Offensive Security Tool: Upload_Bypass
Reading Time: 2 Minutes
Upload Bypass
Upload Bypass by sAjibuu is a simple tool designed to assist penetration testers and bug hunters in testing file upload mechanisms. It leverages various bug bounty techniques to simplify the process of identifying and exploiting vulnerabilities, ensuring thorough assessments of web applications.
See Also: A Practical Guide to Hacking Techniques for finding Top Bugs.
The Bug Bounty Hunting Course
Features
Detection Mode:
Suitable for real-world penetration tests. This mode will upload harmless files and will not attempt to exploit the target.
New – If a destination folder for the uploaded files is provided, the program will determine if the uploaded sample file is rendered. For example, if you chose PHP, the program will try to determine if an echo command is executed and rendered successfully, if it does, it’ll suggest to enter an interactive shell.
Exploitation Mode:
Suitable when you want to exploit the target and upload an interactive Web-shell (If a destination upload directory is provided), it will upload the file with a random UUID, so it will be harder for fuzzers to guess.
Anti-Malware mode:
Suitable for an Anti-Malware presence test. Upload an Eicar(Anti-Malware test file) to the system, and if the user specifies the location of the uploaded file, the program will check if the file uploaded successfully and exists in the system in order to determine if an Anti-Malware is present on the system.
Customization
Check out config.py in lib directory, you can add new extensions, mimetypes, magicbytes, configure your HTTP method and etc’…
To add a new module, simply add a function with your desired functionality to modules.py then add the function by name into the list “active_modules” in config.py
To add a new file extension, add a sample.{ext} file to assets/sample_files, then add the extension and its mimetype/magic bytes to config.py
See Also: Offensive Security Tool: Pypykatz
Download:
git clone https://github.com/sAjibuu/Upload_Bypass.git
Installation:
pip install -r requirements.txt
Installation from a Docker Hub
sudo docker pull sajibuu/upload_bypass
Installation from a local docker file
sudo docker build -t sajibuu/upload_bypass .
Docker Usage examples
Example without proxy:
sudo docker run -v $(pwd)/request:/Upload_Bypass/{your_request_file} -it sajibuu/upload_bypass -r request -s 'file was uploaded successfully' -E php -e
Example with proxy:
Make sure to listen to port 8080 on all interfaces!
sudo docker run -v $(pwd)/request:/Upload_Bypass/{your_request_file} -it sajibuu/upload_bypass -r request -s 'file was uploaded successfully' -E php -e -p http://{docker_interface_IP}:8080
Limitations:
The tool will not function properly with the following:
- CAPTCHA implementation is in place.
- A requirement for a CSRF token for each request.
- A destination folder is provided for the uploaded files, but, the uploaded files are saved with a GUID (Globally Unique Identifier) instead of their actual filenames, the program won’t be able to work with it.
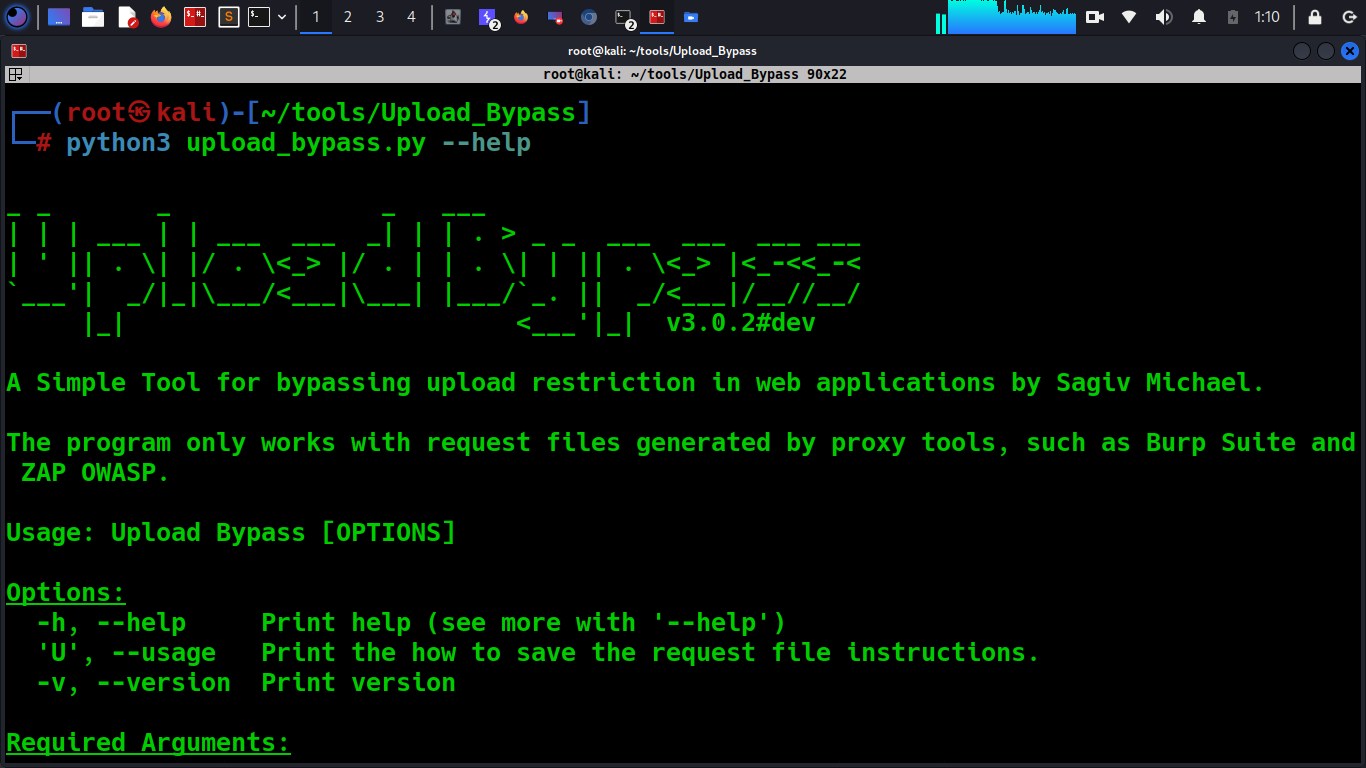
Usage:
Attention
The program only works with request files generated by proxy tools, such as Burp Suite and ZAP OWASP.
Before saving the request file from the proxy you are using, for example, Burp Suite, replace the the following parameter values with their coressponding markers:
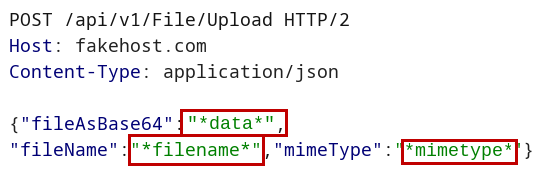
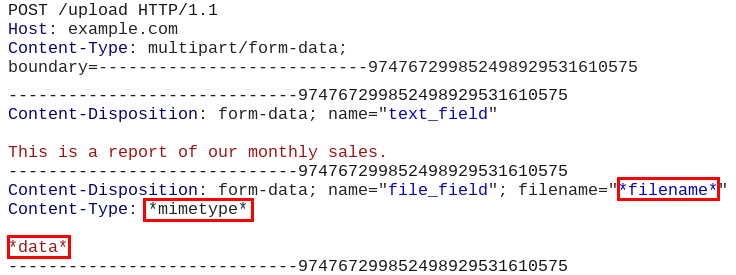
File content: *data*
Example: Replace the image binary data with the string *data*
Filename: *filename*
Example: Replace the filename including its extension with the string *filename*
Content-Type header: *mimetype*.
Example: Replace the file’s content-type (mimetype) with the string *mimetype*
Example 1:
How it should look like in a JSON request:
Example 2:
How it should look like in a multi-part data request:
User Options
Examples
Detection mode
python upload_bypass.py -r test -s 'File uploaded successfully' -E php -D /uploads --burp --detect
Exploitation mode
python upload_bypass.py -r test -s 'File uploaded successfully' -E php -D /uploads --burp --exploit
Anti_Malware mode
python upload_bypass.py -r test -s 'File uploaded successfully' -E php -D /uploads --burp --anti_malware
Disclaimer
Please note that the use of Upload Bypass and any actions taken with it are solely at your own risk. The tool is provided for educational and testing purposes only. The developer of Upload Bypass is not responsible for any misuse, damage, or illegal activities caused by its usage.
Clone the repo from here: GitHub Link