Recon Tool: spoof_checker
Reading Time: 2 Minutes
SPF/DMARC Spoofing & Subdomain Takeover Checker/strong>
spoof_checker, developed by taygun08, is a tool designed for red teamers, penetration testers, and security engineers to identify misconfigurations in email authentication mechanisms and check for subdomain takeover vulnerabilities. It provides both granular analysis and scalable bulk-checking features for domain enumeration tasks.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
Features
- Analyzes SPF (Sender Policy Framework) records for common misconfigurations
- Evaluates DMARC (Domain-based Message Authentication, Reporting & Conformance) policies
- Detects potential spoofing vulnerabilities like:
- Missing or improperly configured SPF/DMARC records
- Overly permissive SPF policies (e.g., “+all” or “?all”)
- Insecure DMARC policy qualifiers
- SPF record loops and excessive DNS lookups
- Checks for subdomain takeover vulnerabilities using known fingerprints
- Multiple output formats (text and JSON)
- Process individual domains or bulk check from a file
- Interactive mode for checking domains one by one
- Save results to an output file
- Concurrent processing for faster bulk scanning
Installation
You can install this tool using Go:
go install github.com/taygun08/spoof_checker@latest
Or clone the repository and install locally:
git clone https://github.com/taygun08/spoof_checker.git
cd spoof_checker
go build -o spoof_check
See Also: Offensive Security Tool: Nucleimonst3r
Usage
Check a single domain
./spoof_check -domain example.com
Process multiple domains from a file
Create a text file with one domain per line. Lines starting with # will be treated as comments and skipped.
./spoof_check -input domains.txt
Interactive mode
./spoof_check -interactive
Output options
JSON output
./spoof_check -domain example.com -json
Save results to a file
./spoof_check -domain example.com -output results.txt
JSON output saved to a file
./spoof_check -domain example.com -json -output results.json
Bulk processing with JSON output
./spoof_check -input domains.txt -json -output results.json
Bulk processing with TXT output
./spoof_check -input domains.txt -output results.txt
Bulk processing subdomain takeover check with json output
./spoof_check -input domains.txt -subtakeover -json -output results.txt
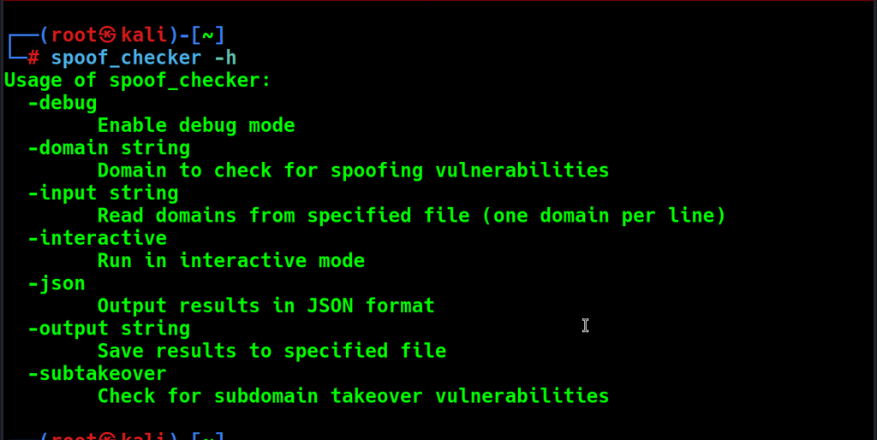
Command-Line Options
Option | Description |
-domain | Specify a single domain to check |
-input | Specify a file containing a list of domains to check |
-output | Save results to the specified file |
-json | Output results in JSON format |
-interactive | Run in interactive mode |
-subtakeover | Check for subdomain takeover vulnerabilities (untested) |
-debug | Debug Mode |
Issue Codes
The tool identifies several types of issues with the following codes:
| Code | Title | Severity |
|---|---|---|
| 0 | Non-existent domain | Low |
| 1 | No SPF record exists | High |
| 2 | SPF “all” mechanism is missing or set to “?all” | High |
| 3 | SPF “+all” mechanism set | Very High |
| 4 | SPF “~all” (SoftFail) mechanism set | Medium |
| 5 | SPF has too many lookups for receiver validation | Medium |
| 6 | No SPF sub-domain record exists | Medium |
| 7 | No DMARC record exists | High |
| 8 | Insecure DMARC policy ‘p’ qualifier | High |
| 9 | Insecure DMARC sub-domain ‘p’ qualifier | High |
| 10 | Partial DMARC coverage | Medium |
| 11 | DNS Timeout during Scan | Low |
| 12 | Trivial SPF recurse loop | Medium |
Example Output
Text format:
--- Checking domain: example.com ---
SPF Record: v=spf1 include:_spf.example.com ~all
DMARC Record: v=DMARC1; p=none; rua=mailto:[email protected]
Found the following issues:
Code 4: SPF "~all" (SoftFail) ```bash
```echanism set
Severity: Medium
Detail: The "all" mechanism at the end of the end of an SPF record tells receivers how to treat unauthorised (i.e. spoofed) emails - the "~all" setting tells receivers to 'SoftFail' (i.e. quarantine) emails that fail SPF authentication. In practice however, many email filters only slightly raise the total spam score and accept 'SoftFailed' (i.e. spoofed) emails.
Code 8: Insecure DMARC policy 'p' qualifier
Severity: High
Detail: The DMARC policy 'p' qualifier is "none". If the DMARC policy is neither "reject" nor "quarantine", spoofed emails utilising an attack technique known as SPF-bypass are likely to be accepted.
--- Subdomain Takeover Check ---
Not vulnerable to subdomain takeover.
CNAME: example.com
--- End of report ---
JSON format:
{
"domain": "example.com",
"spf_record": "v=spf1 include:_spf.example.com ~all",
"dmarc_record": "v=DMARC1; p=none; rua=mailto:[email protected]",
"issues": [
{
"code": 4,
"title": "SPF \"~all\" (SoftFail) mechanism set",
"detail": "The \"all\" mechanism at the end of the end of an SPF record tells receivers how to treat unauthorised (i.e. spoofed) emails - the \"~all\" setting tells receivers to 'SoftFail' (i.e. quarantine) emails that fail SPF authentication. In practice however, many email filters only slightly raise the total spam score and accept 'SoftFailed' (i.e. spoofed) emails.",
"severity": "Medium"
},
{
"code": 8,
"title": "Insecure DMARC policy 'p' qualifier",
"detail": "The DMARC policy 'p' qualifier is \"none\". If the DMARC policy is neither \"reject\" nor \"quarantine\", spoofed emails utilising an attack technique known as SPF-bypass are likely to be accepted.",
"severity": "High"
}
],
"success": true,
"subdomain_takeover": {
"domain": "example.com",
"vulnerable": false,
"cname_record": "example.com"
}
},
Clone the repo from here: GitHub Link









