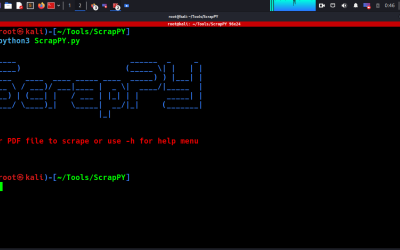
Digital Forensics Tool: ScrapPy
ScrapPY is a Python utility for scraping manuals, documents, and other sensitive PDFs to generate wordlists that can be utilized by offensive security tools to perform brute force, forced browsing, and dictionary attacks against targets.
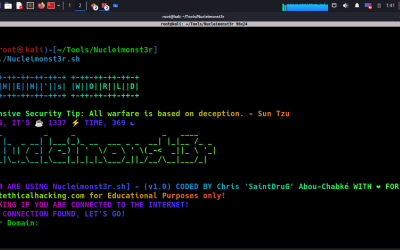
Offensive Security Tool: Nucleimonst3r
Nucleimonst3r is a powerful vulnerability scanner that can help Bug Bounty Hunters find low hanging fruit vulnerabilities for known CVEs and exploits.
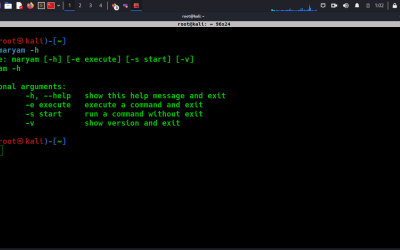
OSINT Tool: Maryam
OWASP Maryam is a modular open-source framework based on OSINT (Open Source Intelligence) and data gathering. It is designed to provide a robust environment to harvest data from open sources and search engines quickly and thoroughly.
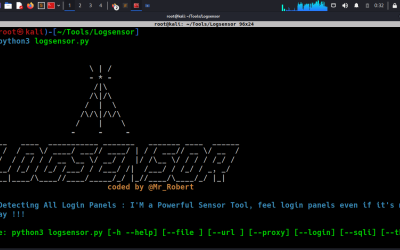
Recon Tool: Logsensor
Logsensor is a powerful tool designed to help identify login panels and perform POST form SQL injection (SQLi) scanning.
Offensive Security Tool: SSRFPwned
SSRFPwned is a tool that automates the process of testing for Server-Side Request Forgery (SSRF) vulnerabilities. The tool injects payloads into the query parameters of each URL and checks the response code to determine if a vulnerability exists. The payloads are custom, with multiple attack vectors, and you can also add more wordlists if you want to test further.
Offensive Security Tool: PhoneSploit Pro
PhoneSploit Pro is an all-in-one hacking tool designed to exploit Android devices remotely. It leverages the power of ADB (Android Debug Bridge) and Metasploit-Framework to gain control over the target device and establish a Meterpreter session. PhoneSploit Pro provides a convenient and efficient solution for penetration testers looking to exploit Android devices remotely.
Offensive Security Tool: Octopus
Octopus is an open source pre-operation C2 server based on python which can control an Octopus powershell agent through HTTP/S. Octopus works in a very simple way to execute commands and exchange information with the C2 over a well encrypted channel, which makes it inconspicuous and undetectable from almost every AV, endpoint protection, and network monitoring solution.
Offensive Security Tool: Pypykatz
PyPyKatz is the Mimikatz implementation in pure Python. It can parse the secrets hidden in the LSASS process. This is just like mimikatz’s sekurlsa:: but with different commands. The main difference here is that all the parsing logic is separated from the data source, so if you define a new reader object you can basically perform the parsing of LSASS from anywhere but has even more features
Offensive Security Tool: Pyramid
Pyramid is a tool to perform post-exploitation task in an evasive manner, executing offensive tooling from a signed binary (e.g. python.exe) by importing their dependencies in memory.