Offensive Security Tool: SessionProbe
SessionProbe
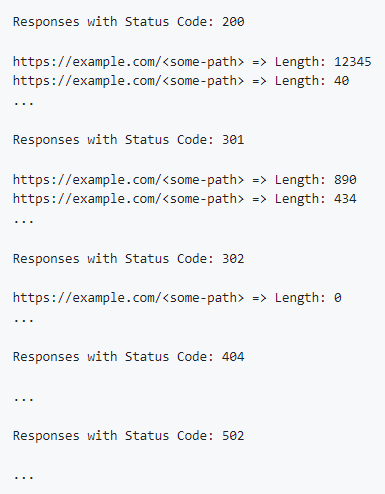
SessionProbe is a multi-threaded pentesting tool designed to assist in evaluating user privileges in web applications. It takes a user’s session token and checks for a list of URLs if access is possible, highlighting potential authorization issues. SessionProbe deduplicates URL lists and provides real-time logging and progress tracking.
SessionProbe is intended to be used with Burp Suite’s “Copy URLs in this host” functionality in the Target tab (available in the free Community Edition).
Note: You may want to change the filter in Burps’s Target tab to include files or images. Otherwise, these URLs would not be copied by “Copy URLs in this host” and would not be tested by SessionProbe.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
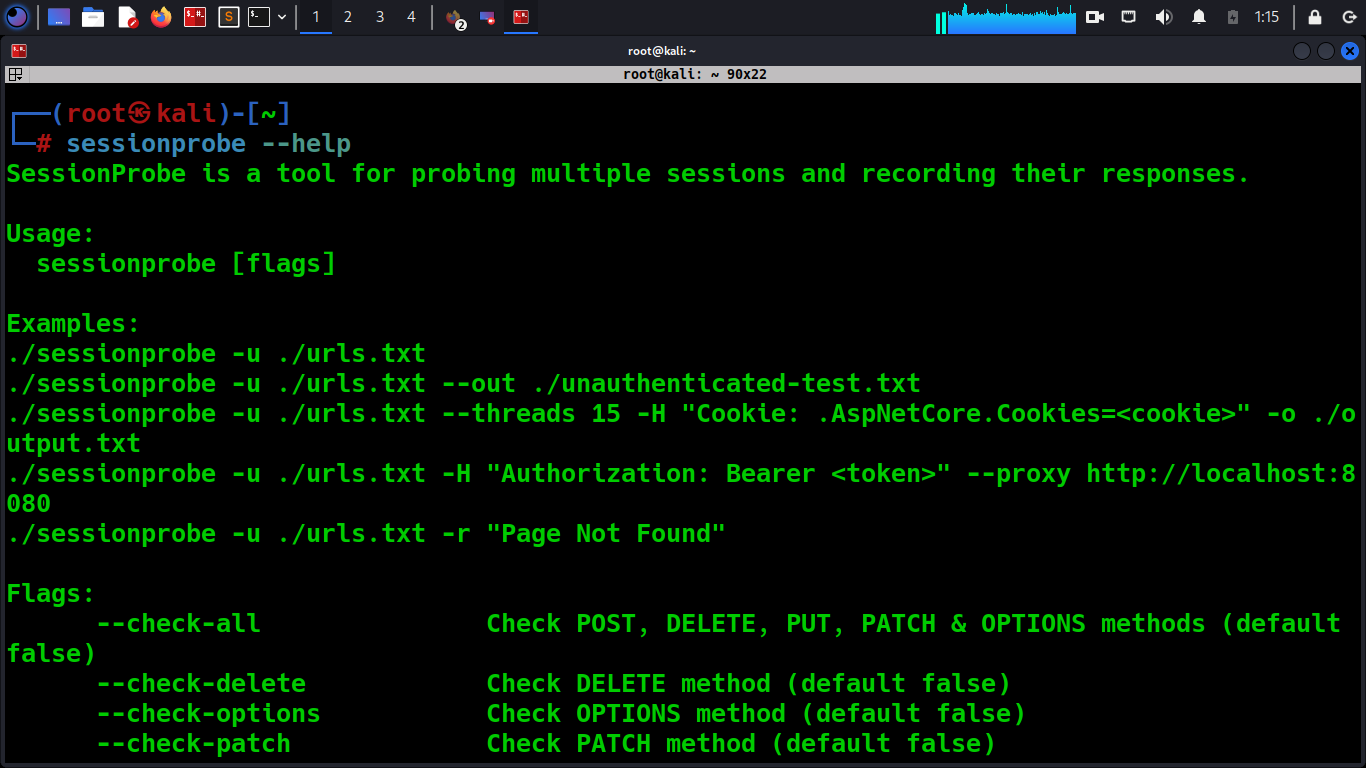
Built-in Help
Help is built-in!
- sessionprobe –help – outputs the help.
How to Use
Usage:
sessionprobe [flags]
Flags:
-u, --urls string file containing the URLs to be checked (required)
-H, --headers string HTTP headers to be used in the requests in the format "Key1:Value1;Key2:Value2;..."
-h, --help help for sessionprobe
--ignore-css ignore URLs ending with .css (default true)
--ignore-js ignore URLs ending with .js (default true)
-o, --out string output file (default "output.txt")
-p, --proxy string proxy URL (default: "")
-r, --filter-regex string exclude HTTP responses using a regex. Responses whose body matches this regex will not be part of the output.
-l, --filter-lengths string exclude HTTP responses by body length. You can specify lengths separated by commas (e.g., "123,456,789").
--skip-verification skip verification of SSL certificates (default false)
-t, --threads int number of threads (default 10)
--check-all Check POST, DELETE, PUT, PATCH & OPTIONS methods (default false)
--check-delete Check DELETE method (default false)
--check-options Check OPTIONS method (default false)
--check-patch Check PATCH method (default false)
--check-post Check POST method (default false)
--check-put Check PUT method (default false)
Examples:
./sessionprobe -u ./urls.txt
./sessionprobe -u ./urls.txt --out ./unauthenticated-test.txt --threads 15
./sessionprobe -u ./urls.txt -H "Cookie: .AspNetCore.Cookies=<cookie>" -o ./output.txt
./sessionprobe -u ./urls.txt -H "Authorization: Bearer <token>" --proxy http://localhost:8080
./sessionprobe -u ./urls.txt -r "Page Not Found"See Also: Recon Tool: CHOMTE.SH
See Also: Offensive Security Tool: Nginxpwner
Run via Docker
- Navigate into the directory where your URLs file is.
- Run the below command:
docker run -it --rm -v "$(pwd):/app/files" --name sessionprobe fw10/sessionprobe [flags]
- Note that we are mounting the current directory in. This means that your URLs file must be in the current directory and your output file will also be in this directory.
- Also remember to have a Burp listener run on all interfaces if you want to use the –proxy option
Setup
- You can simply run this tool from source via go run .
- You can build the tool yourself via go build
- You can build the docker image yourself via docker build . -t fw10/sessionprobe
Run Tests
- To run the tests, run go test or go test -v (for more details)
Releases
- The Releases section contains some already compiled binaries for you so that you might not have to build the tool yourself
- For the Mac releases, your Mac may throw a warning (“cannot be opened because it is from an unidentified developer“)
- To avoid this warning in the first place, you could simply build the app yourself (see Setup)
- Alternatively, you may – at your own risk – bypass this warning following the guidance here
- Afterwards, you can simply run the binary from the command line and provide the required flags
Clone the repo from here: GitHub Link