Offensive Security Tool: HExHTTP
Reading Time: 3 Minutes
HExHTTP
HExHTTP, developed by c0dejump, is an advanced security testing tool designed to analyze HTTP headers, identify vulnerabilities, and detect interesting behaviors in web responses. It automates security checks on various HTTP-based attack vectors, including cache poisoning, cookie reflection, and server misconfigurations.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Installation
Python
pip install -r requirements.txt
./hexhttp.py -u 'https://target.tld/'
# OR
python3 hexhttp.py -u 'https://target.tld/'
Docker
docker build -t hexhttp:latest .
docker run --rm -it --net=host -v "$PWD:/hexhttp/" hexhttp:latest -u 'https://target.tld/'
See Also: Offensive Security Tool: SSRFPwned
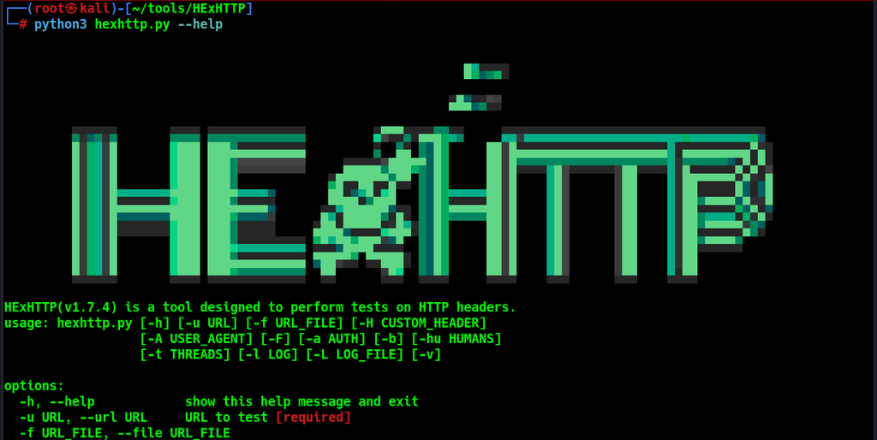
Usage
Usage: hexhttp.py [-h] [-u URL] [-f URL_FILE] [-H CUSTOM_HEADER] [-A USER_AGENT] [-F] [-a AUTH] [-b] HExHTTP is a tool designed to perform tests on HTTP headers. options: -h, --help show this help message and exit -u URL, --url URL URL to test [required] -f URL_FILE, --file URL_FILE File of URLs -H CUSTOM_HEADER, --header CUSTOM_HEADER Add a custom HTTP Header -A USER_AGENT, --user-agent USER_AGENT Add a custom User Agent -F, --full Display the full HTTP Header -a AUTH, --auth AUTH Add an HTTP authentication. Ex: --auth admin:admin -b, --behavior Activates a simplified version of verbose, highlighting interesting cache behaviors -hu HUMANS, --humans HUMANS Performs a timesleep to reproduce human behavior (Default: 0s) value: "r" or "random" -t THREADS, --threads THREADS Threads numbers for multiple URLs. Default: 10 -l LOG, --log LOG Set the logging level (DEBUG, INFO, WARNING, ERROR, CRITICAL) -L LOG_FILE, --log-file LOG_FILE The file path pattern for the log file. Default: logs/ -v, --verbose Increase verbosity (can be used multiple times)
Arguments
# Scan only one domain
» ./hexhttp.py -u 'https://target.tld/'
# Scan a list of domains with behavior feature
» ./hexhttp.py -b -f domains.lst
# Add custom User-Agent
» ./hexhttp.py -u 'https://target.tld/' --user-agent "User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64) Firefox/123.0-BugBounty"
# Use a custom Header and authentication
» ./hexhttp.py --header 'Foo: bar' --auth 'user:passwd' -u 'https://target.tld/'
# Loop on domains, grep for vulnerabilities only and send result with notify (from projectdiscovery)
» for domain in $(cat domains.lst); do ./hexhttp.py -u "$domain" | grep -Eio "(INTERESTING|CONFIRMED)(.*)PAYLOAD.?:(.*){5,20}$" | notify -silent; doneExamples
Example on a public target
Example with a confirmed Cache Poisoning vulnerability
You can test this tool on the Web Security Academy’s vulnerable labs, like Web cache poisoning with an unkeyed header. The expected result should be the same as below.
Features
- Server Error response checking
- Localhost header response analysis
- Vhosts checking
- Methods response analysis
- HTTP Version analysis [Experimental]
- Cache Poisoning DoS (CPDoS) techniques
- Web cache poisoning
- Range poisoning/error (416 response error) [Experimental]
- Cookie Reflection
- CDN/proxies Analysis (Envoy/Apache/Akamai/Nginx) [IP]
Clone the repo from here: GitHub Link