Offensive Security Tool: PingRAT
Reading Time: 2 Minutes
PingRAT
PingRAT by umutcamliyurt, is a tool designed to covertly transmit Command and Control (C2) traffic through firewalls by using ICMP (Internet Control Message Protocol) payloads. It hides its C2 communication within the data portion of ICMP packets. Since ICMP packets are typically allowed through firewalls and often overlooked by security systems, this method allows PingRAT to bypass firewall restrictions and evade detection. It can help penetration testers during security assessments, by simulate sophisticated attack techniques and evaluate the effectiveness of security defenses.
See Also: A Practical Guide to Hacking Techniques for finding Top Bugs.
The Bug Bounty Hunting Course
Features
- Uses ICMP for Command and Control
- Undetectable by most AV/EDR solutions
- Written in Go
See Also: Offensive Security Tool: CrackQL
Installation:
Download the binaries
or build the binaries and you are ready to go:
$ git clone https://github.com/Nemesis0U/PingRAT.git
$ go build client.go
$ go build server.go
Usage:
Server:
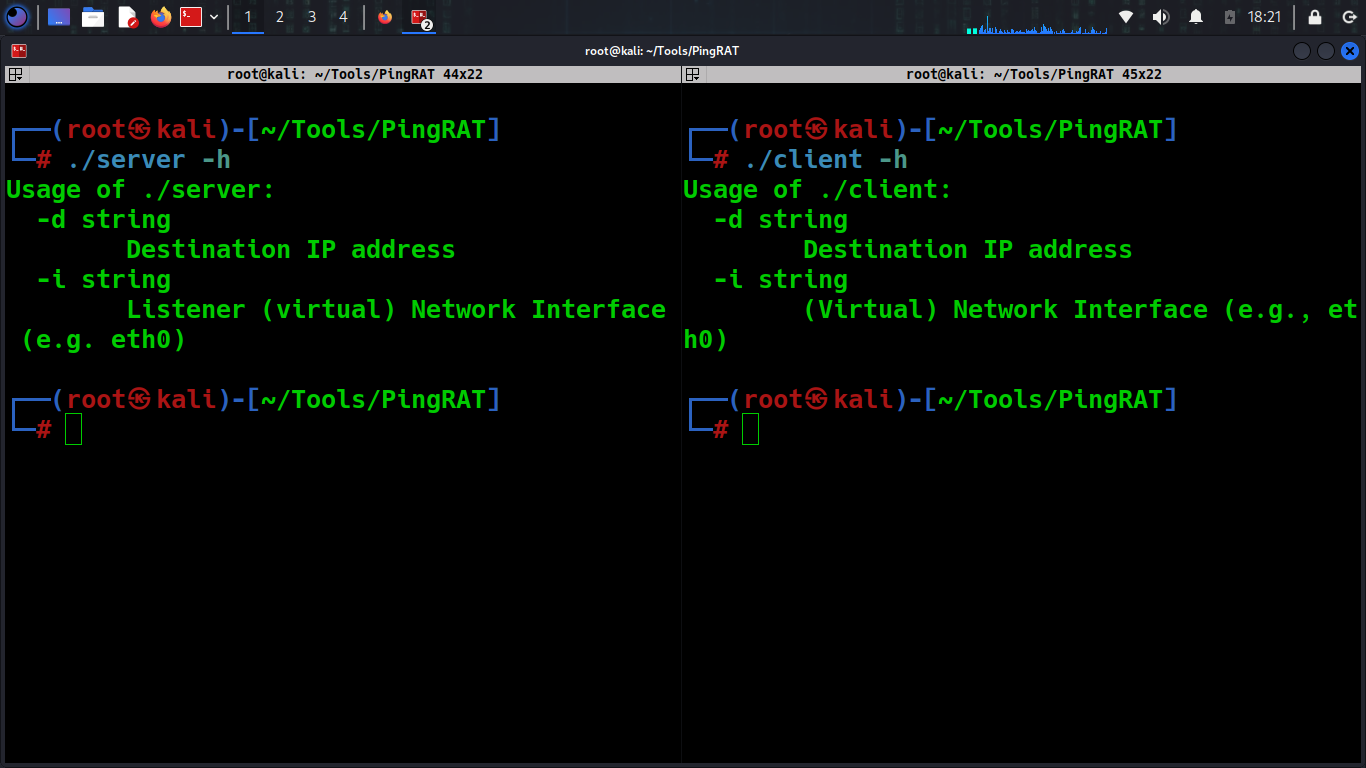
./server -h
Usage of ./server:
-d string
Destination IP address
-i string
Listener (virtual) Network Interface (e.g. eth0)
Client:
./client -h
Usage of ./client:
-d string
Destination IP address
-i string
(Virtual) Network Interface (e.g., eth0)
Clone the repo from here: GitHub Link










