OSINT Tool: SARENKA
Reading Time: 4 Minutes
SARENKA by pawlaczyk is an Open Source Intelligence (OSINT) tool that helps you obtain and understand Attack Surface.
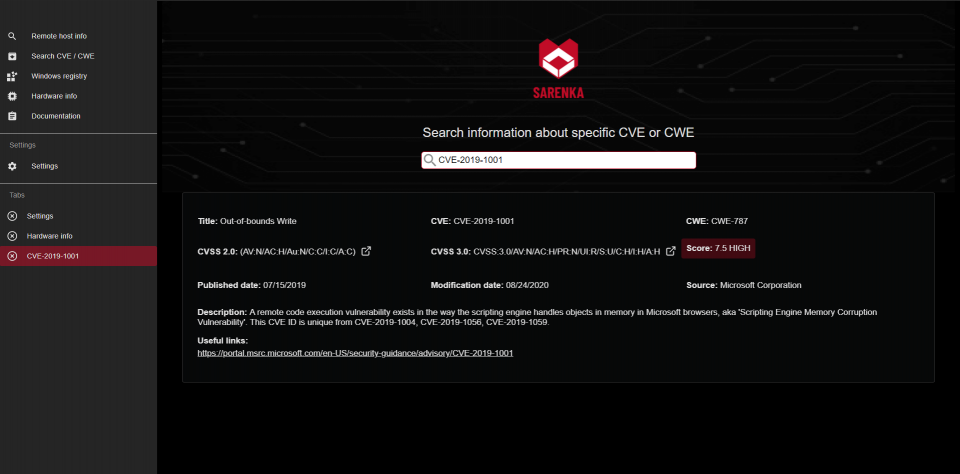
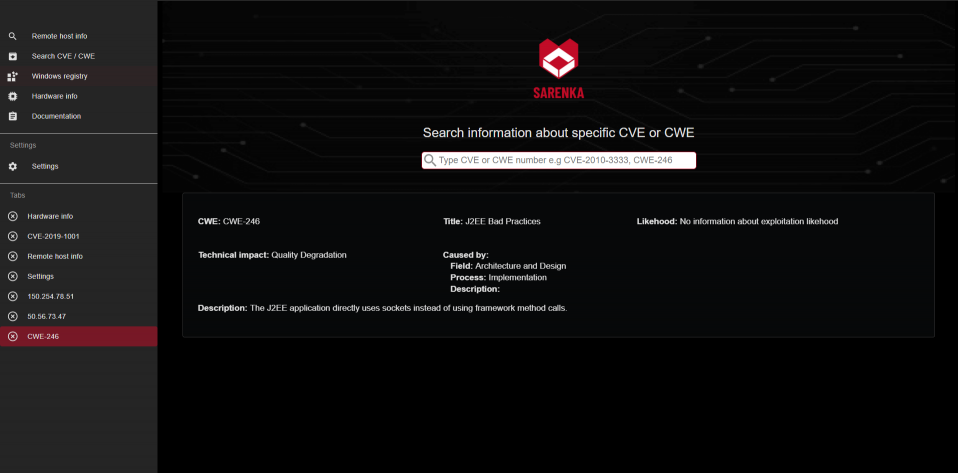
The main goal is gathering information from search engines for Internet-connected devices (https://censys.io/, https://www.shodan.io/). It scraps data about Common Vulnerabilities and Exposures (CVE), Common Weakness Enumeration (CWE) and also has database where CVEs are mapped to CWE.
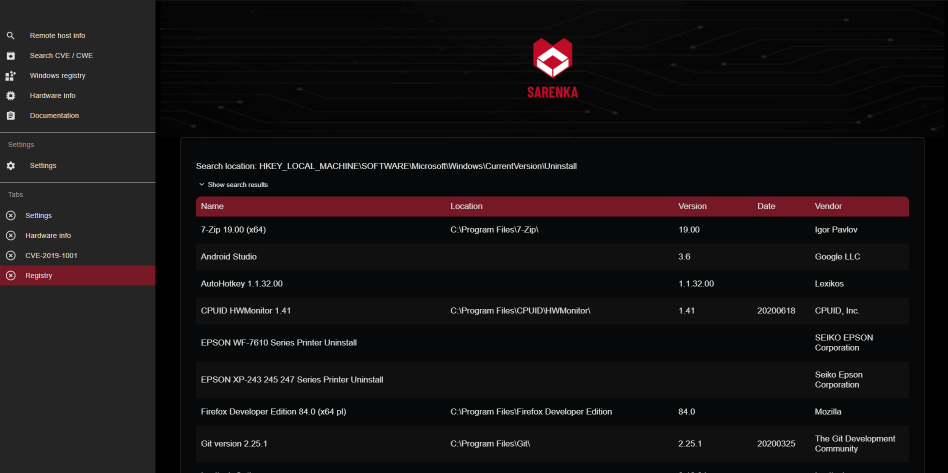
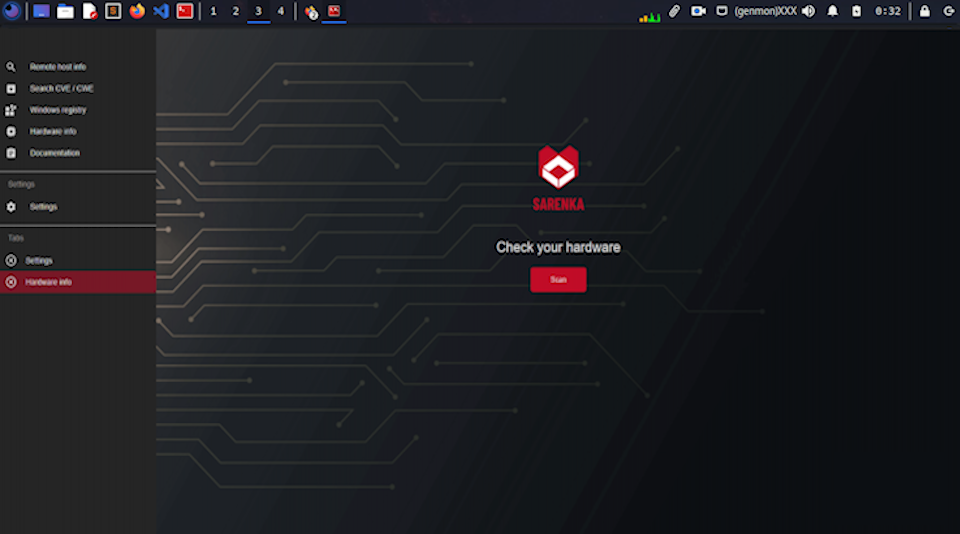
It returns data about the local machine – local installed software (from Windows Registry), local network information (python libraries, popular cmd commands). For now the application has also simple tools like hash calculator, shannon entropy calculator and very simple port scanner.
In Red-Teaming, OSINT has proven to reveal often times, lots of sensitive documents, and information that an organization/person had no idea was there, and it plays a crucial role in your Pentesting process in the early stages that will help you determine and decide the way you will conduct your attack plan.
Features
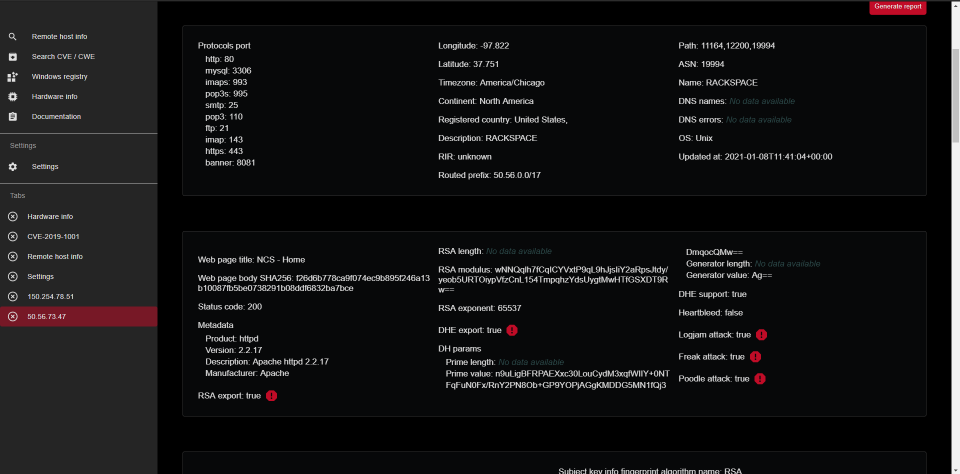
- gets data from https://censys.io/ by ip
- gets data from https://www.shodan.io/ by ip
- gets DNS data
- gets WHOIS data
- banner grabbing
- finds CVEs by CWE
- generates pdf report
You can also:
- calculate hashes based on user string
- calculate shannon entropy based on user string
- check is port open|closed (instead always use nmap if you can – it is slow)
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
Installation
The team has tested it on applications running on Windows 10, Kali Linux and using Python 3.8
SARENKA requires:
Clone repository
$ git clone https://github.com/pawlaczyk/sarenka.git
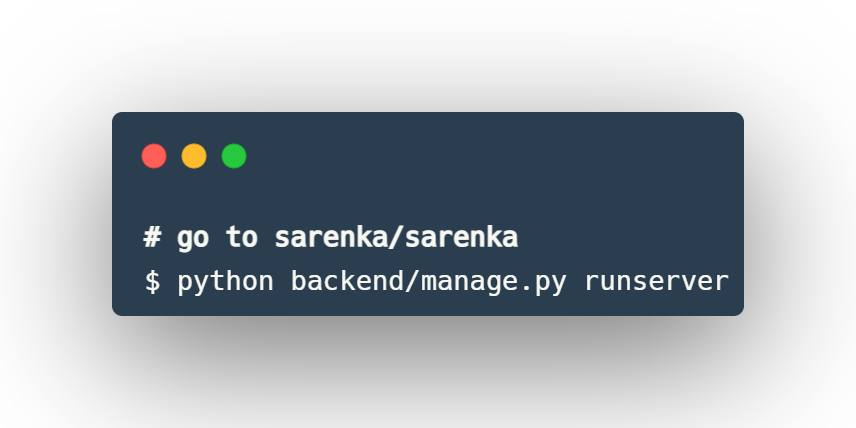
Go to application directory
$ cd ./sarenka
Create venv
$ python3 -m venv env
Activate venv
Powershell
$ ./env/Scripts/Activate.ps1
cmd
$ ./env/Scripts/activate.bat
Install requirements
$ pip3 install -r ./requirements.txt
Build application with sarenka.py script
$ python ./sarenka/sarenka.py
Getting started
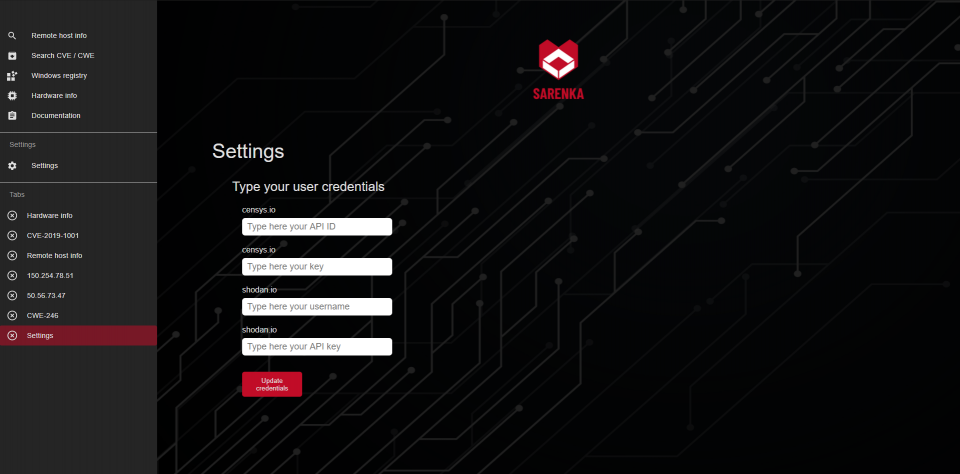
Please create accounts on services:
Application – default http://localhost:8000/
Add user credentials at “Settings”
See Also: Recon Tool: WayMore
Screenshots