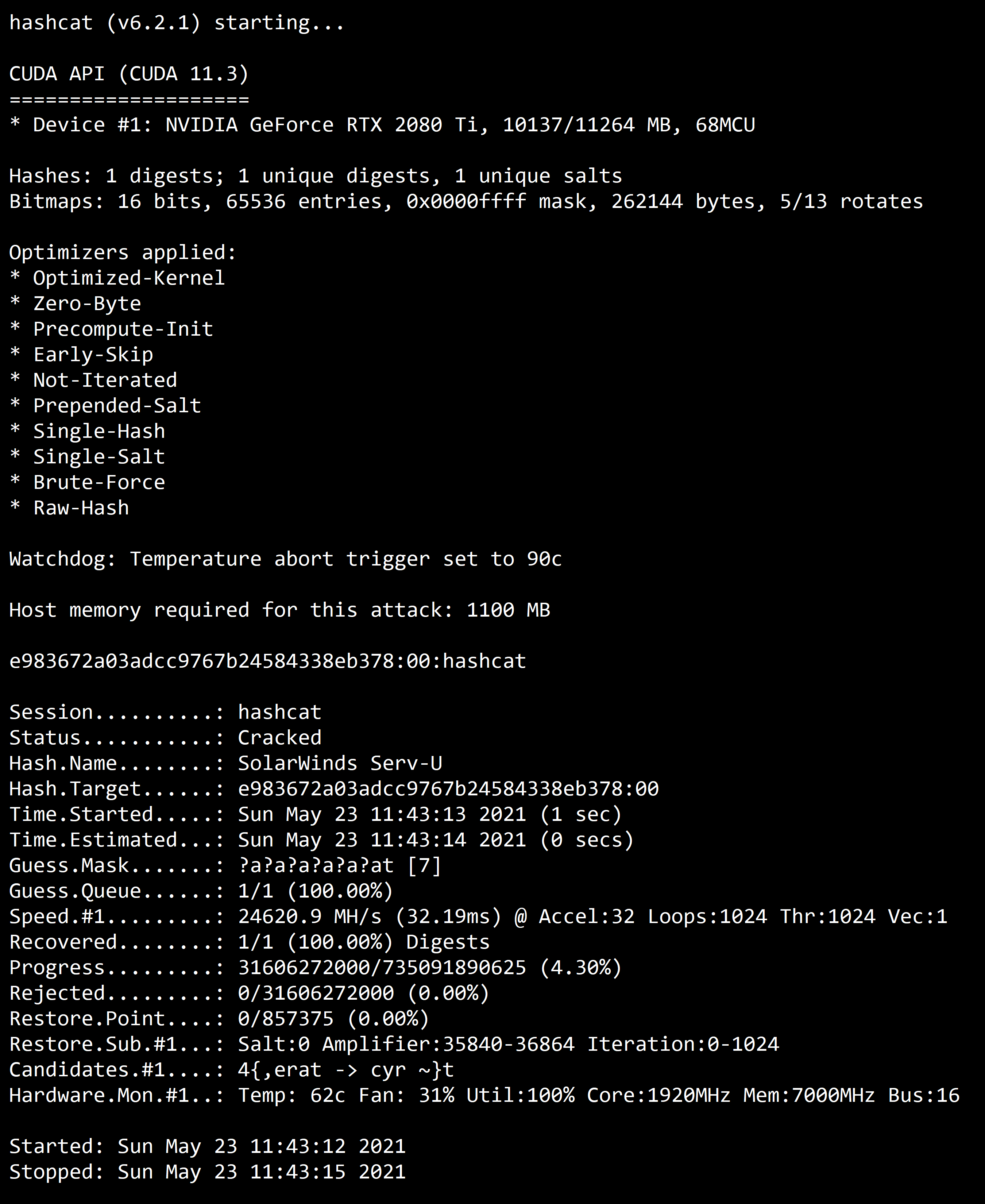
See Also: Obfuscated Payloads can be undetected even if you have real-time protection
Algorithms
- MD4
- MD5
- SHA1
- SHA2-224
- SHA2-256
- SHA2-384
- SHA2-512
- SHA3-224
- SHA3-256
- SHA3-384
- SHA3-512
- RIPEMD-160
- BLAKE2b-512
- GOST R 34.11-2012 (Streebog) 256-bit, big-endian
- GOST R 34.11-2012 (Streebog) 512-bit, big-endian
- GOST R 34.11-94
- GPG (AES-128/AES-256 (SHA-1($pass)))
- Half MD5
- Keccak-224
- Keccak-256
- Keccak-384
- Keccak-512
- Whirlpool
- SipHash
Click here to see all of the algorithms.
Attack-Modes
- Straight *
- Combination
- Brute-force
- Hybrid dict + mask
- Hybrid mask + dict
- Association *
* accept Rules
Supported OpenCL runtimes
- AMD
- Apple
- Intel
- NVidia
- POCL
- ROCm
Supported OpenCL device types
- GPU
- CPU
- APU
Installation
Download the latest release and unpack it in the desired location. Please remember to use 7z x when unpacking the archive from the command line to ensure full file paths remain intact.
Usage/Help
Please refer to the Hashcat Wiki and the output of –help for usage information and general help. A list of frequently asked questions may also be found here. The Hashcat Forum also contains a plethora of information. If you still think you need help by a real human come to Discord.
Building
Refer to BUILD.md for instructions on how to build hashcat from source.
See Also: Hacking stories – The first botnet hijacker aka the Zombie King