Offensive Security Tool: SSRFPwned

Reading Time: 3 Minutes
Description
SSRFPwned is written by Chris “SaintDruG” Abou-Chabke from Black Hat Ethical Hacking and is a Penetration Testing and Bug Bounty Offensive Security Tool that automates the process of testing for Server Side Request Forgery (SSRF) vulnerabilities. SSRF is a type of vulnerability that allows attackers to make unauthorized requests to internal resources of a server by manipulating user-supplied input. SSRFPwned automates the testing of thousands of URLs to identify potential SSRF vulnerabilities. It does this by injecting payloads into the query parameters of each URL and checking the response code to determine if a vulnerability exists. The Payloads are custom ones with multiple attack vectors, and you could also add more wordlists in case you want to even test for more, as it will copy the wordlist, merge them then start the attack.
See Also: So you want to be a hacker?
Offensive Security and Ethical Hacking Course
What Makes SSRFPwned Unique
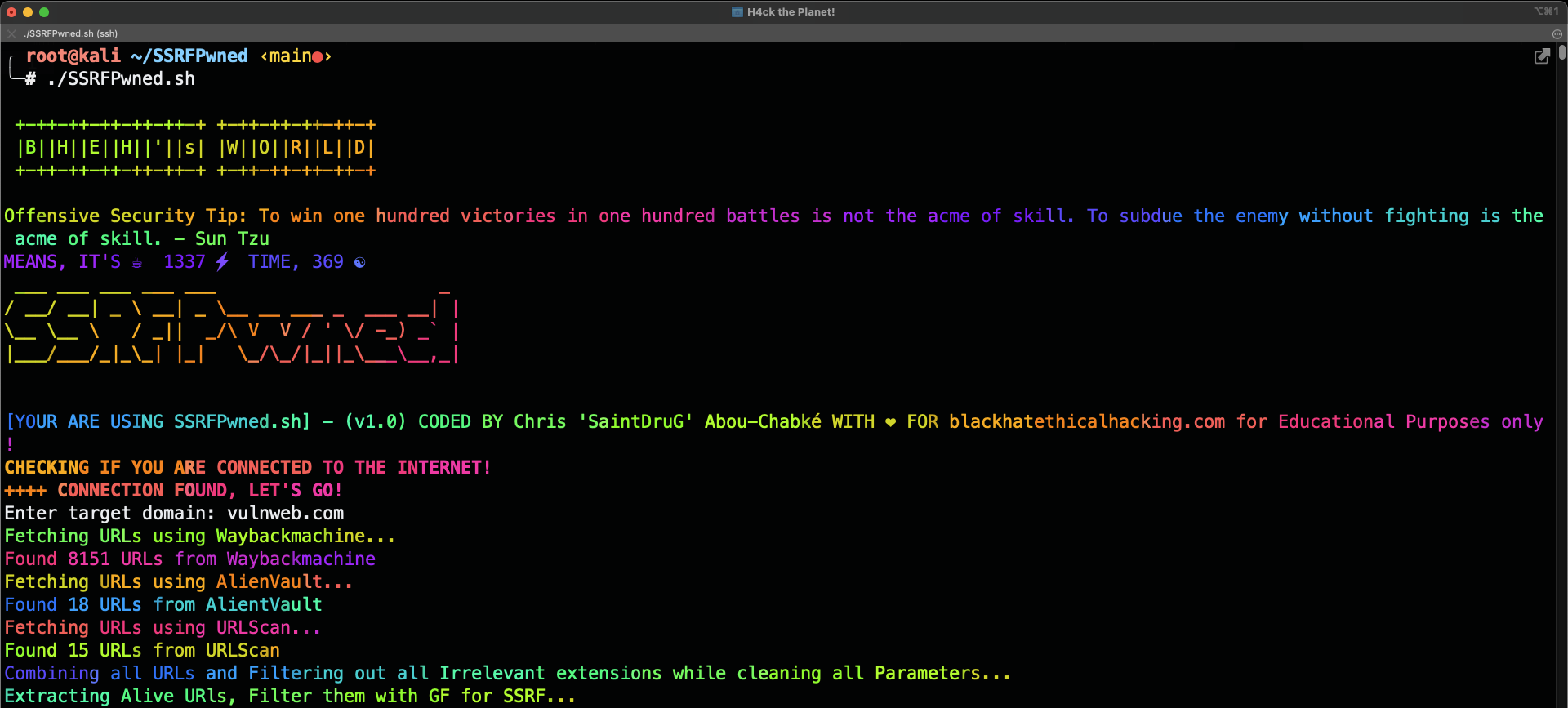
SSRFPwned is unique because it combines multiple sources for URL discovery, including the Wayback Machine, URLScan and AlienVault. The tool is also highly customizable, allowing users to add their own payloads for testing specific types of SSRF vulnerabilities. Additionally, the tool is designed to be efficient and scalable, allowing users to test thousands of URLs at once. It is also special because the way it filters the URLs based on using GF to specifically filter out with Regex only the ones that matches the SSRF Pattern, but also cleaning the parameters from values so it can then inject it there. The way it checks also if it is vulnerable or not, checks also for reflected traces of the payload in the response and if it has 200 code to give the result.
See Also: Offensive Security Tool: PhoneSploit Pro
See Also: Malware Analysis Tool: retoolkit
The Flow and Methodology
- Discovery – The tool begins by discovering URLs to test for SSRF vulnerabilities. It does this by using multiple sources including Wayback Machine, AlienVault and URLScan.
- Filtering – The tool filters out URLs that are not relevant for testing SSRF vulnerabilities, such as image files or CSS files.
- It also greps using GF the patterns with Regex that matches the SSRF model and cleans the values of the parameters.
- Payload Injection – The tool then injects a variety of custom payloads into the query parameters of each URL. The payloads are designed to test for specific types of SSRF vulnerabilities.
- Testing – The tool tests each URL and payload combination by sending a request to the URL with the injected payload. It then checks the response code to determine if a vulnerability exists.
- Reporting – The tool generates a report of vulnerable URLs and the payloads that were successful in exploiting the vulnerability.
Features
- Automatic testing of thousands of URLs for SSRF vulnerabilities
- Supports multiple sources for URL discovery
- Automatic payload injection into query parameters of each URL
- Customizable payload list for testing specific types of SSRF vulnerabilities
- Supports HTTP and HTTPS protocols
- Provides detailed output including vulnerable URLs and payload used
- Saves results in an easily readable format for further analysis
Requirements
- waybackurls: This tool can be installed by running go install github.com/tomnomnom/waybackurls@latest
- cURL: This tool is commonly pre-installed on Kali Linux and Ubuntu, but can be installed by running apt-get install curl on Ubuntu or brew install curl on MacOS
- httpx: is a fast and multi-purpose HTTP toolkit that allows running multiple probes using the retryable http library. To install it: go install -v github.com/projectdiscovery/httpx/cmd/httpx@latest
- lolcat: pip install lolcat for rainbow beauty
- gf: go install -v github.com/tomnomnom/gf@latest
Installation
git clone https://github.com/blackhatethicalhacking/SSRFPwned.git
cd SSRFPwned
chmod +x SSRFPwned.sh
./SSRFPwned.sh
Screenshot
Compatibility
This tool has been tested on Kali Linux, Ubuntu and MacOS.
Disclaimer
This tool is provided for educational and research purposes only. The author of this project is no way responsible for any misuse of this tool. We use it to test under NDA agreements with clients and their consents for pentesting purposes and we never encourage to misuse or take responsibility for any damage caused!
Clone the repo from here: GitHub Link