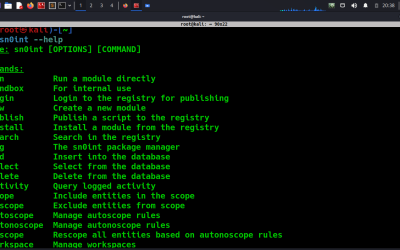
OSINT Tool: sn0int
sn0int is a semi-automatic OSINT framework and package manager designed for IT security professionals, bug bounty hunters, law enforcement agencies, and individuals seeking to gather intelligence about a target or themselves.
Recon Tool: PassDetective
PassDetective is a command-line tool that scans your shell command history for mistakenly written passwords, API keys, and secrets. It uses regular expressions to identify potential sensitive information and helps you avoid accidentally exposing sensitive data in your command history.
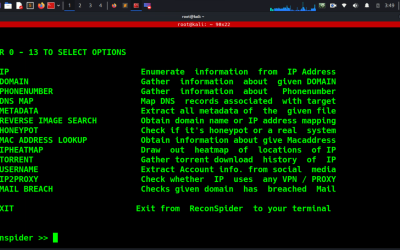
Recon Tool: ReconSpider
ReconSpider is one of the most advanced Open Source Intelligence (OSINT) Framework and Recon for scanning IP Addresses, Emails, Websites, and Organizations and finding out information from different sources.
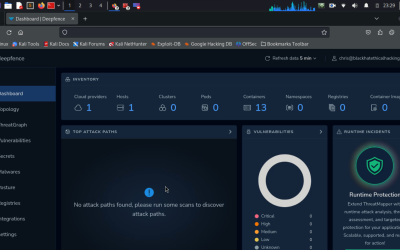
Offensive Security Tool: ThreatMapper
ThreatMapper is a platform for runtime threat management and attack path enumeration in cloud-native environments. It actively hunts for threats in production platforms, ranking them based on their risk of exploitation. It reveals vulnerabilities, exposed secrets, and deviations from security best practices through a combination of agent-based inspection and agent-less monitoring.
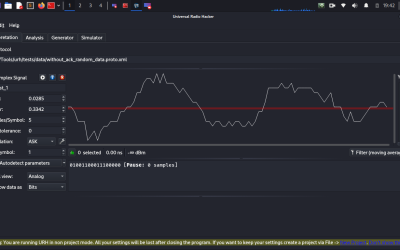
Digital Forensics Tool: Universal Radio Hacker (URH)
The Universal Radio Hacker (URH) is a complete suite for wireless protocol investigation with native support for many common Software Defined Radios (SDRs).
Recon Tool: subby
subby is an uber fast and simple subdomain enumeration tool using DNS and web requests with support for detecting wildcard DNS records.
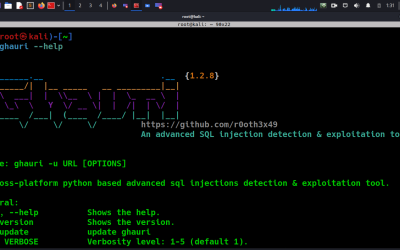
Offensive Security Tool: Ghauri
Ghauri is an advanced cross-platform tool designed to automate the detection and exploitation of SQL injection security vulnerabilities.
Recon Tool: CHOMTE.SH
CHOMTE.SH is a powerful shell script designed to automate recon tasks. It utilizes various Go-based tools to gather information and identify the attack surface, making it a valuable asset for bug bounty hunters and penetration testers.
Offensive Security Tool: o365sprayer
o365sprayer is a tool used to enumerate and spray passwords for Office 365 accounts on both Managed and Federated AD services. It has the ability to distinguish managed O365 and Federated Microsoft Office 365 accounts for a target domain.