Offensive Security Tool: Snallygaster
Reading Time: 2 Minutes
Offensive Security Tool: Snallygaster
Snallygaster
Finds file leaks and other security problems on HTTP servers.
What?
Snallygaster by hannob, is a tool that looks for files accessible on web servers that shouldn’t be public and can pose a security risk. Typical examples include publicly accessible git repositories, backup files potentially containing passwords or database dumps. In addition, it contains a few checks for other security vulnerabilities.
As an introduction to these kinds of issues you may want to watch this talk:
⦿ Attacking with HTTP Requests
See the TESTS.md file for an overview of all tests and links to further information about the issues.
See Also: Microsoft, Google Clouds Hijacked for Gobs of Phishing
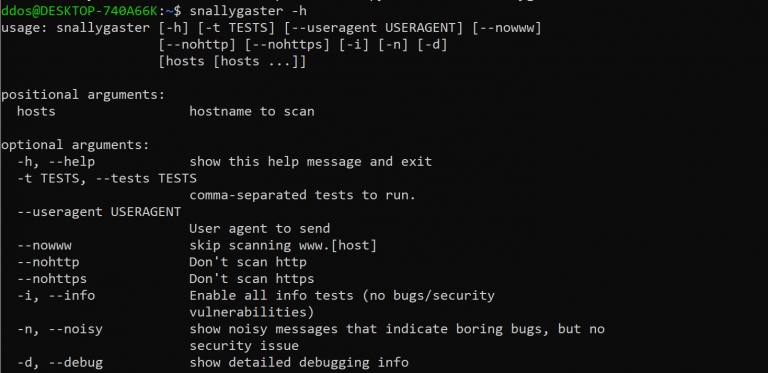
Some Features:
⦿ Select a random user agent to send and scan remote host. this will allow to bypass user-agent block list.
⦿ Skip scanning www.[host] option.
⦿ Don’t scan http it will be possible to crawl one protocol in case that the same web content available on the encrypted version.
⦿ Don’t scan https this to avoid scanning https.
⦿ Enable all info tests (no bugs/security vulnerabilities)
⦿ Show noisy messages that indicate boring bugs, but no security issue.
⦿ Produce JSON output
See Also: Hacking Stories: Xbox Underground
Install
snallygaster is available via pypi:
pip3 install snallygaster
It’s a simple python 3 script, so you can just download the file “snallygaster” and execute it. Dependencies are urllib3, beautifulsoup4 and dnspython. In Debian- or Ubuntu-based distributions you can install them via:
apt install python3-dnspython python3-urllib3 python3-bs4
Distribution Packages
Some Linux and BSD systems have snallygaster packaged:
⦿ Gentoo
⦿ NetBSD
⦿ Arch Linux (git version)
Author
snallygaster is developed and maintained by Hanno Böck.
See Also: Offensive Security Tool: Skipfish