Recon Tool: fetchmeurls
fetchmeurls is a Recon tool designed for Bug Bounty Hunters to quickly fetch URLs for multiple domains, either for small or large scopes, actively and passively.
Offensive Security Tool: Noir
Noir is an attack surface detector for source code and it is designed for identifying API endpoints and potential security issues within web applications by analyzing their source code.
Recon Tool: Mantra
Mantra it’s a recon tool with the main objective of searching for API keys in JavaScript files and HTML pages.
Recon Tool: Goblyn
Goblyn is a versatile tool designed for the enumeration and extraction of metadata from files hosted on websites.
Offensive Security Tool: Headerpwn
Headerpwn is a fuzzing tool for finding anomalies and analyzing how servers respond to different HTTP headers. It can provide valuable insights into potential security risks and misconfigurations.
OSINT Tool: Photon
Photon is an advanced web crawler and osint tool for thorough website analysis. It’s capable of scanning websites comprehensively to uncover valuable information.
Recon Tool: Dirhunt
Dirhunt is a web crawler optimize for search and analyze directories. It detects directories with false 404 errors, directories where an empty index file has been created to hide things and much more.
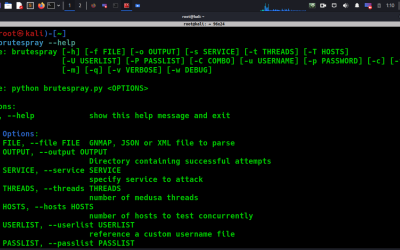
Offensive Security Tool: BruteSpray
BruteSpray a tool that automates and accelerates the testing of weak credentials and passwords across multiple services, such as SSH, RDP, and FTP. BruteSpray operates by accepting a target list and a password list, and then efficiently launching brute force attacks against the specified services.
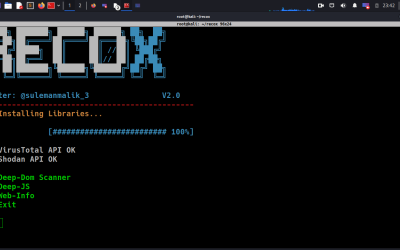
Recon Tool: RecoX
Recox is a powerful tool for finding vulnerabilities in web applications. It goes beyond the OWASP top ten list, making it valuable for security professionals.