Offensive Security Tool: WEF (WiFi Exploitation Framework)

Reading Time: 2 Minutes
WEF (WiFi Exploitation Framework)
This tool is written by D3Ext, a fully offensive framework for the 802.11 networks and protocols with different types of attacks for WPA/WPA2 and WEP, automated hash cracking, Bluetooth hacking, and much more. Performing Wireless Assessment is crucial in your Pentesting when it comes to the Red Team. You have to be able to demonstrate, how an attacker can go under the hood, and manipulate a network card so it can send other commands to perform deeper packet man-in-the-middle attack techniques.
Tested and supported in Kali Linux, Parrot OS, Arch Linux and Ubuntu.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
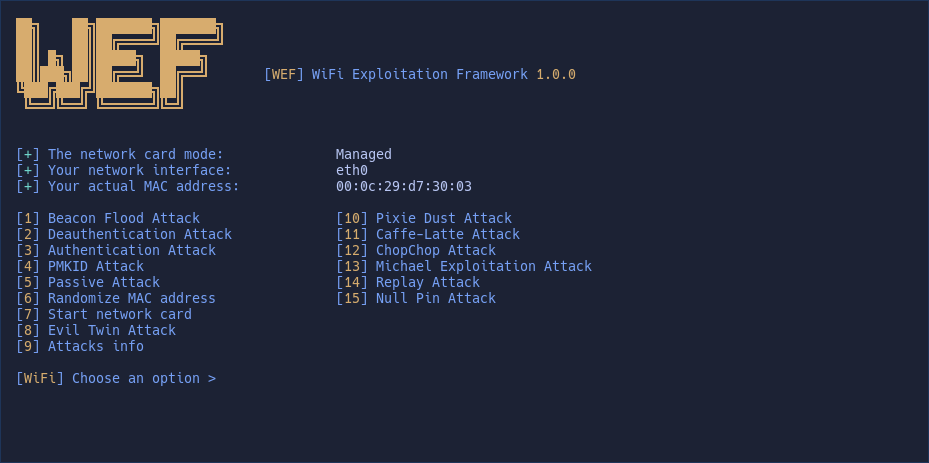
SUPPORTED ATTACKS:
☑️ Deauthentication Attack
☑️ Authentication Attack
☑️ Beacon Flood Attack
☑️ PMKID Attack
☑️ EvilTwin Attack
☑️ Passive/Stealthy Attack
☑️ Pixie Dust Attack
☑️ Null Pin Attack
☑️ Chopchop Attack
☑️ Replay Attack
☑️ Michael Exploitation Attack
☑️ Caffe-Latte Attack
☑️ Jamming, Reading and Writing Bluetooth connections
☑️ GPS Spoofing with HackRF
FEATURES:
☑️ Log generator
☑️ WPA/WPA2, WPS and WEP Attacks
☑️ Auto handshake cracking
☑️ Multiple templates for EvilTwin attack
☑️ Check monitor mode and it status
☑️ 2Ghz and 5Ghz attacks
☑️ Custom wordlist selector
☑️ Auto detect requirements
☑️ Bluetooth support (Jamming, Reading, Writing)
Trending: OSINT Tool: Blackbird
USAGE:
Common usage of the framework.
wef -i wlan0 # Your interface name might be different
or
wef --interface wlan0
Once the application is running, type help to view more functions and useful info.
However I’ll do a post on my blog about WEF and wifi hacking from zero to hero
REQUIREMENTS:
Don’t install them manually, WEF takes care of that if you don’t already have them.
aircrack-ng
reaver
mdk4
macchanger
hashcat
xterm
hcxtools
pixiewps
python3
btlejack
crackle
php
hostadp
dnsmasq
INSTALLATION:
Checkout the Wiki
DEMO:
Demo on a Parrot OS with Kitty terminal
Clone the repo from here: GitHub Link