Offensive Security Tool: HTTPLoot

Reading Time: 3 Minutes
HTTPLoot by redhuntlabs is an automated tool that can simultaneously crawl, fill forms, trigger error/debug pages, and “loot” secrets out of the client-facing code of sites. When you are working with WebApps, reconnaissance is the most important part when it comes to finding vulnerabilities, and it has multiple techniques and ways to do this. Crawling websites, checking forms, search queries, trying to find hard-coded secrets, and tokens requires time to analyze, and manual checkups. This tool can help you perform this really fast, so you can focus on the results, using your skillset to demonstrate issues found that create serious impacts throughout your Proof of Concept.
Usage
To use the tool, you can grab any one of the pre-built binaries from the Releases section of the repository. If you want to build the source code yourself, you will need Go > 1.16 to build it. Simply running go build will output a usable binary for you.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
Video demo:
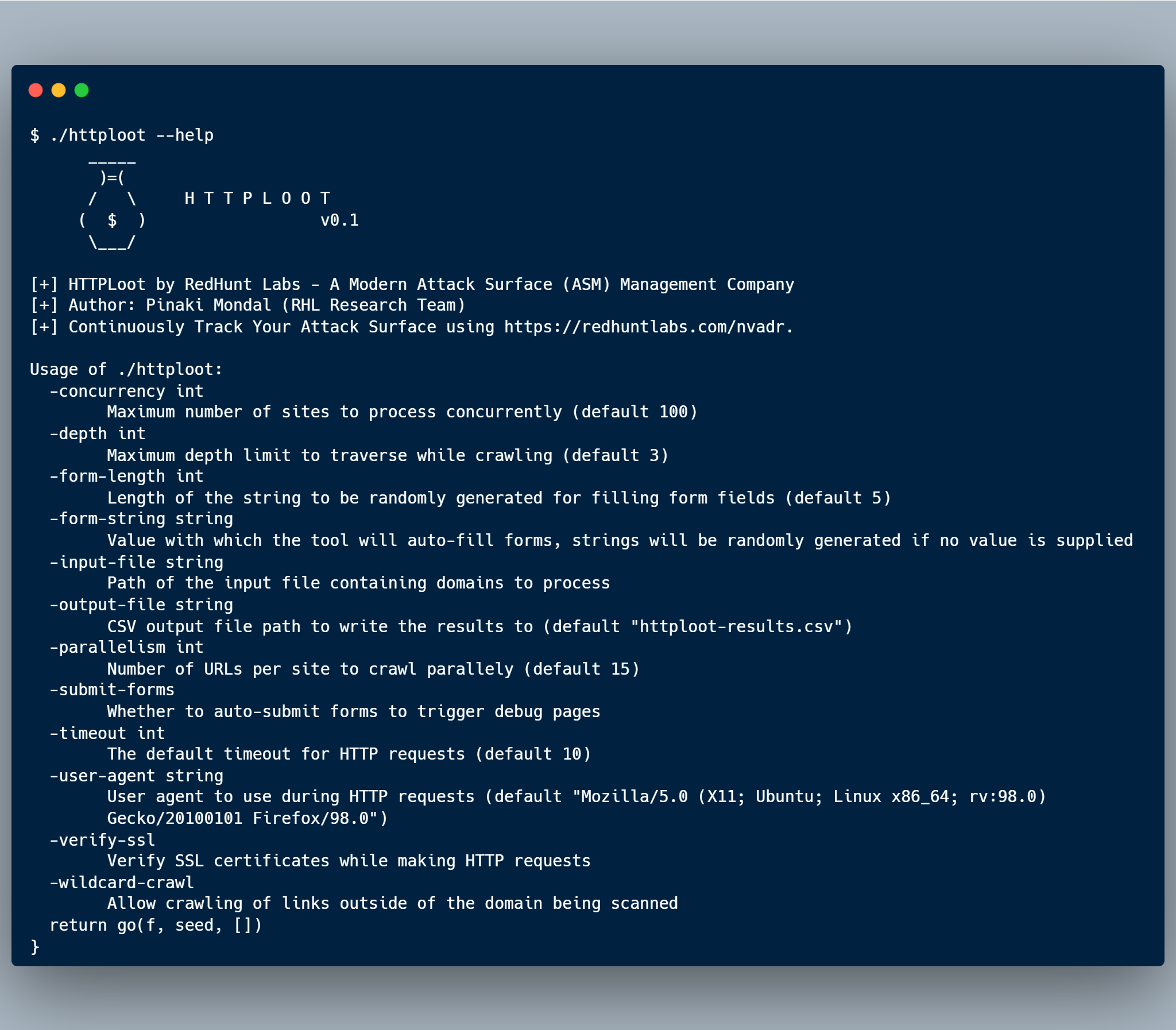
Here is the help usage of the tool:
Trending: Offensive Security Tool: Mobile Security Framework (MobSF)
Concurrent scanning
There are two flags which help with the concurrent scanning:
- -concurrency: Specifies the maximum number of sites to process concurrently.
- -parallelism: Specifies the number of links per site to crawl parallelly.
Both -concurrency and -parallelism are crucial to performance and reliability of the tool results.
Crawling
The crawl depth can be specified using the -depth flag. The integer value supplied to this is the maximum chain depth of links to crawl grabbed on a site.
An important flag -wildcard-crawl can be used to specify whether to crawl URLs outside the domain in scope.
NOTE: Using this flag might lead to infinite crawling in worst case scenarios if the crawler finds links to other domains continuously.
Filling forms
If you want the tool to scan for debug pages, you need to specify the -submit-forms argument. This will direct the tool to autosubmit forms and try to trigger error/debug pages once a tech stack has been identified successfully.
If the -submit-forms flag is enabled, you can control the string to be submitted in the form fields. The -form-string specifies the string to be submitted, while the -form-length can control the length of the string to be randomly generated which will be filled into the forms.
Network tuning
Flags like:
- -timeout – specifies the HTTP timeout of requests.
- -user-agent – specifies the user-agent to use in HTTP requests.
- -verify-ssl – specifies whether or not to verify SSL certificates.
Input/Output
Input file to read can be specified using the -input-file argument. You can specify a file path containing a list of URLs to scan with the tool. The -output-file flag can be used to specify the result output file path — which by default goes into a file called httploot-results.csv.
Trending: OSINT Tool: MOSINT









