Offensive Security Tool: log4j Honeypot Flask
Reading Time: 2 Minutes
Offensive Security Tool: log4j Honeypot Flask
log4j-honeypot-flask
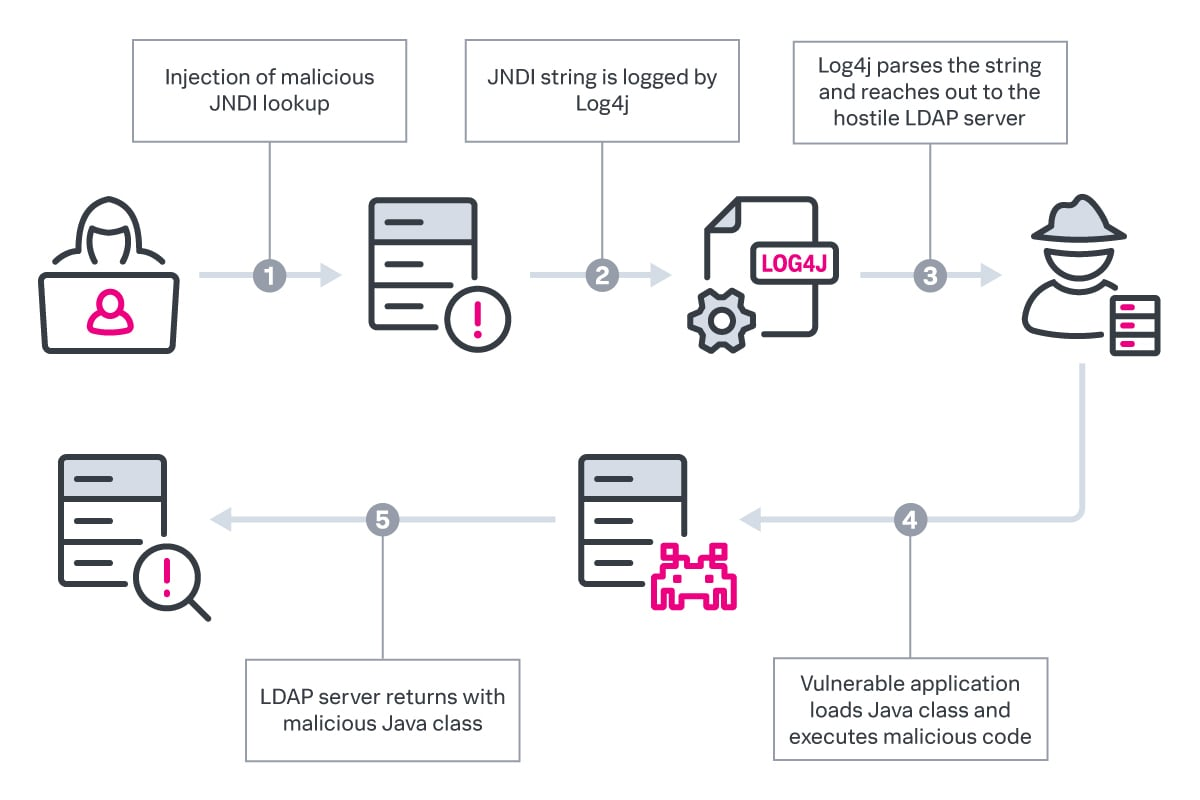
Now that Log4j has been discovered, a scanner we had shared released, and an existing PoC to showcase the damage it can do, we are sharing another HoneyPot tool mechanism that can help you detect for such attacks happening in your company internally or externally specifically for this, based on the patterns and reverse engineering of the tool that took place. You can setup this Honeypot, set up notifications, and stay steps ahead mitigating it from being compromised with this latest Zero Day release CVE, affecting a big number of Apache Servers.
Log4j Honeypot Flask by BinaryDefense is an internal network honeypot for detecting if an attacker or insider threat scans your network for log4j CVE-2021-44228.
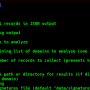
This can be installed on a workstation or server, either by running the Python app/app.py script directly (you’ll need python3, Flask, and Requests) or as a Docker container.
You will need to set some environment variables (or hard-code them into the script): WEBHOOK_URL=your Teams, Slack or Mattermost webhook URL to receive notifications HONEYPOT_NAME=unique name for this honeypot so you know where the alerts came from HONEYPOT_PORT=8080 or whatever port you want it to listen on.
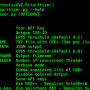
All it does is watch for suspicious string patterns in the requests (form fields and HTTP headers) and alert you if anything weird comes through by sending a message on Teams or Slack.
Important Note: This is a LOW-INTERACTION honeypot meant for internal active defense. It is not supposed to be vulnerable or let attackers get into anything.
See Also: Complete Offensive Security and Ethical Hacking Course
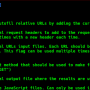
Example running via Docker:
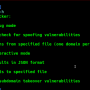
docker build -t log4j-honeypot-flask:latest .
docker run -d -p 8080:8080 -e WEBHOOK_URL=https://yourwebhookurl -e HONEYPOT_NAME=dmz_log4j_hp log4j-honeypot-flask
See Also: Apple fixes macOS security flaw behind Gatekeeper bypass
Example running via command line:
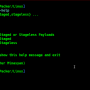
export WEBHOOK_URL=https://yourwebhookurl
export HONEYPOT_NAME=LittleBobbyJNDI
export HONEYPOT_PORT=8081
python3 app/app.py