Offensive Security Tool: pphack
pphack is a tool designed for detecting prototype pollution vulnerabilities in client-side JavaScript code.
OSINT Tool: Certina
Certina is an OSINT tool for red teamers, bug bounty hunters and pentesters to discover subdomains from web certificate data.
Offensive Security Tool: 403jump
403jump is a tool designed for penetration testers and bug bounty hunters to audit the security of web applications and identify potential vulnerabilities. It aims to bypass HTTP 403 (Forbidden) pages using various techniques.
OSINT Tool: NetScout
NetScout is an OSINT tool that finds domains, subdomains, directories, endpoints and files for a given seed URL.
Offensive Security Tool: WAF Bypass
WAF bypass is an open source tool to analyze the security of any WAF for False Positives and False Negatives using predefined and customizable payloads. Check your WAF before an attacker does.
Digital Forensics Tool: mailMeta
mailMeta is a python based forensic tool which reads through the email headers from the email file and extracts crucial information to identify if the email is legitimate.
Recon Tool: SiCat
SiCat is an exploit search tool, and its primary objective is to efficiently identify and gather information about potential exploits from various sources, including both online repositories and local resources.
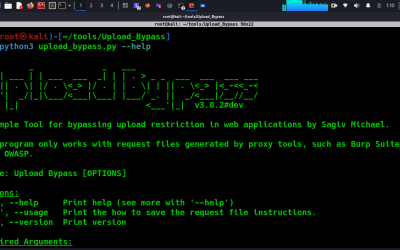
Offensive Security Tool: Upload_Bypass
Upload Bypass is a simple tool designed to assist penetration testers and bug hunters in testing file upload mechanisms. It leverages various bug bounty techniques to simplify the process of identifying and exploiting vulnerabilities, ensuring thorough assessments of web applications.
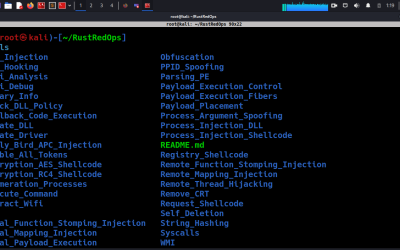
Offensive Security Techniques Repo: RustRedOps
RustRedOps is a repository dedicated to gathering and sharing various tools, projects, advanced techniques and offensive malware related to Red Team operations, with a specific focus on the Rust programming language.