Offensive Security Tool: ZipExec

Reading Time: 2 Minutes
Offensive Security Tool: ZipExec
ZipExec
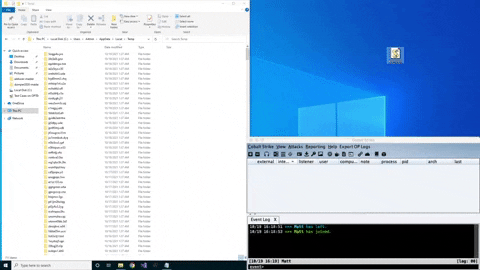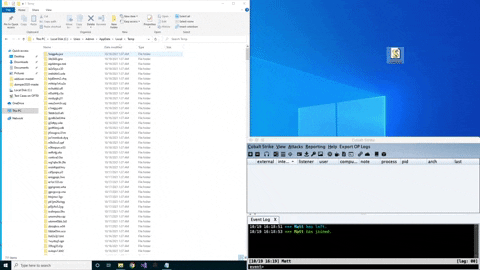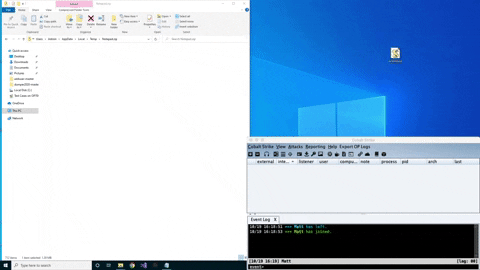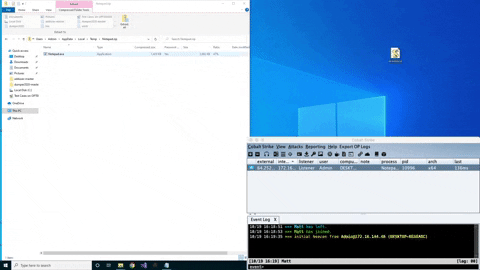
ZipExec by Tylous, is a Proof-of-Concept (POC) tool to wrap binary-based tools into a password-protected zip file. This zip file is then base64 encoded into a string that is rebuilt on disk. This encoded string is then loaded into a JScript file that when executed, would rebuild the password-protected zip file on disk and execute it. This is done programmatically by using COM objects to access the GUI-based functions in Windows via the generated JScript loader, executing the loader inside the password-protected zip without having to unzip it first. By password protecting the zip file, it protects the binary from EDRs and disk-based or anti-malware scanning mechanisms.
As you can see, this is a unique technique to execute binaries from a password protected zip helping the digital forensics team, and offensive security team to use in their field.
See Also: All Windows versions impacted by new LPE zero-day vulnerability
Installation
The first step as always is to clone the repo. Before you compile ZipExec you’ll need to install the dependencies. To install them, run the following commands:
go get github.com/yeka/zip
Then build it
go build ZipExec.go
or
go get github.com/Tylous/ZipExec
See Also: Hacking stories – Operation Troy – How researchers linked the cyberattacks
Help
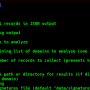
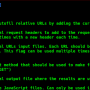
./ZipExec -h
__________.__ ___________
\____ /|__|_____\_ _____/__ ___ ____ ____
/ / | \____ \| __)_\ \/ // __ \_/ ___\
/ /_ | | |_> > \> <\ ___/\ \___
/_______ \|__| __/_______ /__/\_ \\___ >\___ >
\/ |__| \/ \/ \/ \/
(@Tyl0us)
Usage of ./ZipExec:
-I string
Path to the file containing binary to zip.
-O string
Name of output file (e.g. loader.js)
-sandbox
Enables sandbox evasion using IsDomainedJoined.
See Also: Offensive Security Tool: Dalfox